FPGA implementation and image encryption application of a new PRNG based on a memristive Hopfield neural network with a special activation gradient
Fei Yu(余飞), Zinan Zhang(张梓楠), Hui Shen(沈辉), Yuanyuan Huang(黄园媛),Shuo Cai(蔡烁), and Sichun Du(杜四春)
1School of Computer and Communication Engineering,Changsha University of Science and Technology,Changsha 410114,China
2College of Computer Science and Electronic Engineering,Hunan University,Changsha 410082,China
A memristive Hopfield neural network (MHNN) with a special activation gradient is proposed by adding a suitable memristor to the Hopfield neural network(HNN)with a special activation gradient.The MHNN is simulated and dynamically analyzed, and implemented on FPGA.Then, a new pseudo-random number generator (PRNG) based on MHNN is proposed.The post-processing unit of the PRNG is composed of nonlinear post-processor and XOR calculator, which effectively ensures the randomness of PRNG.The experiments in this paper comply with the IEEE 754-1985 high precision 32-bit floating point standard and are done on the Vivado design tool using a Xilinx XC7Z020CLG400-2 FPGA chip and the Verilog-HDL hardware programming language.The random sequence generated by the PRNG proposed in this paper has passed the NIST SP800-22 test suite and security analysis,proving its randomness and high performance.Finally,an image encryption system based on PRNG is proposed and implemented on FPGA, which proves the value of the image encryption system in the field of data encryption connected to the Internet of Things(IoT).
Keywords: memristive Hopfield neural network(MHNN),pseudo-random number generator(PRNG),FPGA,image encryption,decryption system
1.Introduction
With the rapid development and large-scale application of the Internet of Things(IoT)technology,a number of issues and challenges have emerged, including greater concern over the secure transmission of private information.[1–5]The secure transmission of private information cannot be achieved without the information security system provided by cryptography.Therefore,pseudo-random number generators(PRNGs),as the most prevalent information security systems in cryptography,are receiving increasing attention from researchers.[6,7]Privacy information, as information data, can be encrypted with the random sequence generated by the PRNG during secure transmission and decrypted using the PRNG’s security key to obtain the correct privacy information at the end of the transmission.
Chaotic systems, the most common source of entropy in PRNGs, have randomness and high sensitivity to initial conditions.As a consequence, many chaotic systems possessing abundant dynamical behaviors have been investigated in recent years.[8–13]As a fourth circuit element with natural non-linearity and plasticity, memristors can easily be combined with chaotic system circuits to construct chaotic systems based on memristors.[14–22]Currently, chaotic systems have been used in a wide range of applications such as neural network chaotic systems,[23–32]secure communications,[33–37]synchronization,[38–40]PRNG,[41–44]image encryption,[45–53]and fractional-order chaotic system.[54–56]In recent years,the combination of memristors and neural network chaotic systems to form a memristive neural network model has attracted a lot of research and discussion.[57–59]Xiuet al.[58]proposed a five-dimensional memristive cellular neural network(CNN)hyperchaotic system,and used the chaotic system to synchronise and design a secure communication system, in which a sliding mode control method was used to enhance the robustness to system parameter uncertainties and disturbances.Zhanget al.[59]developed a novel memristive Hopfield neural network(HNN)model with multiple double vortex attractors, in which a non-ideal flux-controlled memristor model was used to replace the synapses of the HNN and applied to pseudo-random generators and image encryption.While the above are memristive neural network chaotic systems and their applications, there has been little research into PRNGs based on memristive neural network chaotic systems and their implementation on FPGA.
In recent years,PRNGs based on neural network chaotic systems have become a hot research topic as a variety of neural network chaotic system structures have been proposed.[60–62]Yanget al.[61]proposed a fractional order HNN chaotic system using the Caputo definition and HNN chaotic system,analyzed the rich dynamical behavior of the system, and implemented the digital circuit of the system based on a DSP platform.Finally, as a source of entropy for PRNG.Tlelo–Cuautleet al.[62]proposed an artificial neural network chaotic system using Hopfield and Hindmarsh–Rose as neurons, which passed the NIST test after implementation on FPGA.Finally, it was applied in image encryption.However,so far there has been no research on the implementation of PRNGs based on the memristive Hopfield neural networks(MHNN) with a special activation gradient on FPGAs, and equally few engineering applications of PRNGs implemented on FPGAs have been reported.
In this work, a PRNG based on an MHNN is proposed,in which the post-processing unit consists of a nonlinear postprocessor and an XOR calculator to improve the randomness of the resulting random sequence.First,the MHNN is discretised for FPGA implementation and a detailed dynamics analysis of the discretised system is carried out.The MHNN is implemented on FPGA and compared with the simulated phase diagram in MATLAB to determine the effectiveness of the implementation.Next,a PRNG based on the MHNN is designed and implemented on the FPGA.The random sequence generated by the PRNG is analysed for security and the randomness of this PRNG is demonstrated.Finally, an image encryption and decryption system based on this PRNG is designed and implemented on FPGA.Through simulation on MATLAB and image security analysis,the value of the PRNG in the field of IoT-related data encryption is determined.
The rest of the paper is presented below.Section 2 analyses the discretized numerical model of the MHNN and implements it on an FPGA.Section 3 describes the structure and flow of the designed PRNG, giving the chip resource utilisation and rate after implementation on FPGA.Section 4 presents security analysis and randomness analysis of the random sequence generated by the PRNG.Section 5 describes the image encryption and decryption system based on the PRNG proposed in this paper and implemented on an FPGA.Finally,Section 6 concludes the full paper.
2.Introduction and FPGA implementation of MHNN with a special activation gradient
Neurons, as the basic building blocks of the brain, are capable of generating abundant dynamical behaviors, and the HNN that it constitutes is an extremely significant nonlinear dynamical model in artificial neurology.The MHNN, constructed by introducing a memristor, has a more complex dynamical behavior that allows the system to offer great flexibility and thus be more suitable for engineering applications.Recently, Baoet al.[28]proposed an HNN with an adjustable gradient of neuron activation,as shown below:

where the state variablesx,y,zdenote the three neurons of the neural network,andris the gradient control parameter of the neuron activation function.Meanwhile, the memristor function of an ideal active flux-controlled memristor with absolute value nonlinearity can be expressed as
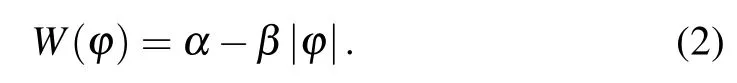
By adding the memristor represented by Eq.(2) to the second equation of the system of Eq.(1),a novel MHNN can be built,which is mathematically modeled as
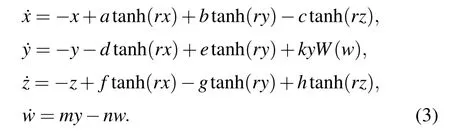
Same as Eq.(1), µ = [x,y,z]Tdenote the neuron state vectors of MHNN.In MHNN,neurons have connection synaptic weights between them, which are represented by the system parametersa,b,c,d,e,f,g,h,respectively.wis the internal dimensionless state variable of the memristor and α,β,k,m,nare the internal parameters of the memristor.tanh(ri)denotes the neuron activation function with an adjustable activation gradient,whereris the activation gradient control parameter.
