Blockchain-Based MCS Detection Framework of Abnormal Spectrum Usage for Satellite Spectrum Sharing Scenario
Ning Yang,Heng Wang,Jingming Hu,Bangning Zhang,Daoxing Guo,Yuan Liu
College of Communications Engineering,Army Engineering University,Nanjing 210007,China
Abstract: In this paper,the problem of abnormal spectrum usage between satellite spectrum sharing systems is investigated to support multi-satellite spectrum coexistence.Given the cost of monitoring,the mobility of low-orbit satellites,and the directional nature of their signals,traditional monitoring methods are no longer suitable,especially in the case of multiple power level.Mobile crowdsensing (MCS),as a new technology,can make full use of idle resources to complete a variety of perceptual tasks.However,traditional MCS heavily relies on a centralized server and is vulnerable to single point of failure attacks.Therefore,we replace the original centralized server with a blockchain-based distributed service provider to enable its security.Therefore,in this work,we propose a blockchain-based MCS framework,in which we explain in detail how this framework can achieve abnormal frequency behavior monitoring in an inter-satellite spectrum sharing system.Then,under certain false alarm probability,we propose an abnormal spectrum detection algorithm based on mixed hypothesis test to maximize detection probability in single power level and multiple power level scenarios,respectively.Finally,a Bad out of Good(BooG)detector is proposed to ease the computational pressure on the blockchain nodes.Simulation results show the effectiveness of the proposed framework.
Keywords: blockchain;hypothesis test;mobile crowdsensing;satellite communication;spectrum sharing
I.INTRODUCTION
1.1 Background and Motivation
With the development of satellite communication technology,people turn their attention to satellite to solve the problem of the shortage of terrestrial spectrum[1-5].However,with the increase of the number of satellites and their terminals,the spectrum deficit on the satellite is becoming more and more serious,which makes the inter-satellite and satellite-terrestrial spectrum coexistence more prominent[6,7].Satelliteground spectrum sharing mostly refers to the opportunistic access of terrestrial devices to the satellite spectrum by sensing the satellite spectrum without affecting the normal operation of satellite receivers.Similarly,inter-satellite spectrum sharing means that the secondary satellite can access the spectrum of the primary satellite by sensing the spectrum of the primary satellite without affecting the normal operation of the primary satellite earth station.In particular,in the scenario of inter-satellite spectrum sharing [8],it is considered that secondary satellites may break the order of spectrum use to obtain higher benefits under selfish drive,malicious attack or equipment failure[9].From the perspective of selfish drive,the abnormal spectrum behavior of secondary satellites is caused by the higher transmission power.Specifically,when the secondary satellite detects the working primary satellite,the selfish secondary satellite breaks through the prescribed transmit power constraint in order to obtain a higher transmission rate and transmits the signal to its ground base station with a higher power.In this way,although the earth stations of the secondary satellite reap higher transmission benefits,the earth stations of the primary satellite will suffer unacceptable interference in return.At this time,because the secondary satellites are selfish,the efficiency of the whole inter-satellite spectrum sharing network will decline sharply,which is not conducive to the spectrum sharing between satellites.In addition,when the secondary satellite detects the primary satellite in a working state,the malicious secondary satellite will operate at a power level lower than the established transmit power in order to prevent other satellites from sharing the spectrum of the primary satellite.It is worth noting that although this action does not interfere with the primary satellite’s earth station,this covert action results in a significant reduction in the transmission rate of the secondary satellite.In this case,the time for the secondary satellite to transmit certain content will be extended,which will affect the detection ability of other secondary satellites that want to access the spectrum of the primary satellite,and then prevent other satellites from sharing the spectrum of the primary satellite.Therefore,the efficiency of the whole inter-satellite spectrum sharing network will also be weakened by this covert behavior.

Table 1.List of main abbreviations.
As an emerging technology that can outsource tasks that would normally be difficult to perform independently to a group of mobile workers (MWs) at a reasonable price for higher return [10],MCS is widely used in perceptual data acquisition tasks[11].Therefore,it can be used to detect abnormal spectrum behavior.However,as shown in Figure 1,traditional MCS rely heavily on a centralized server and is subject to a single point of failure attack (SPoF)[12].Once the central server is compromised,all the perceptual data will be exposed,which is unacceptable for SR and MWs [13].This is because if abnormal usage behavior will not be detected in time,MWs’ private information will be exposed at this time.Therefore,inspired by the above observations,in the scenario of inter-satellite spectrum sharing,how to safely and effectively detect abnormal spectrum behavior through MCS to further promote inter-satellite spectrum coexistence is an urgent problem to be solved,which has not been well studied at present and is the focus of this paper.
