Improving source-in-the-middle continuous-variable quantum key distribution using a heralded hybrid linear amplifier
Lei-Xin Wu(伍磊鑫), Yan-Yan Feng(冯艳艳), and Jian Zhou(周健)
College of Computer and Information Engineering,Central South University of Forestry and Technology,Changsha 410004,China
Keywords: hybrid linear amplifier,source-in-the-middle distribution,finite-size analysis
1.Introduction
Quantum key distribution (QKD)[1–5]enables the establishment of a secure key between two users (Alice and Bob)[6–9]in the presence of an eavesdropper,[10–14]which allows the two communicating parties to exchange and produce a random secure key to encrypt and decode messages.[15–19]Theoretically, the no-cloning theorem and uncertainty principle ensure the absolute security of quantum communication.[20,21]However, due to the interference of noise in the detector and channel, the eavesdroppers could acquire the information by attacking the quantum channel.For Alice and Bob, the signal leakage can be reduced by lowering the channel loss.[22]QKD is divided into discrete variable quantum key distribution (DVQKD) and continuous variable quantum key distribution (CVQKD).DVQKD uses single photons for quantum transport and has a long transmission distance.However, its ability to resist interference is poor.CVQKD offers the benefit of using commercially available telecom components and is more compatible with wave-length-division multiplexing(WDM).[23]However,it is not widely used, as the CVQKD protocol is fragile and cannot maintain high reconciliation efficiency in long distance transfer.As a result, increasing the transmission distance of CVQKD is imminent.[24–26]
Many new CVQKD distribution protocols have been proposed to overcome the disadvantages of transmission distance,such as the protocol involving placing the source between two users.[27–29]Unlike the traditional protocol (the Gaussian entanglement created by Alice, who is a trusted party to Bob),this protocol places the Gaussian entangled source in the middle of Alice and Bob,and uses an untrusted third party(likely Eve)to generate a secure string of keys.Direct reconciliation and reverse reconciliation are interchangeable in the new protocol.The results show that the coherent-state protocol outperforms the squeezed-state protocol in terms of noise resistance (3 dB).Also, the source-in-the-middle protocol, using the coherent state,has higher transmission efficiency and noise immunity than the traditional CVQKD protocol.[28]As a result, there is plenty of room for advancement via alternative means.Discrete modulation was adopted in Ref.[29] to enhance the protocol performance for source-in-the-middle distribution; the results are attractive, but the effective transmission distribution is always very limited under high noise.[29]
Moreover, adding the heralded hybrid linear amplifier(HLA),which is made of a tunable parameter heralded noiseless linear amplifier(NLA)and an optimal deterministic linear amplifier(DLA),to the end provides another way to extend the CVQKD transmission distance.[30–32]The HLA abandons determinism and employs the probabilistic approach to achieve high-fidelity cloning that surpasses the Gaussian unclonable limit.[30]On the one hand, the NLA can amplify the coherent state amplitude without introducing additional noise.[31]On the other hand, the DLA transforms the coherent state in a deterministic manner.Moreover, by tuning the parameters,the coherent state can be amplified with low noise and a high chance of success.[30–32]Besides,finite-size analysis can help to improve the security of quantum communication.[33–35]Although the finite-size analysis has a negative effect on the key rate, the simulation will be closer to the reality.Before the protocol begins, Alice and Bob have agreed on some of the parameters and reconciliation.The parameters are estimated to improve the security of the quantum channel.[33]
In this paper, we introduce the HLA at the output of the channel to enhance the source-in-the-middle distribution protocol.Additionally,finite-size analysis is used to enhance the security of the protocol and bring the simulation closer to reality.The HLA addresses the transmission distance issues with the source-in-the-middle distribution.It is possible to transmit over long distances while keeping the key rate high.In the simulation section,we apply the protocol to a specific system,in which the impact of noise and each HLA parameter on this system will be investigated.
This paper is organized as follows:we describe the modified protocol in Section 2,the key rate of the modified protocol will be calculated in Section 3, the simulation is displayed in Section 4,and the concluding remarks are given in Section 5.
