Improvement of a continuous-variable measurement-device-independent quantum key distribution system via quantum scissors
Lingzhi Kong(孔令志), Weiqi Liu(刘维琪), Fan Jing(荆凡), Zhe-Kun Zhang(张哲坤),Jin Qi(齐锦), and Chen He(贺晨)
College of Information Science and Technology,Northwest University,Xi’an 710127,China
Keywords: measurement-device-independent,quantum key distribution,quantum scissors,performance
1. Introduction
Quantum key distribution(QKD)enables two distant legitimate parties, Alice and Bob, to share secret keys in the presence of eavesdropper(Eve). Based on the laws of Heisenberg’s uncertainty principle and no-cloning theory, QKD can achieve unconditional secure communication through the untrusted channel in theory.Currently,the mainstream QKD protocols can be divided into discrete variable quantum key distribution(DVQKD)protocols[1-3]and continuous variable quantum key distribution(CVQKD)protocols.[4-9]The Gaussianmodulated coherent state (GMCS) CVQKD protocol,[10-12]which encodes information on the quadratures of coherent state and measures the quadratures via homodyne detector or heterodyne detector,has become the most favorable protocol.This protocol has been certified to be secure in both asymptotic case[13]and finite-size effect,[14]and its composable security has been established under collective attack. Furthermore,the GMCS CVQKD protocol has been successfully demonstrated in both labs and field tests.
However,theoretical security analyses of CVQKD protocol usually depend on some ideal theoretical hypothesis and models. Actually,practical CVQKD systems are usually deviated from ideal theoretical models. Devices applied in practical CVQKD systems may be imperfect,[15]such as laser source,beam splitters and detectors. Deviation between nonideal devices and idealized models will open loopholes for Eve to eavesdrop encrypted information without being discovered. To defend side channel attacks,[16]some researchers put forward measurement-device-independent (MDI) QKD protocol.[17-21]Similarly,MDI-QKD protocols can be mainly divided into discrete variable (DV) MDI-QKD protocols[22]and continuous variable (CV) MDI-QKD protocols.[23-25]Compared to a DV-MDI-QKD system, the maximum transmission distance of the CV-MDI-QKD system is not satisfactory.Therefore,improvement of performance of the CV-MDIQKD system has been a hot spot in recent years.
In order to improve performance of CV-MDI-QKD systems, some researchers have proposed various schemes,which can be mainly summarized as optical amplifier,[26-29]photon subtraction operation[30-34]and quantum catalysis operation.[35-37]Among the mentioned methods,photon subtraction and quantum catalysis can improve the system performance by enhancing the success probability of non-Gaussion operations, while optical amplifier improves the system performance by amplifying the amplitude of the coherent state.Among various amplifiers,the heralded noiseless linear amplifier(NLA)[38-41]outperforms the other linear amplifiers,since it will maintain the initial noise level while amplifying the amplitude of the coherent state. However,the implementation of NLA should be under strict assumption that the amplifier is ideally noiseless,and it is of challenge to apply it to a practical CV-MDI-QKD system.
Fortunately, quantum scissors (QS),[42-48]an nondeterministic amplifying setup which combines the input signal with a single photon, can be regarded as an ideal NLA under weak amplitude of input signal. In this paper, we propose a new scheme to improve the performance of a GMCS CV-MDI-QKD system by introducing QS operation at Bob’s side. By amplifying the amplitude of the input state, the system performance can be improved considerably.[46]Simulation results show that the QS-enhanced CV-MDI-QKD protocol indeed outperforms the original CV-MDI-QKD protocol in both the secret key rate and the maximum transmission distance. Moreover,the better the performance of QS operation,the more significant the improvement of the performance of the system.
The rest of this paper is structured as follows. In Section 2,we investigate the proposed scheme of the GMCS CVMDI-QKD protocol with QS operation in detail. Afterwards,the performance analysis of the new scheme is demonstrated in Section 3. Eventually,conclusions are drawn in Section 4.