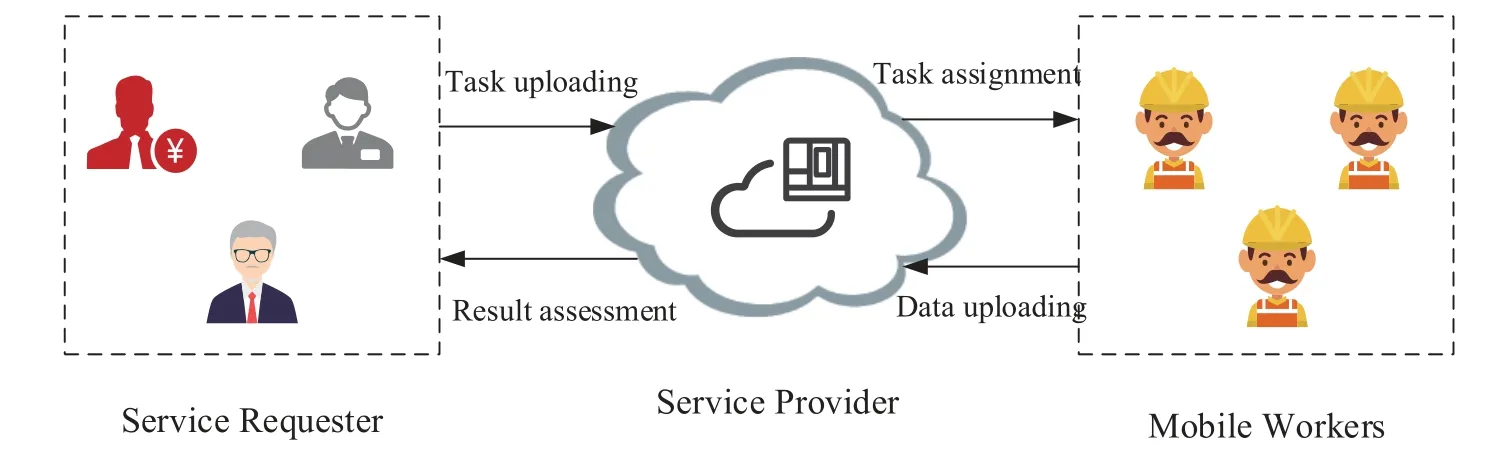
Figure 1.The traditional MCS framework in which service provider is only one server.
1.2 Related Works
With the advance of the space-air-ground integrated network (SAGIN),the high frequency band of satellite is considered to be an effective way to solve the shortage of spectrum resources.As a result,there is a lot of work focusing on how to properly share the spectrum of satellite.However,on the basis of reasonable use of satellite spectrum,there are still some secondary users who intentionally or unintentionally violate the spectrum order out of interest or malicious drive,thus destroying the inter-satellite or satelliteterrestrial spectrum coexistence.Therefore,in order to solve the above problems,there are some studies in this phase focused on how to detect these abnormal frequency behavior.
In [14],by using the high-order moment of the received signal to estimate the power of the hidden signal,the author realized whether there is unauthorized transmission in the cognitive satellite communication network,in which the unauthorized signal was taken as the decision variable.In[15],the generalized likelihood ratio test and the maximum a posteriori estimate were used to calculate the transmitted power of the ground users to detect the interference constraint violation problem in the satellite-ground fusion network.By using multiple hypothesis testing and maximum posterior criterion,the authors deduced the decision threshold of illegal user access detection to realize the detection of illegal user access in the satellite-ground spectrum sharing system[16].Our previous work also focused on the detection of abnormal frequency usage behavior in satellite-ground spectrum sharing system through hypothesis testing theory [17].In the intersatellite spectrum sharing scenario,in order to mitigate the interference received by GEO,an adaptive power allocation scheme was designed to maximize the throughput of LEO while keeping the maximum interference to GEO below the tolerable interference temperature of GEO[18].It is worth noting that most of the above studies only consider the detection problem of abnormal frequency usage by ground users in the satellite-ground spectrum sharing system,but ignore that with the increase of the number of satellites,the inter-satellite spectrum sharing system will also face this problem.To make matters worse,the above detection relies heavily on the deployed monitoring network,so because of the beam and wide range of satellite signals,the monitoring network infrastructure is difficult to apply to the inter-satellite spectrum sharing system when the ground is monitoring the satellite.
