An Optimum Method Research Based on Bit Plane Combination of Digital Image and Fingerprint Watermarking*
, ,
(1.Guangdong Polytechnic Normal University, School of Electronic and Information,Guangzhou 510665,China;2.Xi’an University of Posts & Telecommunication,School of Communication and Information Engineering,Xi’an 710121,China)
1 Introduction
Information hiding technology is an emerging research area which encompasses application such as copyright protection for digital media, watermarking, fingerprinting, steganography, and data embedding[1]. In the past literature on watermarking, it is observed that bit plane method is one of the recommended methods of watermarking in spatial domain. This method is characterized by spread spectrum and is blind while watermark retrieval[2]. Optimal implementation of this method maximizes the fidelity and robustness against different attacks. This method is based on the fact that the least significant bit plane of the image does not contain visually significant information. Therefore it can be easily replaced with watermark bits without affecting the quality of original image[3-4]. However the survival of the watermark is an open issue and two main drawbacks of inserting watermark in least significant and most significant bits are:
1)If watermark is inserted in least significant bit planes, then the watermark may not survive against coding, channel noise, mild filtering or random bit-flipping.
2)On the other hand, if the watermark is embedded in most significant bit plane, watermark survives but image quality is degraded.
Therefore, to get optimal results, in terms of fidelity, robustness, and high embedding capacity, a new bit plane modification method is proposed in this paper.
To overcome above problems, we propose the novel method for image watermarking. Proposed method differs in two different ways than the earlier technique of bit plane watermarking[5-6]. Firstly, to prove the ownership or identify the owner, most effective digital signature watermark(as fingerprint data) is embedded instead of pseudorandom watermark. Secondly, instead of LSB, a previous bit to LSB is identified for watermark embedding to avoid the degradation of image and to survive the watermark after different general attacks like various Conditional compression.