FPGA, as an efficient chip design tool, is able to transform the system model from software to hardware successfully by using special design algorithms in MATLAB.In this paper,the Runge–Kutta 4th-order(RK4)design algorithm is used to realize the discretization of the system model.The specific algorithm is as follows:
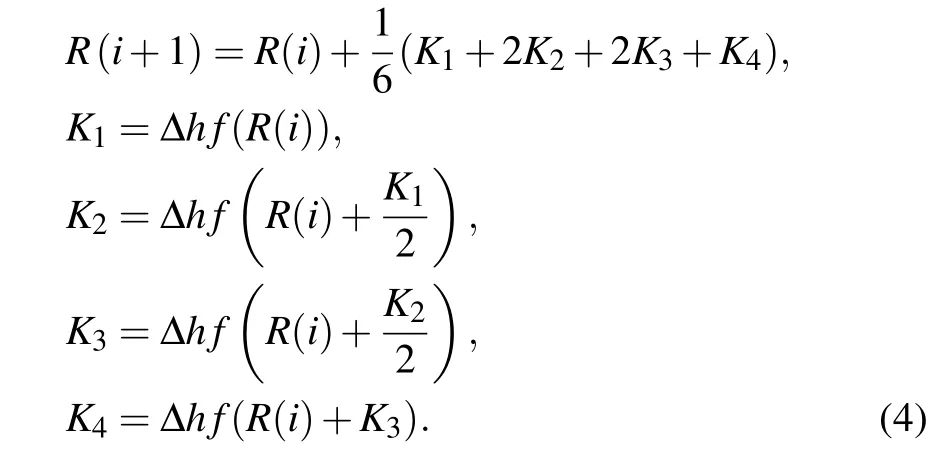
In this paper,the iteration step size is Δh=0.01.R(i)=(x(i),y(i),z(i),w(i)) is the output value of the state variable in thei-th iteration and the input value of the next iterationR(i+1)=(x(i+1),y(i+1),z(i+1),w(i+1)).Similarly,the limitation of the number of logic gates in the FPGA chip poses some challenges to the implementation of the hyperbolic tangent function.Kwanet al.[63]proposed a second-order piecewise function for replacing the hyperbolic tangent function as the activation function, which enables the numerical implementation of the MHNN model.The second-order piecewise function is shown in below:
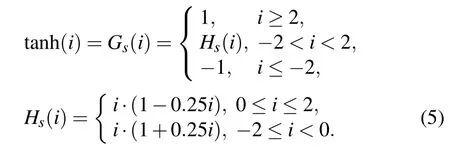
2.1.Simulation and dynamics analysis of system models
In this part, the simulation and analysis of the system are based on the MATLAB platform using the RK4 algorithm of Eq.(4) and the alternative activation function of Eq.(5).In Eq.(3), we set the parameters of the system and the memristor asa=1.5,b=2.9,c=0.7,d=2,e=1.18,f=2.977,g=22,h=0.49,k=0.1,α =1,β =1,m=0.5,n=1.When the initial condition and step size are chosen as(x(0),y(0),z(0),w(0))=(0,1,0,0)and Δh=0.01,respectively.The finite-time Lyapunov exponent spectrum when the activation gradient control parameterr∈(0.8,1.4)is shown in Fig.1.It is obvious from Fig.1.that whenr=1.3,the system has a Lyapunov exponentL1as positive,L2is equal to 0,L3,andL4as negative.At this time,the system is in a chaotic state andL1=0.4496,L2=0.007,L3=−0.472,L4=−0.998.In Eq.(1), the initial condition (x′(0),y′(0),z′(0))=(0,1,0) is selected, and the corresponding Lyapunov exponent is=0.3182,=0.0185,=−0.4349.The Lyapunov index represents the periodic separation rate of the chaotic system,and the separation rate increases with the increase of the Lyapunov index.Therefore,it can be seen fromL1≥that MHNN has a better separation rate.
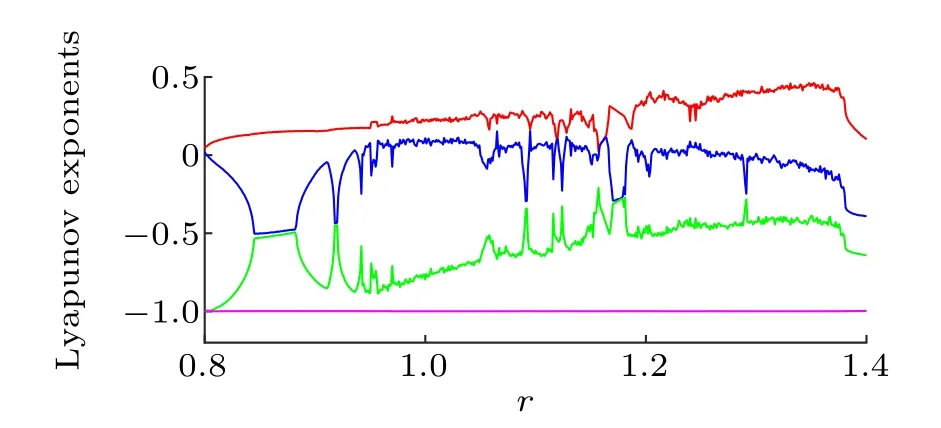
Fig.1.The Lyapunov exponential spectrum of the activated gradient control parameter r ∈(0.8,1.4).
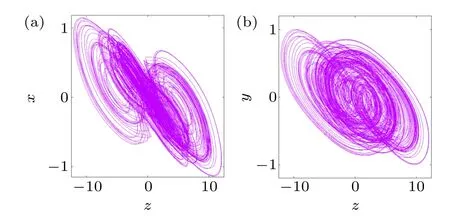
Fig.2.Phase diagram obtained by MHNN in MALTBA platform using the RK4 algorithm and alternative activation functions.(a) Phase diagram projected on z–x plane;(b)phase diagram projected on z–y plane.
In Fig.2,the phase diagram trajectory obtained from the MATLAB numerical simulation can be observed,from which the chaotic behavior inscribed by different types of singular attractors can be revealed.The series diagram of state variablesxandyover time is shown in Fig.3.
Fig.3.Time series diagram of state variables.(a)State variable x; (b)state variable y.