Because of the wide existence and flexible mobility of MWs,MCS is often used in the detection of abnormal frequency spectrum,which is expected to detect abnormal frequency behavior in the intersatellite spectrum sharing system.The existing research mainly focuses on the detection of anomaly spectrum through MCS framework.For the detection of spectral intrusion,the authors solved the problem of selecting heterogeneous sensors on the region of interest and fusion to improve the detection performance of spectral intrusion at an acceptable cost range[19].For spectrum misuse in dynamic spectrum access scenarios,the authors proposed embedding spectrum license in physical layer,using forward error correction(FEC)coding for spectrum license,and constellation design to realize spectrum misuse detection in which simulation results showed that the proposed scheme can detect spectrum misuse correctly and quickly[20].Similarly,the authors proposed an abnormal frequency detection framework based on crowdsourcing in the dynamic spectrum sharing scenario,which not only has good detection performance for abnormal frequency,but also can effectively locate the source of abnormal frequency [21].At the same time,in order to solve the problem of wireless spectrum anomaly detection,an active detection framework was proposed,in which the detection performance of unsupervised anomaly spectrum was improved by defining the anomaly as an outlier and introducing user feedback [22].In addition,in order to detect spectrum sensing data falsification (SSDF) attacks,the authors proposed a machine learning (ML) framework,which aimed to detect the spectrum anomalies generated by SSDF attacks by using the behavioral fingerprint of devices [23].In order to protect sensor privacy while detecting SSDF attacks,the authors proposed a spectrum sensor intrusion detection system for federal learning(FL),which considers unsupervised ML and system call-based fingerprint,and experimental results demonstrate the effectiveness of the proposed system for SSDF detection[24].In order to improve the timeliness and security performance of MCS system,the authors applied mean-field game and EIGamal encryption to optimize the age of information and protect the privacy of the system,respectively[25].
It is worth noting that the above studies of MCS for spectrum detecting are only limited to the ground spectrum sharing scenario,and have not been used in the inter-satellite spectrum sharing scenario at this stage.In addition,the above MCS detection frameworks rely heavily on a centralized server,which is vulnerable to single point of failure attacks.If blockchain is introduced into the MCS framework,with its decentralization,transparency and traceability,the MCS framework will be more secure and robust[26,27].In general,to the best of authors’knowledge,there is few research on the detection of abnormal frequency behavior in the inter-satellite spectrum sharing scenario.Therefore,it is urgent to construct an abnormal frequency behavior detection framework to safely and effectively detect the abnormal frequency behavior in the inter-satellite spectrum sharing scenario.
1.3 Contributions
Inspired by the above observations,this paper intends to integrate blockchain on MCS for the safe and effective detection of abnormal frequency usage behavior in satellite spectrum sharing system.Specifically,the contribution of this paper can be summarized as:
• In order to enable MCS framework with security attributes,we propose a blockchain-based MCS framework and give its detailed operation flow.
• In order to solve the problem of abnormal frequency behavior detection in satellite spectrum sharing system,we propose a detection framework based on mixed hypothesis testing,and derive a closed expression for abnormal spectrum behavior identification,where false alarm probability is taken as constraint condition to maximize detection probability as optimization criterion to achieve abnormal frequency behavior detection under single and multiple power level scenarios,respectively.
• In order to verify the effectiveness of the proposed scheme,we carry out simulation verification under different parameters,and the results show that the proposed scheme can prevent potential security problems under the condition of realizing abnormal frequency behavior.
The rest of the paper is arranged as follows.In Section II,the proposed framework is summarized and the optimization problems aiming at maximizing detection probability are formulated.In Section III,the proposed optimization problems are solved under single power level and multi-power level,respectively,and the simplified version of the detector is derived in detail.In Section IV,the proposed detection scheme is verified through simulation under several parameters configurations.Section V concludes this paper upon the analysis from Section IV.