2. The new scheme of CV-MDI QKD with quantum scissors
In this section,we firstly introduce the GMCS CV-MDIQKD protocol with QS operation in detail. Afterwards, we investigate the QS operation in accordance with the equivalent one-way scheme,especially the success probability of the QS operation. Eventually, we perform simulation to demonstrate that success probability will be affected by some parameters.
2.1. The QS-enhanced GMCS CV-MDI-QKD protocol
Generally speaking, the prepare-and-measure (PM)scheme is usually applied for practical implementation,while the equivalent entanglement-based (EB) scheme is of great convenience for analysis. The EB scheme of the CV-MDIQKD protocol with QS operation is drawn in Fig.1,which is comprised of the following steps.
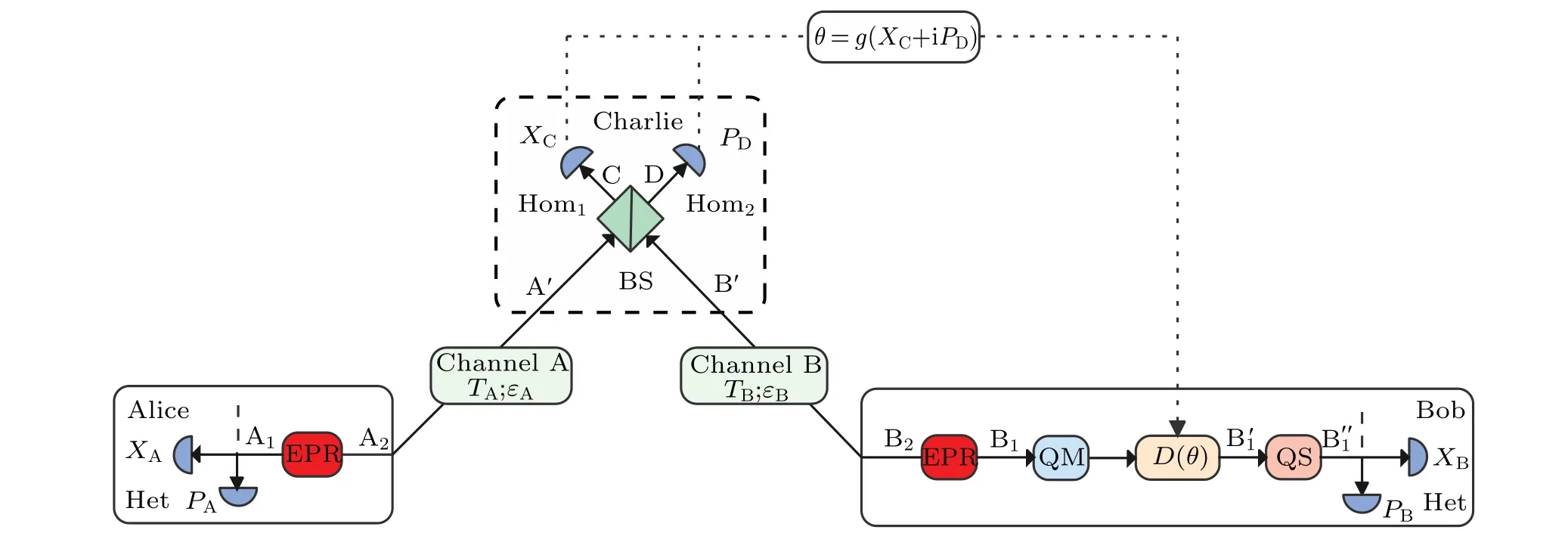
Fig. 1. The EB scheme of the GMCS CV-MDI-QKD protocol with QS operation. EPR: Einstein-Podolsky-Rosen state; BS: beam splitter;Hom: homodyne detector;Het: heterodyne detector;QM:quantum memory;D(θ): displacement operation;QS:quantum scissors operation.