2.2.FPGA-based implementation of MHNN
FPGA design tools have rich hardware resources, such as input and output units, ram, logic units,etc., which provide guarantee for the implementation of MHNN.In this section,the RK4 design algorithm and alternative activation functions are implemented in the vivado design suite using the Verilog HDL language and adders/subtracters,multipliers,and floating-point operators in the IP catalog,and the RK4 design algorithm file is set as a top file.dx, dy, dz, and dwfiles are designed to correspond to the four dimensions of MHNN respectively,and are called by the top file to complete the implementation of FPGA.All operations in this experiment complies with IEEE 754-1985 high precision 32-bit floating point standard.
The flow of the FPGA-based implementation of MHNN is shown in Fig.4.Rst and Clk are the reset signal and clock signal respectively.The step size and initial conditions at the MHNN iteration need to be assigned in the top header file,where Δh=0.01 and(x(0),y(0),z(0),w(0))=(0,1,0,0).The output vector (x(i),y(i),z(i),w(i)) generated by thei-th iteration of the MHNN chaotic oscillator will be input to the floating point to fixed point unit to generate the desired phase value,and finally the corresponding bitstream file will be generated by the digital-to-analog conversion module of the Xilinx XC7Z020CLG400-2 FPGA chip.Meanwhile, the output vectors (x(i),y(i),z(i),w(i)) will be used as the initial values for the next iteration.The end of each iteration of the MHNN chaotic oscillator is controlled by the Clk time control signal.Figure 5 shows the simulation results of MHNN in the Vivado design suite.The bitstream file of the corresponding phase is transmitted to the oscilloscope, and the result is shown in Fig.6.Figures 6(a) and 6(b) show the phase diagram of MHNN chaotic system.Figures 6(c) and 6(d) show the experiment environment of oscilloscope and development board.The simulation results and experimental results of Vivado design suite are consistent with the simulation results of MALTAB software,which show that the MHNN chaotic system based on FPGA is feasible.
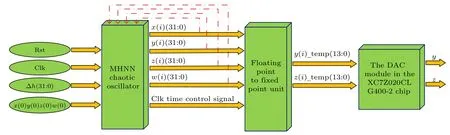
Fig.4.Flow diagram of MHNN implementation with FPGA.
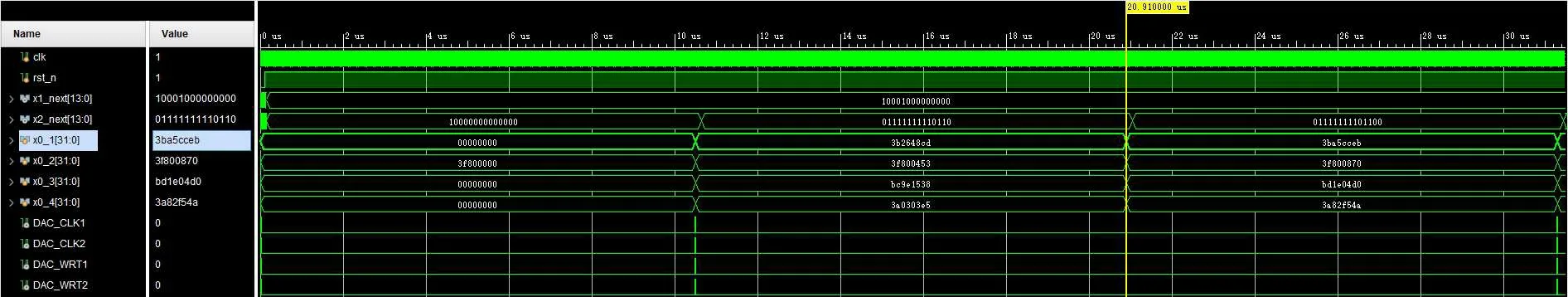
Fig.5.The simulation results of MHNN in the Vivado design tool.
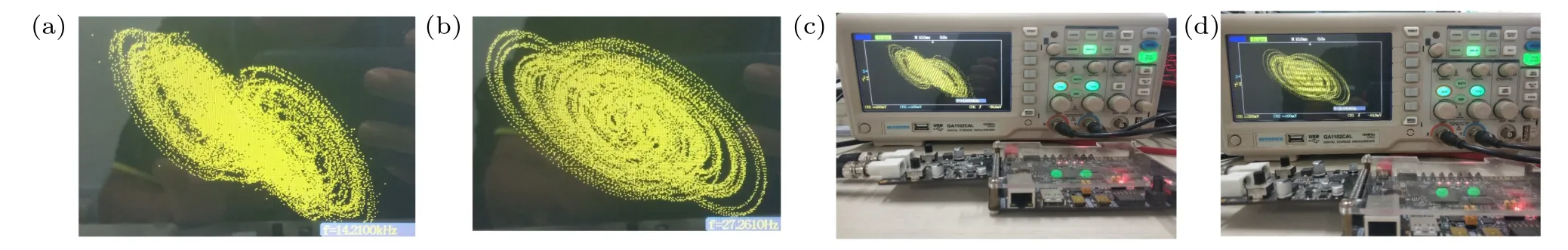
Fig.6.Experimental results of the MHNN chaotic system based on FPGA.(a)Phase diagram projected on z–x plane; (b)phase diagram projected on z–y plane;(c)and(d)the environments of phase diagram experiment.
3.Design and FPGA implementation of digital PRNG
3.1.The design of PRNG based on MHNN
In this part, a novel PRNG is proposed by combining the nonlinear post-processor proposed in Ref.[43] and the characteristics of MHNN in this paper.The workflow of the PRNG is shown in Fig.7.As the entropy source of PRNG, the MHNN chaotic oscillator provides random numbers for post-processing unit, where step size Δh=0.01 and initial condition(x(0),y(0),z(0),w(0))=(0,1,0,0).(x(i),y(i),z(i),w(i)),as the output vector of entropy source,enters the post-processing unit under the control of CLK clock control signal.The specific steps of the post-processing unit are as follows:
Step 1According to the IEEE 754-1985 high precision 32-bit floating point standard,the fractional part of a floating point number is more random.Therefore,in the nonlinear post-processor,the 10th to 31st bits of the input vector are retained,and the output is

Step 2The first λ and last 22 −λ bits of the output vector are swapped by translation, respectively, as shown in Fig.8,where the 0-th and 23-rd bits ofx(I)are XORed to obtainQ.IfQ=1,then λ =8,and otherwise,λ =9.The output vector
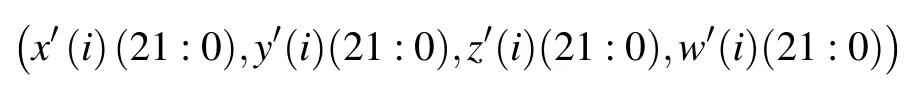
is obtained.
Step 3The vectors

are fed into the XOR.Because the Lyapunov index of the first dimension of MHNN chaotic oscillator is the largest.Therefore,x(i)(22:1)is used for bitwise XOR with
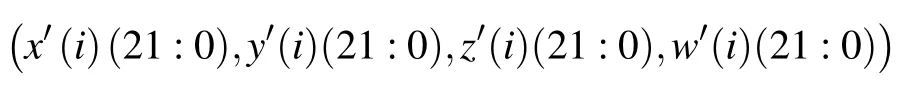
respectively.Finally,each iteration produces a random sequence of 88 bits.