2 Proposed Watermarking Algorithm
Without significant loss of generality, we shall focus on watermarking still images with 256 gray levels of size 512 × 512 pixels. To trade off between the invisibility and robustness of the watermark, the high-energy sub-band (LL4) is not used. Furthermore, the coefficients in high frequency subbands (LH1 , HL1 and HH1) are not used since they often contain few energy. In other subbands, we group the coefficients corresponding to the same spatial location together. Figure 1 shows an example of a group with one coefficient from HL4 , 4 coefficients from HL3 , and 16 coefficients from HL2[7-9].
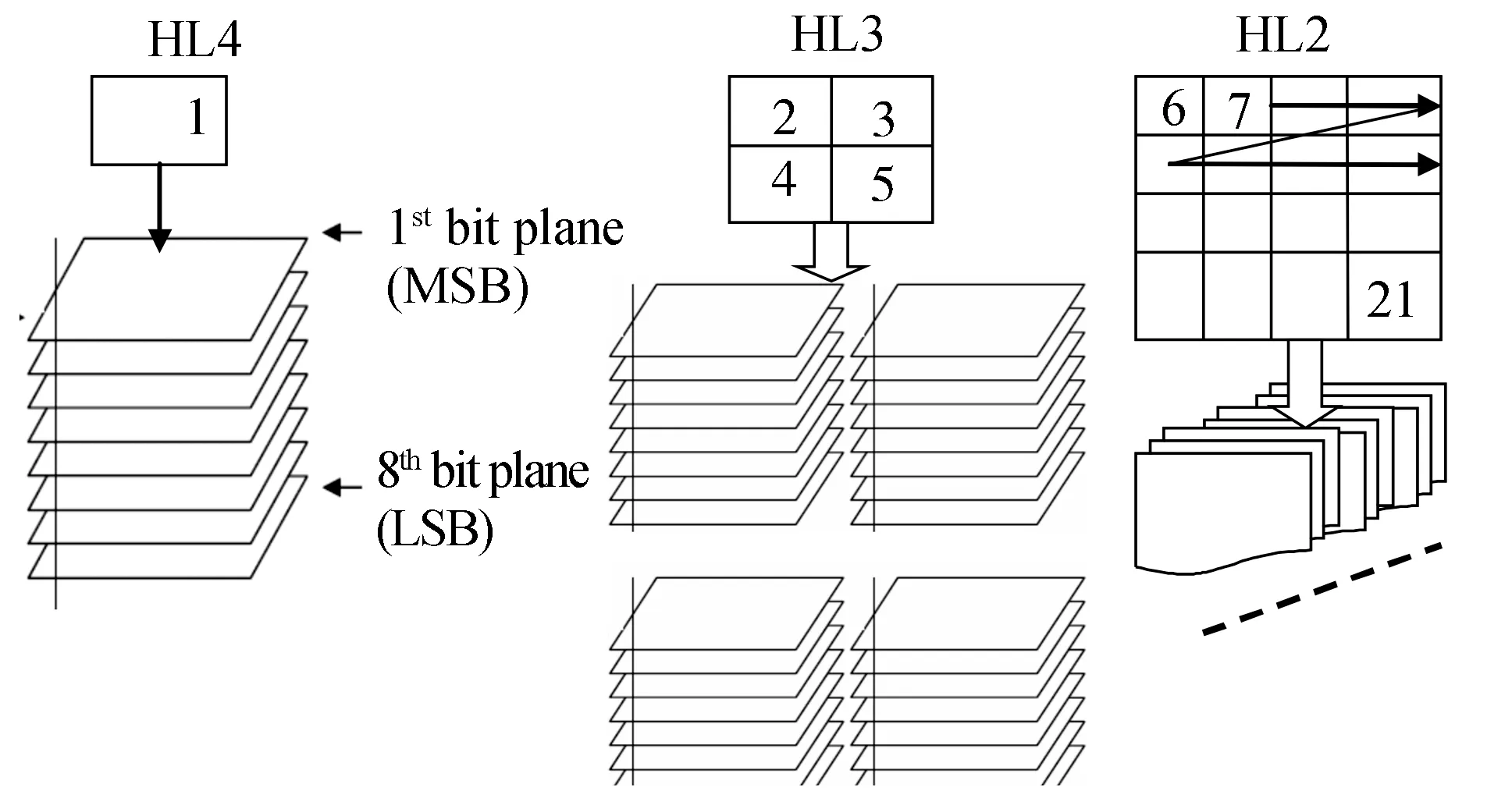
Fig.1 A group of multiwavelet coefficients and Bit plane representation
LetX(m,n) be the grey level image andW(m,n) be the fingerprint image, The grey level image is transformed into the watermarked imageYw(m,n) by DMWT with fingerprint dada embedded. The grey scale imageXis defined as follows:X={X(m,n), m∈{1,...,M}, n∈{1,...N}} , andM,Nare maximum dimensions of an image, whereX(m,n)∈{0,.......,..255} total number of grey levels[10-11]. Step by step algorithm for proposed method is explained below:
Step 1: Decompose the grey level image to bit planes: Grey level image is decomposed in to bit plane image. Each pixel in the image is represented by 8-bits. Therefore the image is decom-posed into eight 1-bit planes, ranging from 8thbit plane for LSB to 1stbit plane for the MSB. The 8thbit plane contains all the lowest order bits in the pixels comprising the image and 1stbit plane contains all the higher order bits as shown in Fig. 1.
The image would be decomposed in to bit planes as follows. A subband coefficient Decomposition of original image into 8-bit planes:
Xl(m,n)=Xb1(m,n)+
Xb2(m,n)+......+Xb8(m,n)
(1)
Similarly, decomposition of fingerprint image into 8-bit planes:
Wb2(m,n)+......+Wb8(m,n)
(2)
Wherelandkindicates number of bit planes of image and ∈{b1,b2,.......b8 }.