2.Entanglement-in-the-middle distribution with the HLA amplifier
The modified protocol is displayed in Fig.1.A Gaussian entanglement source develops in the middle of Alice and Bob.The HLA is compensated at the output of Bob to address the transmission distance shortcomings of original protocols.Under the Gaussian collective attack of Eve, Alice and Bob use an unreliable third party to help them generate a secure key.We conclude from Ref.[28]that there is no impact on the protocol’s security.
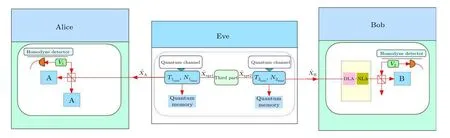
Fig.1.A scheme of the entanglement-in-the-middle protocol with the HLA is detailed.An entanglement source is generated by a third party and transmitted to Alice and Bob by a quantum channel.The HLA amplifier is inserted at the output of Bob.
The two modes of EPR entangled pairs are created by third parties, where ˆXepr1is sent to Alice and ˆXepr2is sent to Bob,after traveling through the channel,
The protocol is strongly symmetric when the entanglement source is positioned in the middle of Alice and Bob[15]
Notably,the protocol switches to a conventional CVQKD protocol atT=1,which allows Alice to generate entangled states and send them securely to Bob.Eve launches a collective Gaussian attack on the channel in the interim.
The HLA is demonstrated to scale the coherent state securely.It makes sense to use the HLA to enhance the sourcein-the-middle protocol.The HLA is composed of a tunable NLA and a DLA,where the NLA is competent to the coherent state togwith probability 1/g2, and DLA is capable of expanding the coherent state by a factor ofG.While a higherGincreases the likelihood of success, it also brings more noise.This straightforward and efficient method accomplishes coherent state amplification close to the quantum noise limit.The original protocol will be improved with the HLA.
The HLA introduces additional noise
When the EPR entangled pair passes through the HLA, the signal is expanded to
The amplitude and phase are both increased to
The HLA can convert the parameter variance factorλ, channel transmittanceT, and noiseNinto a new parameter variance factorς, channel transmittanceη, and noiseNg.They are related as follows:
The HLA takes a probabilistic approach to expand coherent states beyond the Gaussian unclonable limit,resulting in highfidelity predictive cloning.The connection between the input and output is
The average values of the signals are amplified to
Since the HLA extends the transmission distance of the quantum and SNR,we intend to use it at Bob’s end to address the shortcomings of the source-in-the-middle distribution.In fact,the HLA is very compatible with the original protocol and can improve its shortcomings,such as its inability to transmit over long distances and its low noise resistance.The modified protocol can be customized according to the actual transportation requirements.We will consider the use of direct reconciliation for homodyne detection and coherent states.Of course,it also involves the reverse reconciliation with heterodyne detection and squeezed states in this protocol.
3.Secure key rate of the modified protocol
The security keys that export the modified protocol will be distributed.To make the simulation more realistic,we take into account the finite size of the protocol.When deriving the key rate, we consider the direct reconciliation for homodyne detection and coherent states.
The secure key rate of the modified protocol is
whereNsignals are exchanged but onlynis used to encode the signals,andm=N −nis used for parameter estimation.Here,S(A:B)expresses the information shared between Alice and Bob,andSQpe(A:E)represents the information eavesdropped by Eve.The∆(n)denotes the part of privacy amplification.
The following formula can be used to conduct the correlation of data between Alice and Bob
where
andbfollows a normal distribution with a centered shape and an unidentified variance.The distribution is
In Eqs.(14) and (15),kandMare determined parameters;thus,these parameters can be estimated.
Now the lower limitkminforkand the upper limitMmaxforMare acquired by
wheremis the number of signals involved in the parameter estimation.According to Eqs.(4)and(5),we can obtain
The symmetry of the intermediate source protocol is not affected when the finite size is considered.
When the HLA is inserted by Bob’s output,it is equivalent to a new EPR state being sent on a new Gaussian channel.Combined with finite-size analysis for parameters, the new EPR parameters ˆς2, the channel transmission rate ˆη2and the extra noiseare provided by
The new variance ˆV2is
Now,the formulae for computingV(ς1),V(ς2),andV(ς3)are given by
When a flawless homodyne detection is run and the detector is free of noise,
Thus,Alice and Bob’s covariance matrix can be found.TheZandIare the Pauli matrices.