In the random sequence quantization unit,the desired random sequence is finally obtained by several iterations.
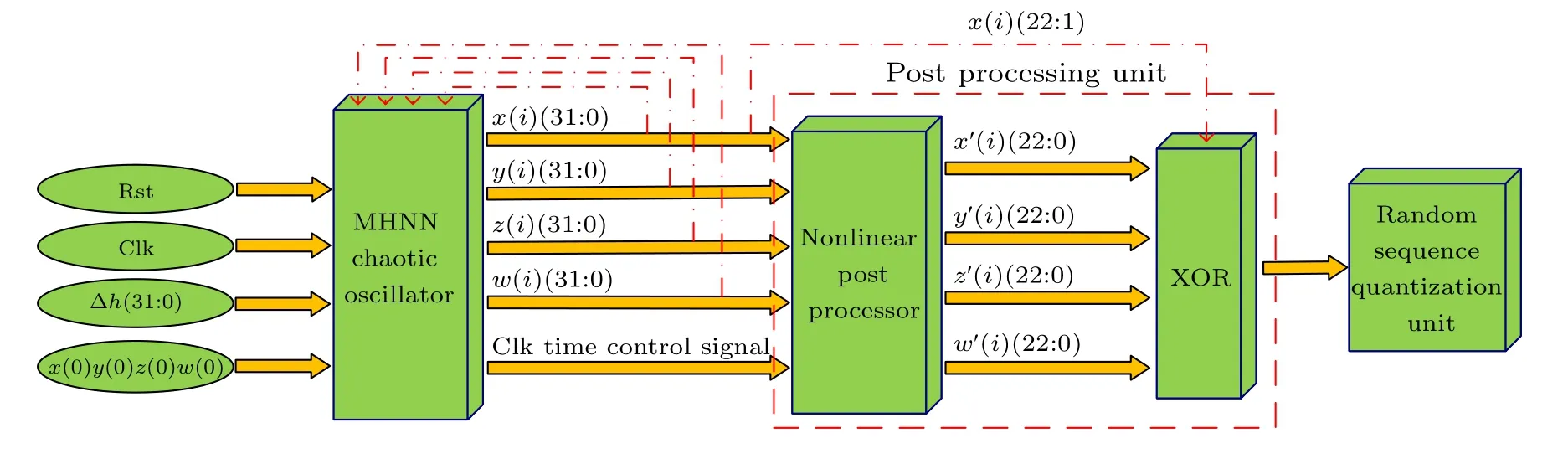
Fig.7.Workflow diagram of the PRNG.
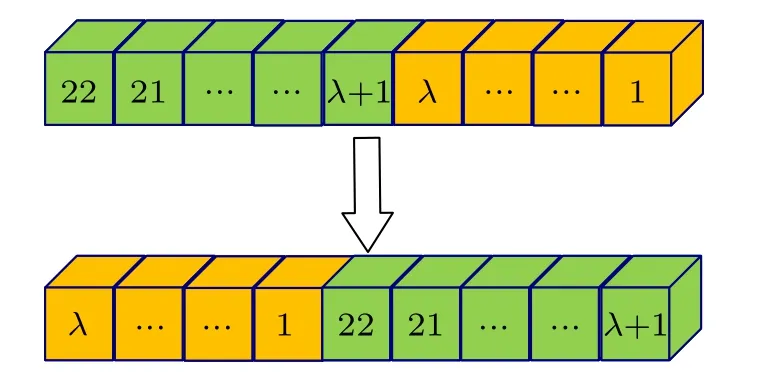
Fig.8.Schematic diagram of position exchange of nonlinear post processor.
3.2.Implementation of the PRNG based on FPGA
In this part, the MHNN chaotic oscillator is synthesized as the entropy source of PRNG by using RK4 design algorithm and alternative activation function for a Xilinx XC7Z020CLG400-2 FPGA chip.The behavior simulation results of PRNG based on MHNN are obtained by Vivado design tools,as shown in Fig.9,where x_reg represents the output of the random sequence.Table 1 shows the chip resource consumption and clock frequency required for the synthesis of the proposed PRNG.Finally,the bit stream generated by the random sequence is obtained and displayed on an oscilloscope,as shown in Fig.10.
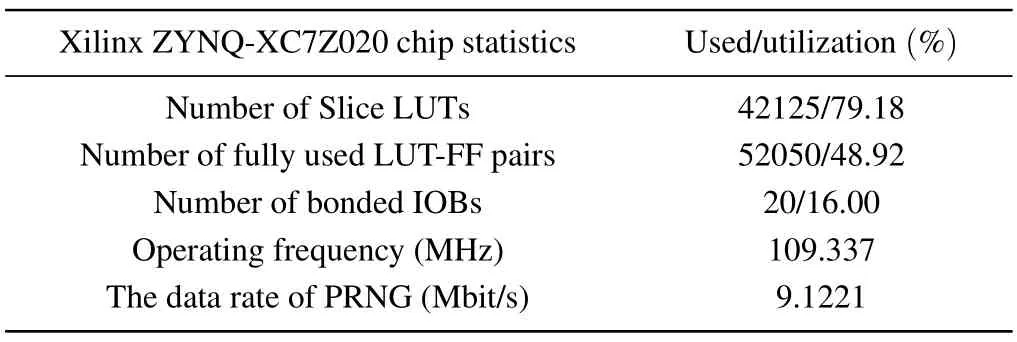
Table 1.Statistical results of chip resource consumption and clock frequency.
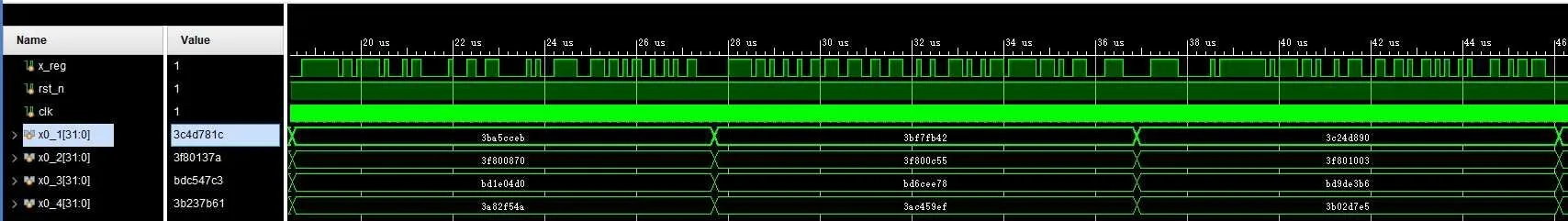
Fig.9.The behavior simulation results of PRNG based on MHNN on Vivado design suite.