Step 2: Replace the significant bit plane of original image with fingerprint bit plane (this is done so as to decide by HVS), which bit planes of the image are good for watermarking[12]. Following set of equations display replacement of 7thbit plane of original image with 1stbit plane of fingerprint data as an example. The same procedure can be adopted for the remaining bit planes of the image.
Yb1(m,n)=Xb1(m,n)
…
Yb7(m,n)=Wb1(m,n)
Yb8(m,n)=Xb8(m,n)
(3)
Combination watermarked image is as follows:
Yw(m,n):Yw(m,n)=Yb1(m,n)+
Yb2(m,n)+...+Yb8(m,n)
(4)
This bit plane watermarked imageYw(m,n) is recomposed in to grey level imageI(m,n) by IDMWT.
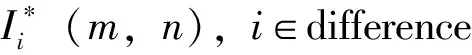
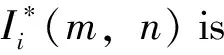
(5)
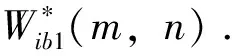
Step5: Computation of CRC: Correlation coefficient between retrieved watermark and original fingerprint is estimated using a standard equation (6)[4]. The estimated correlation coefficients are denoted as CRCi(l,k) . Where,iindicate different attacks,lis taken as 7thand 8thbit planes of original image as selected in step 2 andkdenotes the bit planes of fingerprint watermark from 1 to 8. The quality of watermarked image is observed by HVS. CRC varies between 0 and 1. CRC is defined as given below:
(6)
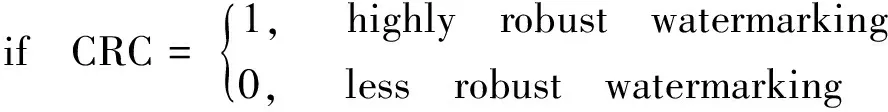
(7)
Step6: Estimation of peak signal to noise ratio (PSNR):PSNRis calculated by using following equation. Capacity of the original image to carry the fingerprint watermark is computed by measuring PSNR, which is defined as follows:
(8)
Mean square error is defined as:
(9)
Step 7: Weighted correlation coefficient computation: Weighted correlation coefficient is defined as follows:
(10)
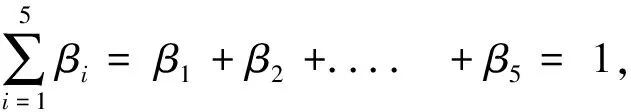
Step 8: Optimization: The above step 7 is repeated by varying the weightings of attacks. The bit plane combination of original image and fingerprint for which, the weighted correlation coefficient is maximum, is selected as the optimized one for the given user requirements. This combination is used for optimized watermarking in terms of robustness and fidelity.
3 Experiment Results and Analysis
Here, we employed Lenna,Baboo,Perppers as test carrier images, which size of the images was fully 512×512, Size of the embedded fingerprint watermarks was 64×64, as figure 2. in the bit planes combination, we use 1stbit plane of fingerprint watermark embedded in 7thbit plane of original image.
The invisibility of the hided image may be measured by histogram statistics charts ,and Peak-value Signal Noise Ratio(PSNR)[13-14]. To the definite information hiding Capacity, the method hold a kind of different hiding efficiency in various compress ratio with JPEG2000[15].
Retrieval of fingerprint image after difference compression attack was showed in finger 3 when the compression factorQ=100,Q=20 ,Q=10 andQ=7, andQ=5,as well asQ=2, respectively. The histogram
statistics charts of theLennaimages composited was showed in figure 4, respectively.