Step 1 Alice prepares an EPR state with modulation varianceVAand retains mode A1to perform heterodyne detection,while the other mode A2is transmitted to the untrusted third party Chaile via the lossy channel A with transmittanceTAand excess noiseεA. Similarly, Bob prepares another EPR state with modulation varianceVBand retains mode B1,while the other mode B2is transmitted to the untrusted third party Chaile via the lossy channel B with transmittanceTBand excess noiseεB. Thus the corresponding transmittance of the channels A and B can be expressed as
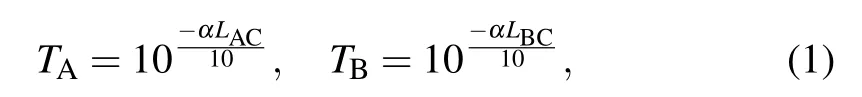
whereα= 0.2 dB/km represents the loss coefficient of the fiber channel,LACandLBCdepict the length of the channels A and B,respectively.As a result,the total transmission distance between Alice and Bob isLAB=LAC+LBC.
Step 2 After being transmitted through the lossy channel,modes A'and B'are obtained. Then Charlie interferes them at the 50:50 beam splitter (BS) with output modes C and D.Afterwards,Charlie performs homodyne detection to measure the quadraturexof the mode C and the quadraturepof the mode D.As consequence,measurement resultsXCandPDare obtained and announced publicly by Charlie.
Step 3 The mode B1is stored in the quantum memory until Charlie announces the measurement result{XC,PD}and returnsθ=g(XC+iPD)to the displacement operationD(θ),wheregdepicts the gain of the displacement operation. When the mode B1is released from quantum memory,Bob performsD(θ)on the mode B1,further obtains the mode B'1. The mode B'1is probabilistically amplified by the QS operation and the amplified mode B''1is obtained. Afterwards, Alice and Bob perform heterodyne detection on the modes A1and B''1, respectively. Eventually, Alice and Bob obtain the final measurement results{XA,PA}and{XB,PB}. It is noteworthy that the measurement results will be useful if and only if the QS setup works successfully.
Step 4 Alice and Bob accomplish the steps of parameter estimation,reverse reconciliation and privacy amplification through a classical channel. Ultimately, Alice and Bob share the encrypted key.
2.2. The equivalent one-way model of the CV-MDI-QKD protocol with QS operation
In the proposed scheme,since the QS operation is an nondeterministic amplifying setup,the final secret key rate should be multiplied by the success probabilityPsucc. Therefore, it is of great significance to investigate the success probabilityPsucc. For simplicity,under the assumption that all operations at Bob’s side are untrusted except the heterodyne detection,the EB scheme of the GMCS CV-MDI-QKD protocol can be converted into a specific one-way scheme using entanglement swapping,in which both Alice and Bob perform heterodyne detection on modes A1and B''1, respectively, as drawn in Fig.2. In what follows,we firstly give a brief introduction of QS operation and further investigate the success probabilityPsucc in detail.

Fig. 2. Equivalent one-way scheme of GMCS CV-MDI-QKD with QS operation. Vac: vaccum states; SPS: single photon source; BS1:balanced beam splitter;BS2: unbalanced beam splitter with transmittanceµ;D1 and D2: single photon detectors.


From Eqs.(1)-(5),we can conclude that the success probability of the QS operation behaves as functions of the transmission distancesLACandLBC,the equivalent excess noiseε,the equivalent transmittanceT,the transmittanceµof the BS2 and the modulation varianceVA. Among these parameters,Tandεare relevant to parametersLAC,LBC,εAandεB. As a result, the success probability can be expressed as a functionPsucc=Psucc(LAC,LBC,εA,εB,µ,VA). For simplicity, we investigate the success probability under the extreme asymmetric circumstance thatLAC/=LBCandLBC=0. Therefore,the function can be simplified toPsucc=Psucc(LAC,εA,εB,µ,VA).