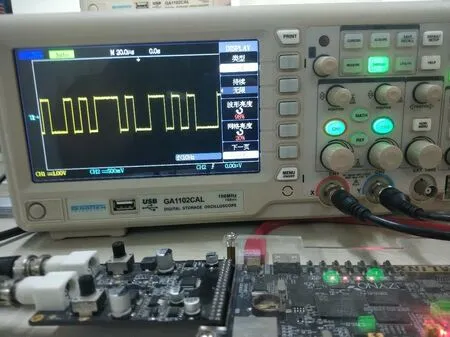
Fig.10.Experimental results of the MHNN-based PRNG implemented on an FPGA are shown on an oscilloscope.
4.Safety analysis
4.1.Randomness test
Today,more and more PRNGs is being used in areas such as key data and encryption programs.As a consequence, the quality of the random sequences generated by PRNGs is increasingly required.To meet this request, the National Institute of Standards and Technology(NIST)has published NIST SP800-22, a randomness test standard for application to random sequences and PRNGs.[64]This standard contains 15 statistical tests, all of which are evaluated by aP-value, with aP-value greater than 0.01 indicating that the test results meet the standard; otherwise, the test results do not meet the standard.The order of the 15 statistical tests in the test suite is arbitrary.However, frequency tests are normally given priority because this statistical test provides the most basic guarantee for randomness and inhomogeneity of random sequences.If this statistical test fails, other statistical tests are likely to fail as well.Finally,the test suite was developed in ANSI C.
In this paper, the MHNN-based PRNG implemented by FPGA generates a 100-Ms bit random sequence and saves the random sequence in a text file.First, we opened the NIST SP800-22 test suite and set each group of random sequences to 1-M bit.Then,in the test suite,select the address of the text file to save the random sequence and set the number of random sequence groups.Finally, set the random sequence type to binary.The results are shown in Table 2.
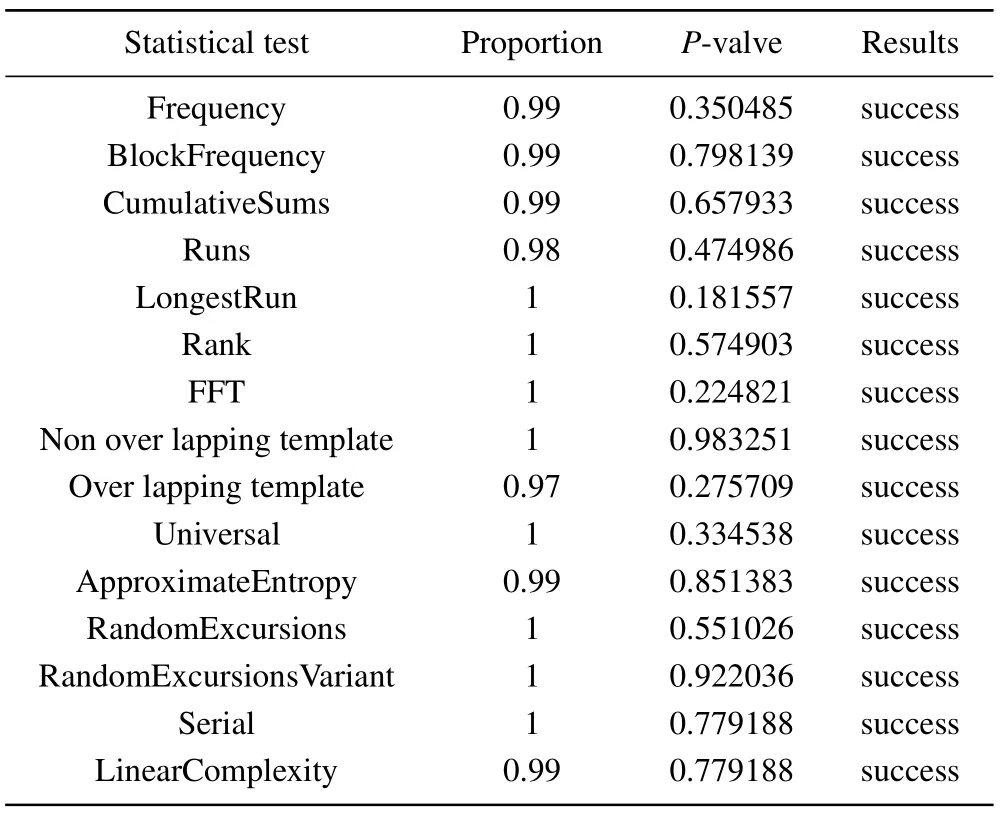
Table 2.The randomness test results of the MHNN-based PRNG implemented in FPGA.
4.2.Key space test
The PRNGs based on neural network chaotic systems each have their own key space,the size of which is positively related to the length of the PRNG key.When the key length isn, the key space is 2n.Currently, PRNG key space is required to be greater than 2128in order to resist the exhaustive attack of high computing power computers.The initial conditions and system parameters of MHNN based on FPGA are set according to IEEE 745-1985 high-precision 32-bit floating point standard, which can ensure the randomness and security of PRNG.Therefore,the key lengthn=512 of the PRNG proposed in this paper makes the key space 2512greater than 2128.It shows that the MHNN-based PRNG implemented on FPGAs can effectively resist exhaustive attacks.
4.3.Key sensitivity test
Key sensitivity analysis can show the influence of small changes in initial conditions or system parameters on the corresponding output of a chaotic system.MHNN chaotic system has key sensitivity based on chaos.Therefore, MHNN-based PRNGs can be subjected to key sensitivity analysis.The bit conversion rate is used to evaluate the sensitivity of binary random sequence keys.The calculation formula is as follows:
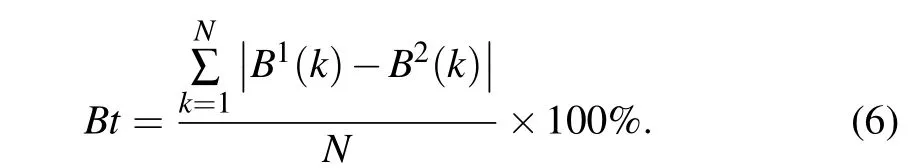
Here,{B1(k)} represents the random sequence generated by PRNG under normal conditions, and {B2(k)}represents the random sequence generated when the initial conditions of PRNG or system parameters change slightly.The length of the two random sequences is represented byN.The length of the random sequence tested in this paper isN=840 kB.The bit conversion rateBtis used as the result of the key sensitivity test,and the best result of the test is whenBt=50%.Table 3 shows the bit conversion rate of PRNG proposed in this paper.Where,I′anda′are the initial conditions and parameters added by 10−8respectively.On the basis of the changed initial conditionI′and parametera′,two random sequences {} and {} were generated,which were subjected to the bit conversion rate calculation with {B1(k)} respectively to obtain the resultBt≈50%.Small changes in the system parameters or initial conditions will directly cause changes in the chaotic sequence of the MHNN chaotic system, as shown in Fig.11.So the proposed PRNG has a high key sensitivity and meets the test requirements.