Fig.2 The carrier image and embedded fingerprint images
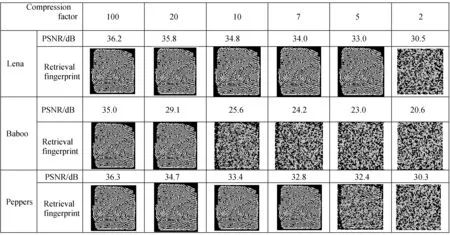
Fig.3 Retrieval of fingerprint image after difference compression attack
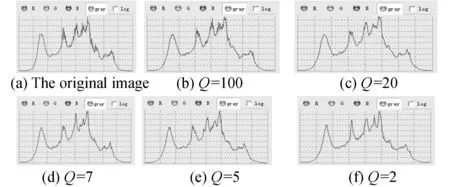
Fig.4 The histogram statistics charts of the Lenna images composited data
From these simulation results, we can find out, where the images composited data possessed better image quality, and the influences to the carrier images was a littler after embedded a fingerprint[8]. Another, the shapes of the histogram statistics charts closed to auxiliary distributions. It shows, the method has better invisibility in various compression ratio, and the highest compression ratio is able to reach the 100∶5 at conditioned embedding images.
4 Conclusions
Based on bit plane decomposition of the original image and the fingerprint image, the paper proposed an effectively information hiding method, which may adaptively embed hidden fingerprint data into wavelet coefficients from low to high frequency sub-band according to in space bit Planes. Experimentation results shows , that The proposed method is found to be useful for authentication and to prove legal ownership, and possesses better tradeoff between invisibility and robustness in various conditional compression.
:
[1] PRAYOTH K, KITTI A,ARTHIT S. A robust image watermarking scheme using multiwavelet tree [C]∥Proceedings of the World Congress on Engineering,London, U.K.July 2-4, 2007.
[2] SUSHMA K, MANESH K. Optimization of bit plane combination for efficient digital image after marking [J].International Journal of Computer Science and Information Security,2009, 4(2): 19-20.
[3] ZhANG L. Combined the information hiding technology with JPEG2000 [D].University of TianJin, 2003: 95-98.
[4] ZHAO H M. Fingerprint system and DSP fast processing technology[J].Research &Progress of Solid State Electronics,2004,24(3):337-342.
[5] TAUBMAN D S, MARCELLIN M W, et al. Image compression foundation, standard and practice of the JPEG2000 [M].Electronics Industrial Publisher, 2004: 415-417.
[6] LI K, ZHANG X P. An image watermarking method integrating with JPEG-2000 still image compression standard[C]∥Electrical and Computer Engineering IEEE CCECE Canadian Conference on, 2003: 2053-2054.
[7] TRAPPE W, WU M, WANG Z J. Anti-collusion fingerprinting for multimedia[J]. IEEE Transactions on Signal Processing, 2008, 53(4):1069-1087.
[8] WANG Z J, WU M, TRAPPE W. Group-oriented fingerprinting for multimedia forensics [J]. EURASIP Journal on Applied Signal Processing, 2004, 14(8): 2142-2162.
[9] WANG Y,LIANG F,XIAO M M. Color image watermarking adaptively in DC coefficients[J]. Acta Scientiarum Naturalium Universitatis Sunyatseni,2010,49(4):43-48.
[10] SWANSON M D, KOHAYASHI M,TEWFIK A. Multimedia data embedding and watermarking technologies[J]. Proc of the IEEE,1998, 86( 6): 1064-1087.
[11] REN J, NADOOSHAN T. A cryptographic watermark embedding technique[C]∥IEEE Asilomar Conf on Signals, Systems and Computers, 2004:382-386.
[12] MAEDER A J, PLANITZ B M. Medical image watermarking for multiple modalities[C]∥34th IEEE Proc on Applied Imagery and Pattern Recognition Workshop, 2005:158-165.
[13] FEI C, KUNDER D,KWONG R H. Analysis and design of secure watermark-based authentication systems[J]. IEEE Trans On Information Forensics and Security, 2006, 1(1):43-55.
[14] PRAYOTH K, KITTI A,ARTHIT S. A new approach for optimization in image watermarking by using genetic algorithms[J]. IEEE Trans on Signal Processing,2005, 53(12):4707-4719.
[15] COX J, KILIAN J, THOMSON F, et al. Secure spread spectrum watermarking for multimedia[J].IEEE Trans on Image Processing,1997, 6(12):1673-1686.