To demonstrate the effect of the transmittanceµ, transmission distanceLACand the excess noiseεA(εB)and on the success probability of the QS operation, we perform simulations as shown in Fig. 3. The success probabilityPsuccas a function of modulation varianceVAunder different transmittanceµis plotted in Fig.3(a). From top to bottom, the three curves depict the relationship between the success probabilityPsuccand modulation varianceVAwith transmittanceµ=0.8,µ= 0.7 andµ= 0.6, respectively. Obviously, the success probabilityPsuccincreases with the increasing transmittanceµwhen other parameters are the same. Meanwhile, the success probabilityPsuccincreases with the increasing modulation varianceVAwithin a certain range, while the success probabilityPsuccwill decrease gradually whenVAexceeds a certain value.The certain value can be labeled as the optimal variance and the optimal variance decreases slightly with the increasing transmittanceµ.
Afterwards, we investigate the relationship between the success probabilityPsuccand the modulation varianceVAwith different transmission distanceLAC,as drawn in Fig.3(b).The success probabilityPsuccincreases with the increasing modulation varianceVAwithin a certain range and decreases gradually whenVAexceeds the optimal variance. The optimal variance increases with the increasing transmission distanceLAC.Meanwhile,we find that the success probabilityPsuccincreases with the increasing transmission distanceLACwhen the optimal variance is exceeded.Finally,the success probabilityPsuccas a function of modulation varianceVAfor different excess noiseεA(εB) is plotted in Fig. 3(c). The success probabilityPsuccincreases with the increasing modulation varianceVAwithin a certain range and decreases gradually whenVAexceeds the optimal variance. The optimal variance decreases as the excess noise increases.Meanwhile,the success probabilityPsuccchanges slightly when the excess noiseεA(εB)fluctuates greatly,which implies that the effect of the excess noise on the success probabilityPsuccis much smaller than the transmittanceµand transmission distanceLAC. In brief, the analysis of success probabilityPsuccof the QS operation is beneficial to select the appropriate parameters to obtain the optimal system performance.

Fig.3. (a)Success probability as a function of VA with different transmittanceµ. The excess noise εA(εB)is fixed at 0.02 and the transmission distance LAC =30 km. (b)Success probability as a function of VA with different transmission distance LAC. The excess noise εA (εB)is fixed at 0.02 and the transmittanceµ =0.6. (c)Success probability as a function of VA with different excess noise εA (εB). The transmission distance LAC=30 km and the transmittanceµ =0.6.
3. Performance analysis of the new scheme
As aforementioned, the EB scheme of the QS-enhanced CV-MDI-QKD protocol can be converted into a specific oneway scheme under the assumption that all operations at Bob’s side are untrusted except the heterodyne detection. In other words,the EB scheme is a specific case of the equivalent oneway scheme with more constraints on Eve. Therefore,the secret key rate of the equivalent one-way scheme should be a lower bound of the EB scheme. Assuming that the secret key rate of the equivalent one-way scheme and the EB scheme areK∗andKQS,respectively,we can further obtainKQS≥K∗.[33]For the sake of simplicity, we use the lower bound ofKQSto depict the secret key rate of the QS-enhanced CV-MDI-QKD protocol under collective attack,that is,

where II=diag(1,1)andσz=diag(1,-1)with



Fig. 4. (a) Performance comparison between the original CV-MDIQKD protocol and the QS-enhanced CV-MDI-QKD protocol with transmittanceµ =0.6 under practical parameters and ideal parameters,respectively. The practical parameters focus on the detection efficiency of homodyne detector η =0.97, electronic noise of homodyne detector vel=0.01 and the ideal parameters focus on the detection efficiency of homodyne detector η =1, electronic noise of homodyne detector vel =0. (b) The secret key rate as a function of transmission distance for different transmittanceµ.Remaining parameters are similarly fixed:The excess noise εA=εB=0.01,the modulation variance VA=20,and reconciliation efficiency β =0.98.