Next,the mutual informationS(A:B)between Alice and Bob can be calculated,
The information that Eve stole is
where
in which
λ1.2is obtained from Eq.(23)
where
λ3.4is obtained from Eq.(25)
When performing homodyne detection to coherent states,
The value of the privacy amplification∆(n) is given by the following equation:
Eventually,the secure key rate is derived.
4.Simulation
We concentrate on the nature of the modified protocol in this section.First, we conduct finite-size analysis of the protocol and compare the transmission distances of the original protocol and the protocol with HLA amplifiers.Based on the modified protocol’s superiority in terms of the key rate, we apply it to a practical system.The effects of the system’s critical parameters on the modified protocol are investigated.We investigate the impact of the protocol with the HLA in this section and analyze its finite-size impact.We assume that the protocol performs quantum key distribution in ideal circumstances.Although the key rate that considers the finite size is lower,the simulation results will be closer to reality.The reason for this is that, when the finite size is considered, not all bits are used to encode information,and some of them are used for channel estimation and will be discarded during reconciliation.Security is increased in the finite-size case.The key rate is lower than the conventional protocol when discrete modulation is used with the source-in-the-middle protocol(the reason for this may not be the use of optimal variance, which needs further exploration).Also, the source-in-the-middle protocol using the HLA has a much greater maximum transmission distance than it does.It is advantageous to use the protocol on a real system later.The linear hybrid amplifier has a significant effect on the source-in-the-middle of the key rate.As shown in Fig.2, the key rate of the original protocol with finite-size analysis begins to decline drastically at 12 km,while the modified protocol can still communicate at a high key rate at 95 km.It is clear that the modified protocol offers superior transmission qualities.It demonstrates that the HLA can overcome the drawbacks of the traditional protocol’s short transmission distance,and has strong compatibility with the source-in-themiddle distribution protocol.It shows that the HLA has a very significant influence on the source-in-the-middle distribution protocol.Compared to the unmodified protocol, it increases the quantum safe transmission distance by a factor of nearly seven.The modified protocol is applied to a system.As shown in Figs.3–5,the effects of two critical amplifier parameters,Gandg,as well as extra noiseN,on the protocol’s key rate are investigated.In fact, the transmission distance is sensitive toGandgwithin certain confidence intervals.
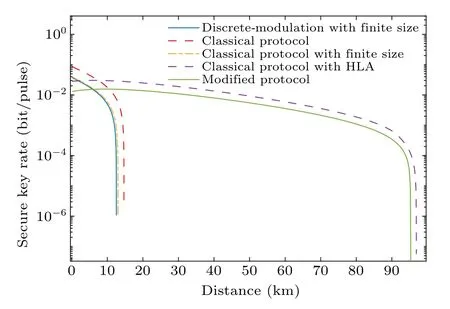
Fig.2.The key rates of the modified and the original protocols with finite size are compared.The original protocol with finite size and discrete modulation with finite size are used as references.
To maximize the key rate in a certain case,we search for an optimalGwithin the legal region.We adjust the other parameters of the system:zQPE/2=6.5,m=n=N/2=108,dimHx=2, ¯Q=10−10.The finite size ofTandNyieldsTminandNmax.The secure key is computed using the method described in Section 2.The relationship between them is roughly understood in Fig.3(a),but it is not intuitive.As a result,we choose the longer distance(60 km,75 km,70 km)to investigate the association between the key rate and distance.If we choose a short distance(likely 10 km),it is meaningless,since the distance is the main factor affecting the key rate.In this case,the key rate is always large,whether or not an amplifier is plugged in.From Fig.3(b),we find that when the transport distance is 65 km,we can compensate the key rate to a higher level by adjustingG= 3.When longer transport distances(65 km, 70 km) are required, a largerGis needed to maintain the communication.Of course, the value ofGdoes not totally compensate for the negative effects of distance,and the key rate constantly drops gradually as the distance increases.Furthermore, when a particular data valueGis reached, the key rate does not change much withG.We can find the optimalGin different systems of quantum communication using a similar method.