Table 3.The bit conversion rate is obtained under the conditions of I′and a′.
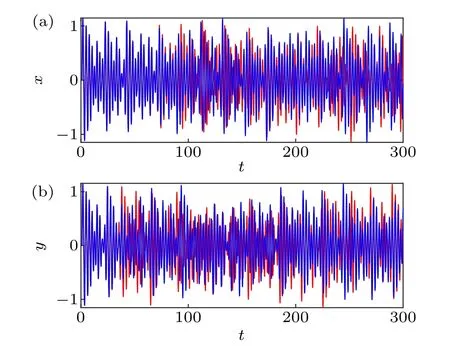
Fig.11.Time-series diagram of the first dimension x of the MHNN chaotic system when the initial conditions I′and the system parameters a′.(a)Timeseries diagram of x when the initial conditions change to I′.(b)Time-series diagram of x when the initial conditions change to a′.
4.4.Auto-correlation and cross-correlation test
Auto-correlation and cross-correlation are collectively referred to as correlation, which is used to assess the similarity of the random sequences generated by PRNG after shift.The correlation between random sequences after shift is calculated by the following formula:

wherejis the number of shifts in the random sequence andR(j)∈[−1,1]denotes the correlation of the random sequence after a shift ofjbits.In this section,the random sequence used for testing is consistent with the random sequence used for key sensitivity analysis.In auto-correlation,the random sequence {B1(k)} is shifted byjbits to obtain the random sequence {B1(k)}′.SandDdenote the number of elements that are the same and the number of elements that are different between {B1(k)} and {B1(k)}′, respectively.In cross-correlation, the random sequence {B1(k)} is compared with the constantly shifted random sequence,withSandDdenoting the number of identical elements and the number of different elements between the two random sequences, respectively.Nis the number of elements of the random sequence being tested.In addition, whenSandDtend to be the same,R(j)tends to 0.Therefore,R(j)=0 is the ideal result of the correlation.
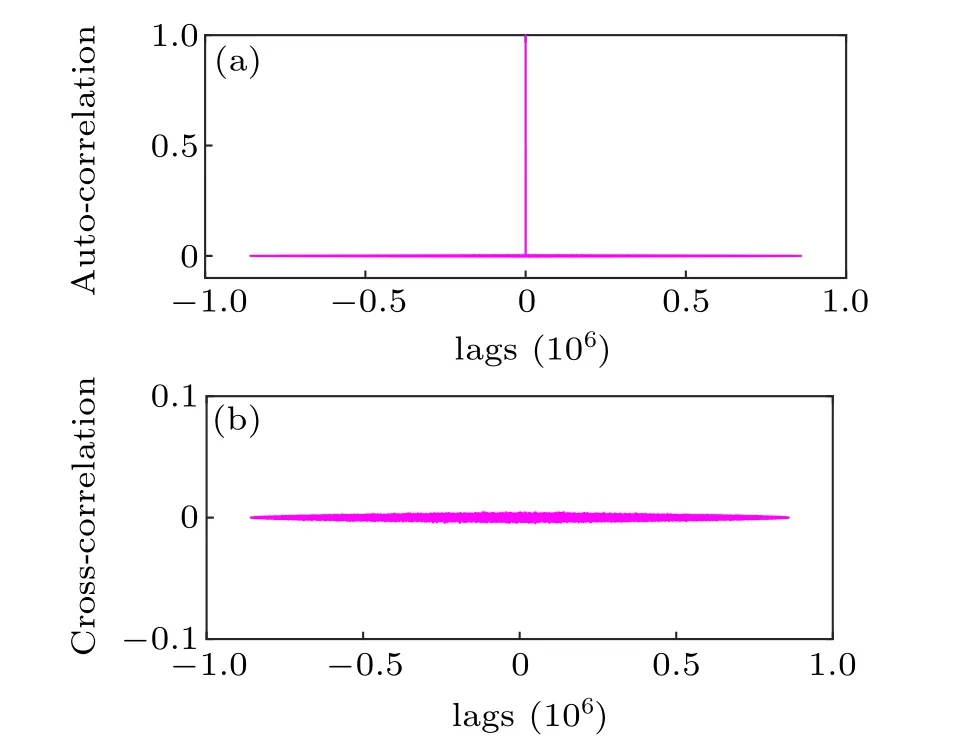
Fig.12.The correlation analysis diagram of random sequence generated by PRNG based on FPGA.(a) The auto-correlation analysis diagram.(b) The cross-correlation analysis diagram.
In this part, the correlation analysis diagram is obtained based on the calculation of Eq.(7),as shown in Fig.12.Figure 12(a) is the auto-correlation analysis diagram of random sequence {B1(k)} withN=840 kB,figure 12(b)is the crosscorrelation analysis of random sequence {B1(k)} and {B12(k)} withN=840 kB.From Fig.12,R(j)tends to 0 whenj/=0.Therefore,the random sequence generated by the FPGA-based PRNG proposed in this paper has a very low correlation.
5.Application of PRNG in image encryption
As the IoT continues to develop,more and more new applications are revolutionising people’s lives,such as the Internet of Vehicles and the Internet of Medical Things.However,the proliferation of IoT applications is likely to generate large amounts of private data and it is therefore extremely essential to ensure the security of data transmission.[65–67]Image encryption systems,as a basic application of PRNG based on chaotic systems, can provide security for the transmission of image data.[68–70]In this section,an image encryption and decryption system is designed using the MHNN-based PRNG proposed in this paper and implemented on an FPGA.In order to ensure the feasibility and security of the image encryption and decryption system,the system will be simulated and security analysed on MATLAB software.
5.1.Structure design and security analysis of encryption and decryption system
he architecture structure diagram of the image encryption and decryption system implemented on FPGA designed in this paper is shown in Fig.13.According to the structure diagram,we can obtain the system operation steps as follows.
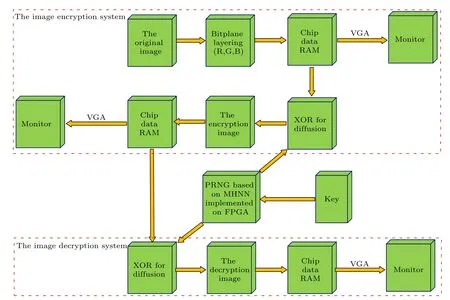
Fig.13.FPGA-based image encryption and decryption system architecture diagram.
Step 1In this experiment, a 256×256 24-bit depth true colour image of “Lena” is used as the original image.Since each pixel of the image “Lena” is 24-bit of binary data, each pixel is divided into three 8-bit data,resulting in theR,G,andBbit planes.The binary data of the three bit planes is stored in the chip data RAM and connected to the monitor via the VGA display controller.