II.SYSTEM MODEL AND PROBLEM FORMULATION
2.1 System Overview
As shown in Figure 2,this subsection introduces a blockchain-based MCS spectrum detecting framework for satellite spectrum sharing scenario,which consists of four roles: service requester,service provider,blockchain node,and MWs.The detailed description is as follows:

Figure 2.The proposed MCS framework based on blockchain for spectrum detectiion.
• Service requester: Any individual,company,organization,or operator with a perceived need can be considered a service requester.Typically,it outsources some perception tasks related to execution time and location to MWs for perception,transmission,and analysis.In this paper,since the scenario considered is a spectrum sharing scenario between satellites,the service requester is a satellite earth station,which is worried about interference from other satellites who share its spectrum.However,due to the high mobility of the satellite sharing its spectrum and the directional nature of its signals,it is difficult to monitor its signals on its own.Therefore,it chooses to send the sensing task to the service provider,so as to obtain the transmission power of the relevant satellite,so as to judge whether there is abnormal frequency behavior.
• Blockchain nodes:In the proposed framework,all blockchain nodes together form a service provider to form a trusted third party[28]in the MCS monitoring framework.They are not only responsible for maintaining the operation of the entire blockchain system,but also need to contribute certain storage and computing resources to complete the processing of perception data,so as to correctly determine whether the monitored satellite has abnormal frequency behavior.In addition,they run a consensus mechanism based on detecting ability to make sure the accuracy of the detection,in which blockchain nodes broadcast their global decision to figure out the one who shows the most accuracy detection will generate the next block.
• Service provider: As shown in the Figure 1,traditional MCS systems rely heavily on a centralized server,so they are vulnerable to single point of failure attacks and other security risks.Therefore,in the proposed framework,a large number of blockchain nodes constitute a distributed service provider.In addition,it is responsible for compiling perceptual data processing algorithms into smart contracts for fast and secure execution.
• MWs: All smart devices with sensing and data transmission capabilities,such as UAVs,road side units,vehicles,and smart watches,can be considered MWs,who are responsible for collecting data in specific time,space,and frequency domains and passing the collected perceptual data back to the service provider.
In addition,the implementation of the proposed framework mainly involves the following steps:
1.Identity registration: The SP and all MWs need to call the identity registration function at the blockchain node for identity registration,so as to obtain legal identity information.
2.Pay the deposit: The SR needs to pay a deposit to the SP based on the duration of the perceived task and the contribution of the participant.
3.Release tasks: Upon receipt of a deposit from the SR,SP will notify SR of task release.At this point,the satellite earth station releases the monitoring task to the SP.
4.Assign tasks:SP will assign the perceptual task to MWs in the corresponding area according to the execution location and time of the task.
5.Data upload: After the perceptual data collection is completed,MWs send back the collected data to SP.
6.Data evaluation: The blockchain node will evaluate the perception data based on the compiled smart contract to obtain the corresponding evaluation results.
7.Evaluation forward: The blockchain node will report the resulting evaluation results to the SR,i.e.,the satellite earth station,which will judge whether the secondary satellite has abnormal frequency behavior according to the evaluation results.
8.Residual payment: SR will pay the final payment to SP based on the reported evaluation results.
9.Reward distribution: SP will allocate incentives based on MWs and their own contributions.Noted that this paper focuses on the detection of abnormal spectrum usage,so only Step 5-7 are needed to pay attention to in the rest of this paper.
2.2 Problem Formulation
As shown in Figure 3,this paper considers the problem of satellite anomaly detection in the inter-satellite spectrum sharing system,in which LEO satellite is secondary user and geosynchronous satellite is primary user.First,the secondary satellite reports the frequency requirement to the satellite earth station of the main satellite,and then the satellite earth station sends the corresponding spectrum resources and the formulated frequency rules to the secondary satellite.At the same time,the satellite earth station shares the frequency information of the secondary satellite,including the allocated channel and transmitting power,to SP to help it complete the frequency behavior detecting of the secondary satellite.SP then distributes the monitoring tasks to MWs in the corresponding area.All MWs monitor a certain time slot of the allocated channel and uploads the sensing data to the blockchain node;Finally,according to the perception data reported by MWs,the blockchain node runs the corresponding smart contract,analyzes the perception data,and feedbacks the frequency behavior detection results of the secondary satellite to SR.