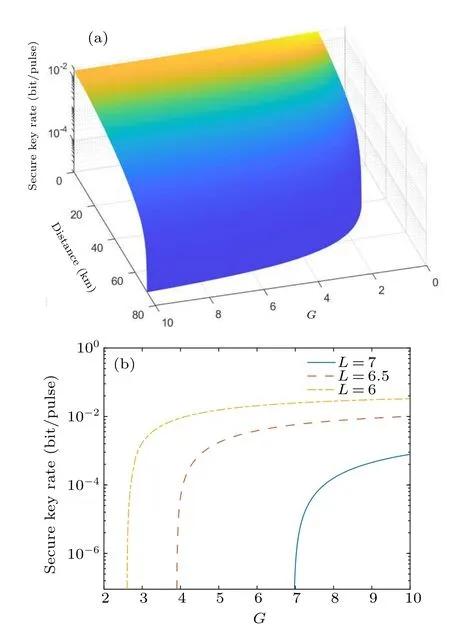
Fig.3.We used three-dimensional surface plots and two-dimensional curve plots to investigate the effect of G on the system.Here, g=2.5,N=0.06 are the other parameters.
Thegis another important parameter of the HLA.The HLA is composed of a DLA and an NLA, whereGis a key parameter of the DLA andgis an important parameter of the NLA.Studying the effect of thegon the system is as important as studyingG.In this system,the same method is used to find the optimalg.By analyzing Figs.4(a)and 4(b),similarly,we can conclude that a largergimproves the performance of the quantum channel, both in terms of the key rate and transmission.The parametergis very effective in the gain interval(2.5–3).Based on the desired length of the quantum channel,we can select the optimal parameters to achieve stable communication.
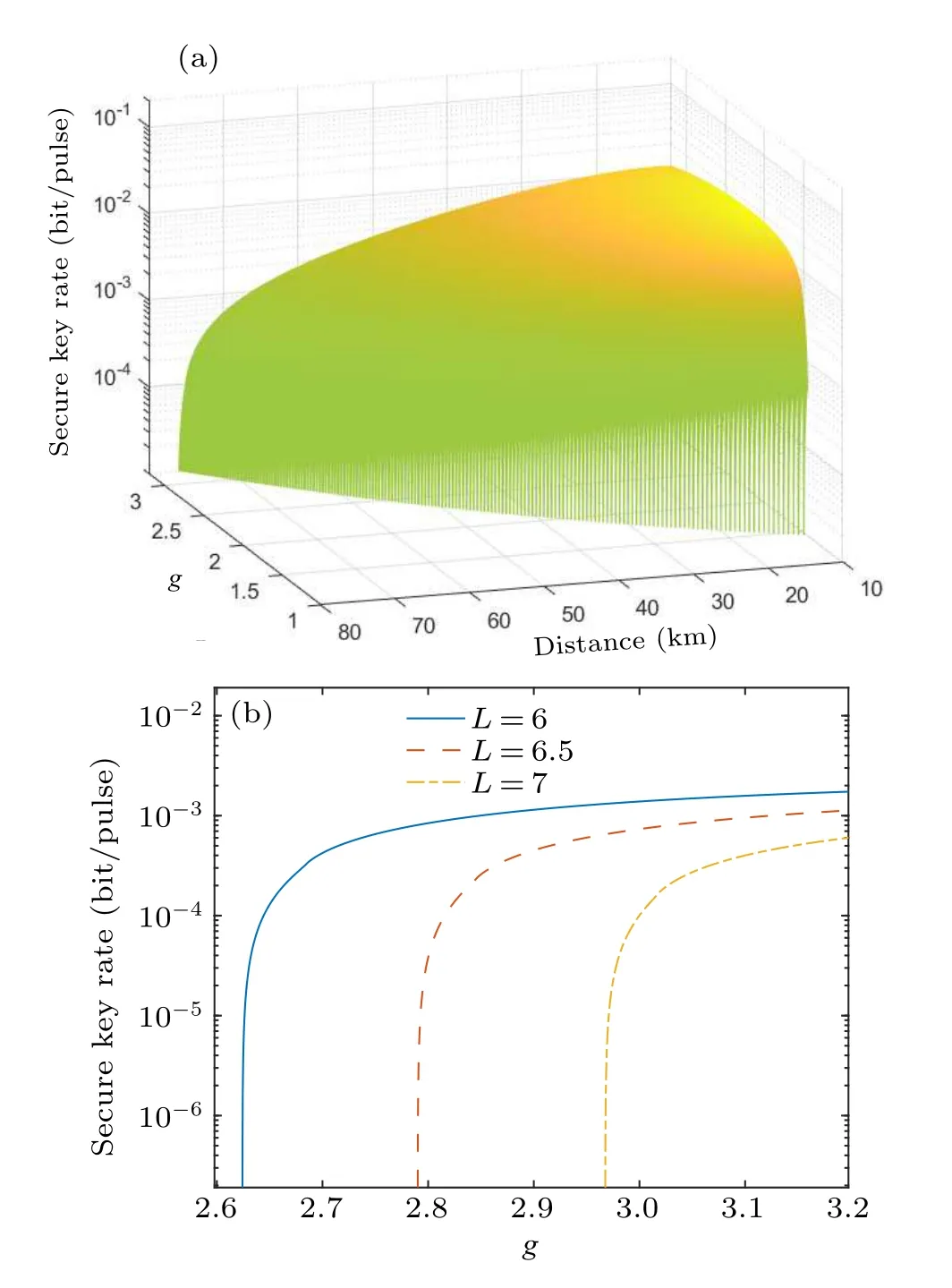
Fig.4.The impact of g on the system is examined using two-dimensional curve plots and three-dimensional surface plots.The other parameters are G=2,N=0.06.
The ability to resist noise is tested in this system withg=3,G=8.In fact,the noise is dynamic rather than static in the quantum channel.Normal communication must be possible,even in the presence of maximum noise,to keep the channel secure; therefore, the effect of noise on the system must be investigated.The noise interval of the general channel is between 0.01 and 