Step 2The MHNN-based PRNG implemented on the FPGA generates 88-bit binary random numbers per iteration,so the binary random numbers generated by the iterations are divided into eight 11-bit binary data and performed self-XOR operations in turn,resulting in eight binary random numbers.Thus, by entering the correct key into the PRNG, three 524288-bit binary random sequencesR1,R2, andR3are obtained by iteration.
Step 3In the image encryption system, the diffusion of the original image data is achieved byR⊕R1=R′,G⊕R2=G′,andB⊕R3=B′where ⊕denotes the XOR operation.The new three bit-planeR′,G′, andB′data obtained are stored in the chip data RAM as the encrypted image data.Finally,it is displayed on the monitor using the VGA display controller.
Step 4In the decryption system,the PRNG with the correct key generates the random sequencesR1,R2andR3.The diffusion is completed byR′⊕R1=R,G′⊕R2=G, andB′⊕R3=Bto obtain the decrypted image data,which is stored in the chip data RAM.Finally, the connection to the monitor is made by the VGA display controller.
The simulation result on MATLAB platform,as shown in Fig.14.Figures 14(a)and 14(b)are the original image and the encrypted image, respectively.Figure 14(c)is the decryption image after obtaining the correct key.

Fig.14.The simulation results of image encryption and decryption systems:(a)original image;(b)encryption image,and(c)decryption image.
The result of security analysis is an important index to evaluate the security and encryption performance of an image encryption and decryption system based on PRNG.The security analysis of this experiment includes histogram analysis,differential key attack analysis,and entropy analysis.The specific analysis is as follows:
(i) Histogram analysis: The whole process of image encryption and decryption system proposed in this paper is based on binary series, so the system has similar encryption performance for any image to be encrypted.Histogram represents the digital spectrum of image data, and the ideal spectrum of encrypted image should be evenly distributed.The histogram analysis results are shown in Fig.15.Figures 15(a)and 15(c)show the original image and its histogram, and figures 15(b)and 15(d) show the encrypted image and the corresponding histogram.Figure 15(d) shows that the data frequencies of the encrypted images are uniformly distributed.Therefore,the proposed image encryption and decryption system has a high encryption performance.
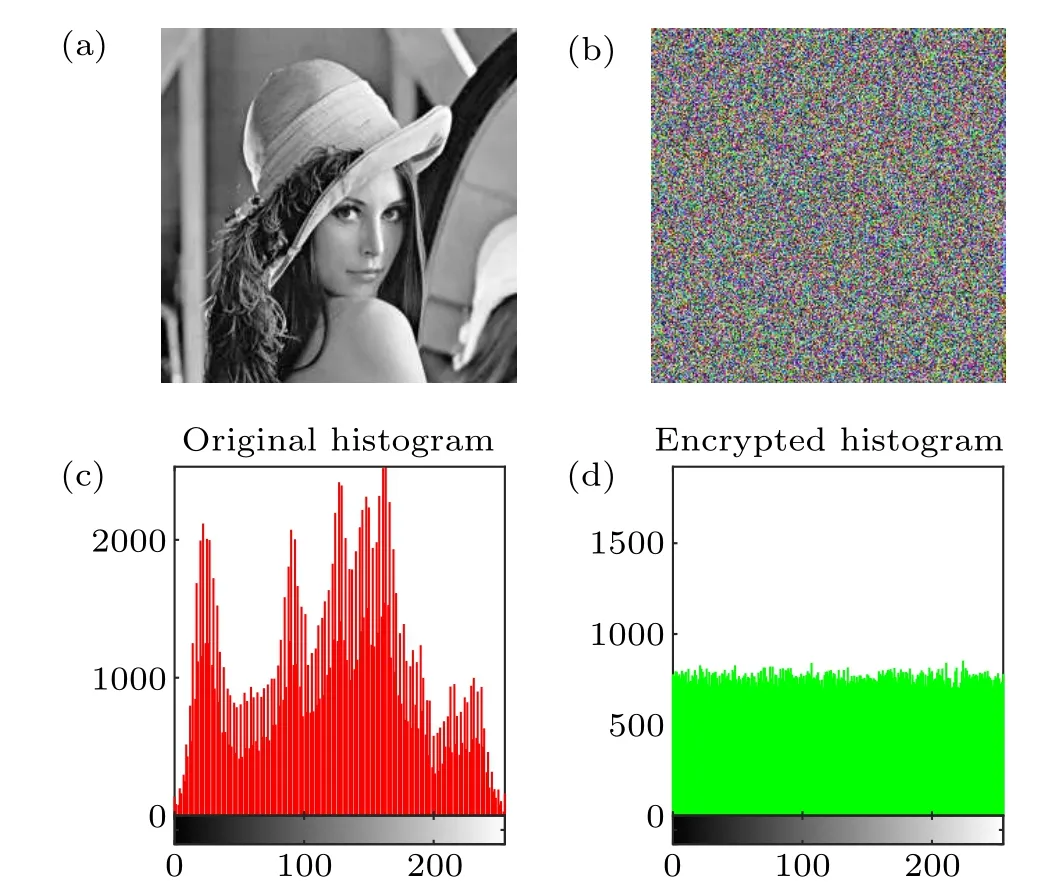
Fig.15.The histogram analysis results.Panels (a) and (b) are the original image and the encrypted image;panels(c)and(d)are histograms of the original image and the encrypted image.
(ii) Differential key attack analysis: Differential key attack is an attack method in which a finite number of incorrect key results with tiny differences are analysed to finally arrive at the correct key.The differential key attack analysis evaluates the impact of distinct keys on the encrypted image by two metrics, the Number of Pixel Change Rate (NPCR) and the Uniform Average Change Intensity(UACI).The formulae for NPCR and UACI are shown below:
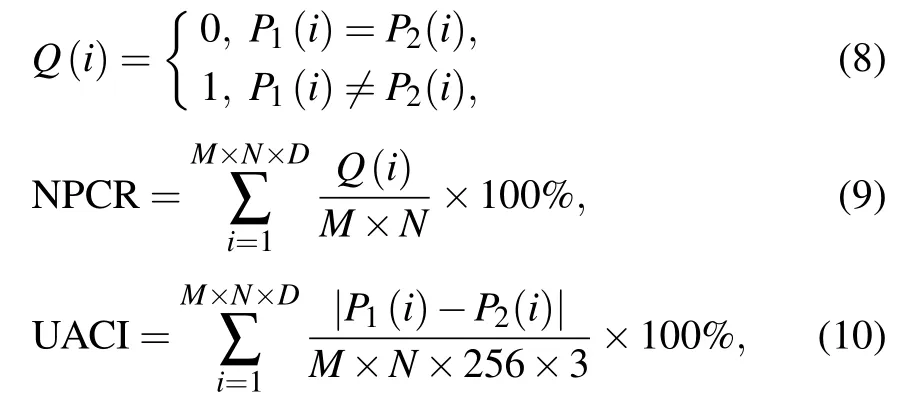
whereM,N=256,andD=24 are the image pixel depths.P1is the binary data sequence of the encrypted image obtained with the correct key,andP2is the binary data sequence of the encrypted image obtained with the key whose initial condition becomes(10−8,1,0,0).The results of the differential key attack analysis,as shown in Table 4,are more satisfactory.