Figure 3.The inter-satellite spectrum sharing model.
Therefore,the normal frequency usage state of the secondary satellite can be modeled as[15]:
whereN0andN1indicate that the detected channel is not occupied by secondary satellite or is occupied by secondary satellite withl-level transmitting poweris the m-thsampled signal of MWi,is Gaussian white noise.si(m)is the sampling of the transmitted signal,which is widely modeled as an independent uniformly distributed random process with zero mean and unit variance,i.e,si(m)~N(0,1) [29].h0,iandh1,iare the channel gains from the primary and secondary satellites to the MWi[15],respectively,which can be expressed as
whereh0,i(θ0,i) represents the antenna gain of the satellite at the direction ofθ0,k,withd0,kas the distance between the satellite and the MWi,with propagation factorAgas gaseous absorption andAcas cloud or fog attenuation [15].Agcan be further given byAg=Ao+Aw=0.182fN′′(f),whereAoandAware the specific attenuations due to water vapor and dry air,respectively,andN′′(f)is the imaginary part of the frequency-dependent complex refractivity.What’s more,the specific attenuation within a cloud or fogAccan be represented asAc=KlC,withKl=0.89f/[ε′′(1+η)]as the specific attenuation coefficientη=(2+ε′)/ε′′,ε′andε′′denote the imaginary part and real part of the dielectric permittivityεof waterCrepresents liquid water density in the cloud or fog.
It is worth noting that in most of the literature,the allowable transmission power level is 1,that is,L=1;But in practical applications,for example,referring to standards such as IEEE 802.11[30],secondary satellites are likely to have more than one transmit power level,i.e.L >1.Therefore,the normal spectrum usage needs to consider a variety of frequency usage states,which makes the detection of abnormal frequency usage more complicated.In this paper,we define the transmission power deviation from the predetermined level as an abnormal frequency behavior,which can be modeled as
whereParepresents the abnormal transmission power level of the secondary satellite,andrepresentsN0.In this case,we can measure it by the difference betweenPaandTherefore,in order to detect the abnormal frequency behavior of secondary satellites,we model the detection problem as a binary hypothesis testing problem[31]:
where the original hypothesisO0contains all the normal frequency statesN0,N1,...,NLof the secondary satellite,and the alternative hypothesisO1is equivalent toA.Therefore,it can be seen from(3) that the normal transmission power levelPnof the secondary satellite contains a variety of caseswhile the abnormal frequencyPais distributed among the normal cases but does not belong toPn.
Therefore,all hypothesis tests in (4) are mixed hypothesis tests.However,most of the current detection algorithms are only aimed at simple binary hypothesis testing,and few studies focus on hybrid hypothesis testing.In addition,the above problem also includes the secondary satellite’s diverse normal power levels and unknown abnormal power levels,which greatly increases the detection difficulty.Therefore,the present method cannot be directly applied to the above problems.Therefore,it is necessary to design a suitable and effective detection algorithm for the above problems to correctly detect the abnormal frequency behavior of secondary satellites,so as to promote the spectrum coexistence between satellite systems.
However,in the process of detecting abnormal frequency behavior of secondary satellite,false detection consists of false alarm probability and missed detection probability.Specifically,for the false alarm probability,the MCS detection framework wrongly determines that the secondary satellite has abnormal frequency behavior,which will cause it to suffer undeserved punishment.On the contrary,for the probability of missing detection,the MCS detection framework misses the detection of the abnormal frequency behavior of the secondary satellite and allows it to continue to use the abnormal spectrum.Therefore,it is necessary to design the corresponding detection algorithm to reduce the probability of these two kinds of compromise.