0.1.The additional noise is antagonistic to the channel in Fig.5(a).In Fig.5(b),if the noise upper bound is 0.04 dB,the system can achieve 90km communication,and when the noise rises to 0.08 dB, the distance of secure communication drops to 80 km.
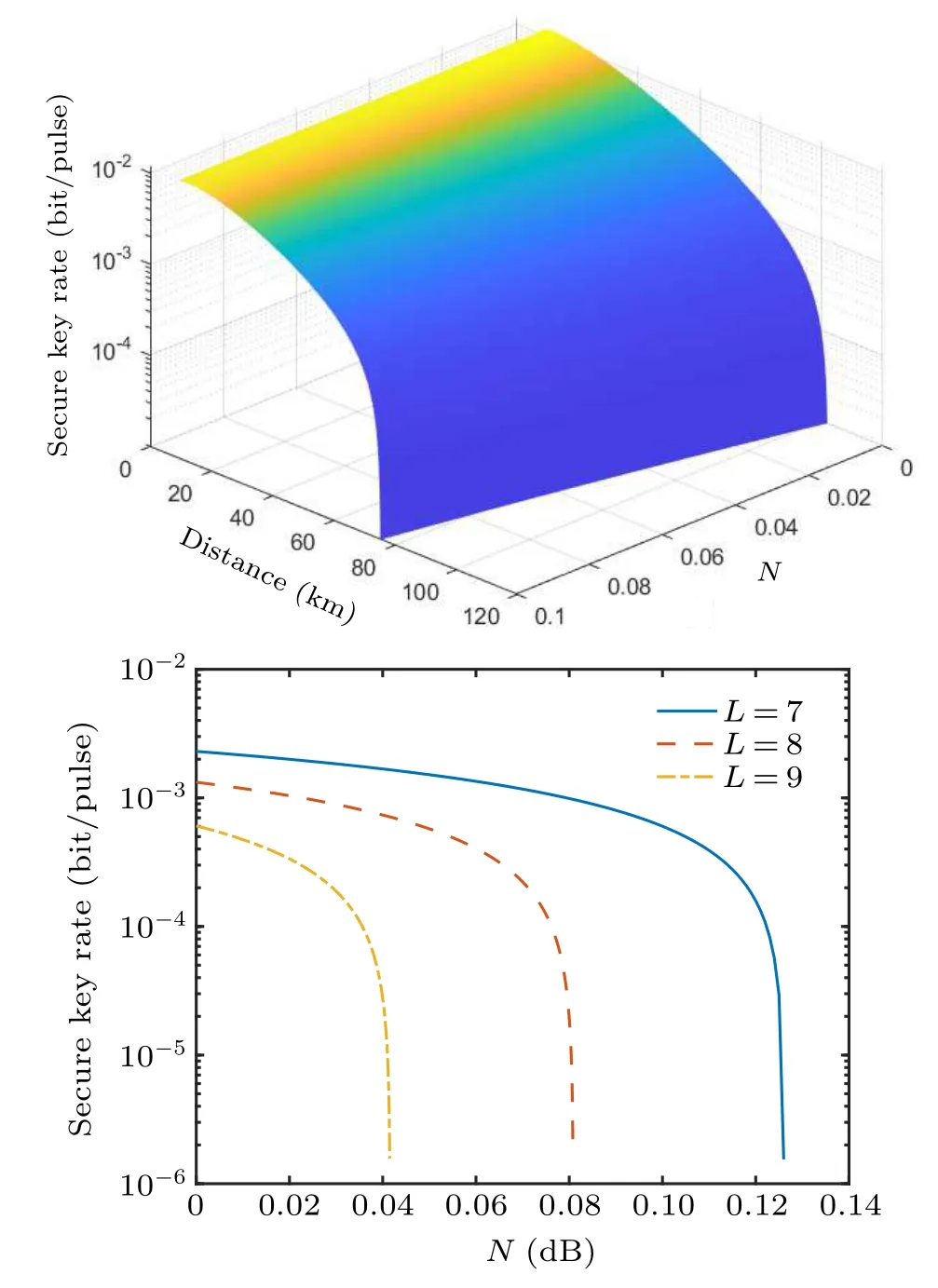
Fig.5.How noise relates to the distance(a)and system key rate(b).
Even in 0.12 dB noise, it can still maintain a key rate of more than 104(bit/pulse)in 70 km.The modified protocol has a high resistance to noise,and can be widely used in practice.
5.Conclusion
In this paper, we use the HLA to improve the sourcein-the-middle distribution protocol.The shortcomings of the original protocol with regard to transmission distance have been overcome.The finite-size effect of the modified protocol has also been analyzed in the protocol.Compared with the original protocol, the modified protocol has better transmission,and can achieve 95 km transmission in ideal conditions.We specifically discuss the effect of the gain coefficientG,gon the key rate between the good simulation results of the protocol after inserting the HLA.To some extent, a largerGorgcan improve the key rate for a given distance.However,the negative effect of distance on the key rate cannot be fully compensated,and the increases in the key rate withG,gis not significant up to a certain value.Also, the effect of noise on the modified protocol is discussed.The simulation results show that the modified protocol can transmit over long distances of 70 km under the noise conditions of 0.12 dB.It is excellent and broadens the application range of CVQKD significantly.In practical applications,we adjust the optimalGandgto apply HLA to different Gaussian channels to maximize the key rate and distance.
Acknowledgments
Project supported by the National Natural Science Foundation of China (Grant No.62201620), the Outstanding Youth Program of Education Department of Hunan (Grant No.21B0228), Changsha Municipal Natural Science Foundation (Grant No.kq2202293), Hunan Students’ Platform for innovation and entrepreneurship training program (Grant No.S202210538069), and the Research Fund of Central South University of Forestry and Technology (Grant No.1121001703).
- Chinese Physics B的其它文章
- Interaction solutions and localized waves to the(2+1)-dimensional Hirota–Satsuma–Ito equation with variable coefficient
- Soliton propagation for a coupled Schr¨odinger equation describing Rossby waves
- Angle robust transmitted plasmonic colors with different surroundings utilizing localized surface plasmon resonance
- Rapid stabilization of stochastic quantum systems in a unified framework
- An improved ISR-WV rumor propagation model based on multichannels with time delay and pulse vaccination
- Quantum homomorphic broadcast multi-signature based on homomorphic aggregation