In what follows, we analyze the performance of the GMCS CV-MDI-QKD system equipped with QS operation under the extreme asymmetric circumstance in detail. Firstly,to investigate the effect of the QS operation on the performance of the GMCS CV-MDI-QKD system, we perform the simulation of the original CV-MDI-QKD protocol[23,24]and the QS-enhanced CV-MDI-QKD protocol, respectively, as illustrated in Fig.4(a). The blue curve represents the secret key rate of the original CV-MDI-QKD system versus the transmission distance with practical parameters. The red curve represents the secret key rate of the QS-enhanced CV-MDI-QKD system versus the transmission distance with practical parameters. The black curve depicts the relationship between the secret key rate of the original system and the transmission distance with ideal parameters. The purple curve depicts the relationship between the secret key rate of the system equipped with QS operation and the transmission distance with ideal parameters. The green curve is the PLOB bound,[49]which constrains the maximum secret key rate of the system with lossy channel. The results show that the QS-enhanced CVMDI-QKD protocol outperforms the original CV-MDI-QKD protocol in both the secret key rate and the maximum transmission distance. In other words,QS operation at Bob’s side can indeed improve the performance of the CV-MDI-QKD system significantly. In addition,compared to the system with an ideal homodyne detector at Charlie’s side,the performance of the system with a practical homodyne detector which has finite detection efficiency and eletronic noise can be improved more considerably via the QS operation. In fact,the improvement of the performance can be attributed to the QS operation which truncates the input state to first order and simultaneously amplifies it by increasing the amplitude of the single photon component relative to the vacuum component.
Then from the schematic view of the QS operation, we can conclude that different transmittanceµcorresponds to different QS operation, further leads to different degree of improvement of the performance. As aforementioned, the success probabilityPsuccincreases as the transmittanceµincreases. In other words,the performance of the QS operation will increase with the increasing transmittanceµ. Therefore,we further perform the simulation to demonstrate the effect of the performance of QS operation on the improvement of the system,as plotted in Fig.4(b).From left to right,curves represent the secret key rate as a function of transmission distance for transmittanceµ=0.6, 0.7, 0.8, respectively. Simulation results indicate that the performance of the QS-enhanced system will improve more significantly with the increasing transmittanceµin both the secret key rate and the maximum transmission distance. In conclusion, the better the performance of QS operation,the more significant the improvement of the performance of the system.
4. Conclusion
In summary,we have proposed a new scheme to enhance the performance of the GMCS CV-MDI-QKD system by applying QS operation at Bob’s side. In order to investigate the success probability of the QS operation and demonstrate the effect of the QS operation on the performance of the CVMDI-QKD system, we perform simulations. The simulation results show that the transmittance of the unbalanced BS,the transmission distance, the excess noise and the modulation variance will all affect the success probability of the QS operation. Therefore, selecting suitable parameters is of great significance for obtaining the optimal performance. Subsequently,the performance analysis indicates that QS operation can indeed improve the performance significantly,in which the QS-enhanced CV-MDI-QKD protocol outperforms the original CV-MDI-QKD protocol in both the secret key rate and the maximum transmission distance. Meanwhile, the better the performance of QS operation,the more significant the improvement of performance of the system.
Acknowledgements
Project supported by the National Natural Science Foundation of China (Grant No. 62001383) and the Scientific Research Plan Project of Shaanxi Education Department(Natural Science Special Project)(Grant No.19JK0847).
- Chinese Physics B的其它文章
- Characterizing entanglement in non-Hermitian chaotic systems via out-of-time ordered correlators
- Steering quantum nonlocalities of quantum dot system suffering from decoherence
- Probabilistic quantum teleportation of shared quantum secret
- Spin–orbit coupling adjusting topological superfluid of mass-imbalanced Fermi gas
- An overview of quantum error mitigation formulas
- High Chern number phase in topological insulator multilayer structures: A Dirac cone model study