Table 4.The results of NPCR and UACI in differential key attack analysis.
(iii) Entropy analysis: Information entropy is used to analyse the complexity and randomness of image encryption and decryption systems.The result of information entropy can be calculated using
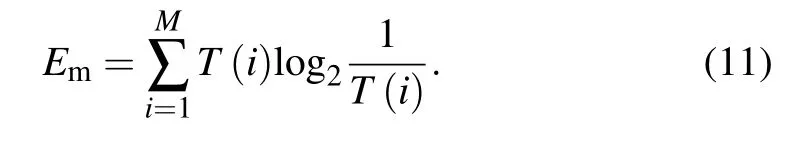
The calculation of information entropy requires that the binary image data is first converted to decimal data in units of 8 bits.T(i) is the frequency of occurrence of decimal image data in the range 0 to 255.Since each pixel in the bit plane is 8 bits, the closer the information entropy calculation result is to 8,the better.The calculation results of this experiment are shown in Table 5.The results show that the image encryption and decryption system proposed in this paper has high complexity and randomness.

Table 5.The calculation results on information.
(iv) Correlation analysis of adjacent pixels: The performance of image encryption system is related to the correlation of adjacent pixels of the image before and after encryption.Because the adjacent pixels of the image before encryption have high correlation, a high security image encryption system can effectively reduce the correlation of adjacent pixels of the image after encryption.Because the adjacent pixels of the image before encryption have high correlation,a high security image encryption system can effectively reduce the adjacent pixel correlation of the encrypted image.In this experiment,we select the first 196607 bits pixel of the image asS1and the last 196607 bits pixel asS2, and calculate the correlation coefficients of adjacent pixels of the image before and after encryption through Eq.(12), whereandare the average,n=196607.The results are shown in Table 6.Because the closer the correlation coefficient is to 0,the lower the correlation is, the image encryption system has high encryption performance.
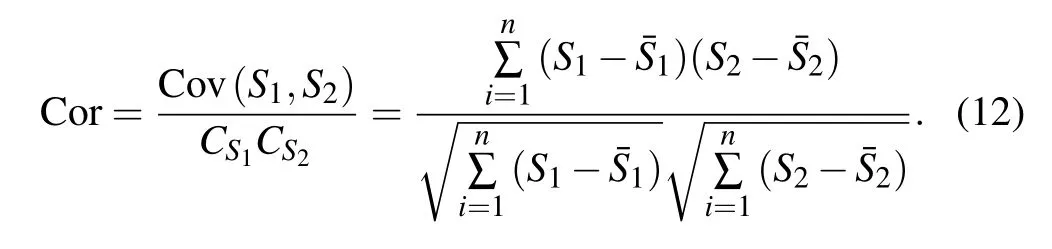

Table 6.Correlation analysis results of adjacent pixels.
5.2.The FPGA implementation
This experiment was done on the Vivado design tool,using Verilog-HDL as the hardware design language.The Xilinx XC7Z020CLG400-2 FPGA chip provided the chip data RAM and the VGA display controller for the experiment.The system structure and experimental flow are consistent with those of the simulation on the MATLAB software platform.The experimental results are shown in Fig.16.Figure 16(a)shows the original and encrypted images displayed by the system when the correct key is entered,and figure 16(b)shows the decryption results of the system when the correct key is obtained.With the results, it can be seen that the system is of great research value in data encryption related to the IoT.
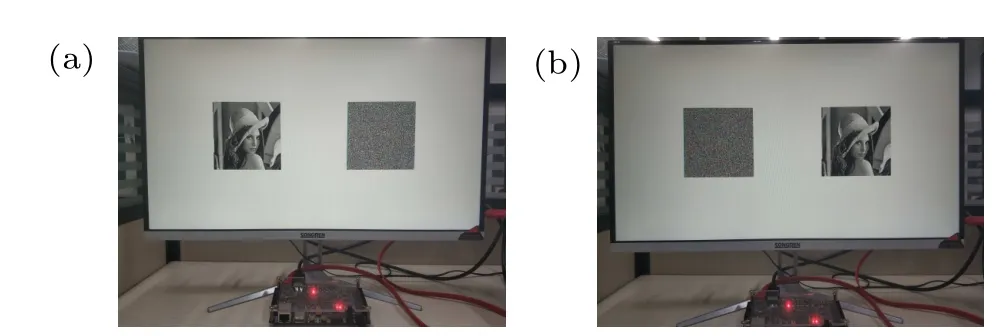
Fig.16.The PRNG-based image encryption and decryption system implemented on FPGA.Panel (a) is the encryption system and panel (b) is the decryption system.
6.Conclusion
In this paper, a PRNG based on MHNN is proposed and implemented on the Vivado design tool using the Xilinx XC7Z020CLG400-2 FPGA chip.the post-processing unit of the PRNG consists of a nonlinear post-processor and an XOR calculator,which also requires the MHNN chaotic oscillator’s the first dimensional output is used as input data as a way to improve the randomness of the PRNG implemented on the FPGA.The experimental results show that the PRNG produces a random sequence of 88 bits per iteration,with an output rate of up to 9.1221 Mbit/s.The security and high performance of the PRNG is confirmed by security analysis.Finally,the PRNG-based image encryption and decryption system was designed and passed the image security analysis,demonstrating the value of this PRNG in the field of IoT-related data encryption.
Acknowledgments
Project supported by the Scientific Research Fund of Hunan Provincial Education Department (Grant No.21B0345),the Postgraduate Scientific Research Innovation Project of Changsha University of Science and Technology (Grant Nos.CX2021SS69 and CX2021SS72), the Postgraduate Scientific Research Innovation Project of Hunan Province,China(Grant No.CX20200884), the Natural Science Foundation of Hunan Province, China (Grant Nos.2019JJ50648,2020JJ4622, and 2020JJ4221), the National Natural Science Foundation of China (Grant No.62172058), and the Special Funds for the Construction of Innovative Provinces of Hunan Province,China(Grant Nos.2020JK4046 and 2022SK2007).
- Chinese Physics B的其它文章
- High sensitivity plasmonic temperature sensor based on a side-polished photonic crystal fiber
- Digital synthesis of programmable photonic integrated circuits
- Non-Rayleigh photon statistics of superbunching pseudothermal light
- Refractive index sensing of double Fano resonance excited by nano-cube array coupled with multilayer all-dielectric film
- A novel polarization converter based on the band-stop frequency selective surface
- Effects of pulse energy ratios on plasma characteristics of dual-pulse fiber-optic laser-induced breakdown spectroscopy