WhenL=1,we first consider the anomaly frequency behavior detection of the single power stage of the secondary satellite,i.e.,the satellite is either not working or working at transmit powerTherefore,(4)can be reexpressed as
Considering that there may be a large difference between normal and abnormal transmission power of secondary satellites,two false alarm constraints,α0andα1,need to be considered.Therefore,forL=1,the detection of abnormal frequency behavior can be modeled as the following optimization problem
Where,Pr(O1|O1)represents the detection probability of secondary satellite abnormal frequency behavior,and Pr(O1|O0) represents the false alarm probability of secondary satellite.In this way,(5) can be equivalent converted into the following three primary hypothesis testing problem

Where Pr(H2|Hj),j ∈0,1,2 represents the probability of being judged asHjwhen the actual state of the monitored channel isH2.
WhenL >1,different from the heterogeneous false alarm constraint of(6),we choose the Neyman-Pearson criterion to maximize the detection probability Pr(O1|O1) under the constraint of false alarm probability Pr(O1|O0).Specifically,the optimization problem can be expressed as follows
III.ALGORITHM DESIGN
3.1 Single Power Level Detection
The Lagrange multiplier method is usually used to solve constrained optimization problems[32].Therefore,in order to maximize the detection probability of abnormal frequency behavior of secondary satellites under heterogeneous false alarm constraints,we have
where y represents the set of perceived data of MWs in a given time slot,andCis the detection threshold.In this way,in order to maximize the detection probability Pr(H2|H2),we have
where y satisfies y∈C.And we can get
However,because the working status and the transmission power of the secondary satellite are unknown,is difficult to obtain directly.Therefore,we consider to characterize the truth value by using the maximum likelihood estimateThen(12)can be further written as
where,parameterλimeets the requirement thatλj=and is decided by false alarm constraint.In addition,due to the presence of secondary satellite abnormal frequency signals in the sampled signal,We useRto represent the decision domain of the abnormal frequency behavior for the test statisticT,which can be expressed as
Therefore,according to the data reported by a single MW,the local judgment of the abnormal frequency behavior of the secondary satellite can be expressed as
SinceTis the sum of squares ofNindependent standard normally distributed variables,it followsT=Therefore,the conditional probability can be obtained by the following equation
According to the above equation,we assume that
By taking the derivative of the above equation with respect toT,and vice versa.At this point,there must exist anη2satisfyingsuch thatg0(η2)+g1(η2)=1.In other words,whenT >η2,T ∈R.Similarly,in the intervalsatisfies>0 andSo,there may be partial decision domain in intervalwhich is highly related to SNROverall,the decision domain of this part is composed of the following cases:
• When SNR is large,the heterogeneous false alarm constraintsα0andα1reach a maximum.By solvingwe can obtain three solutionsη0,η1,η2satisfyingIn this case,the decision domain satisfiesR=[η0,η1]∪[η2,∞).
• When SNR is small,only one solutionη2 can be obtained by solving formulasatisfyingTherefore,local decision domain can be
After the SP makes a local decision about a single MW,it is considered to make a global decision [33-35] about whether the abnormal frequency usage behavior of the secondary satellite occurs through the decision criterionL/K,i.e,
Where,di ∈{0,1}represents the local decision of thei-thMW andLis the global decision threshold.
Similar to the decision criterion for local decisions,the decision criterion for global decisions can be expressed as
whereβ0andβ1are global false alarm probability constraints,0<β0≤α0,0<β1≤α1.βj,j ∈{0,1}denotes the global false alarm constraint and satisfiesβj ≤ αj,j ∈ {0,1}.It is worth noting that since the distance between MWs is much smaller than the distance between MWs and secondary satellite.Therefore,in order to simplify the solution of the global decision,it is assumed that each MW has the same sensing ability,and we have
Therefore,(20) shows that as the decision threshold increases,the false alarm also increases as well as the detection probability.Therefore,according to the decision criterion,the optimal decision threshold should minimize the false alarm constraint to maximize the detection probability.By solving (20),the decision threshold can be expressed asL ≥Lj,j={0,1},where denotes the minimum value that satisfies the corresponding false alarm probability.Finally,the optimal decision threshold isLopt=max(Lj),j ∈{0,1}.According to Algorithm 1,the detection of abnormal spectrum usage at single power level can be accomplished.
3.2 Multiple Power Level Detection
Multiple power level detection refers to the detection when the secondary satellite operates atLdifferent levels of power.For the optimization problem in Eq.(9),we use the likelihood ratio test to maximize its detection probability,which is derived as follows
wherep(y|Pa)andrepresent the probability density function under abnormal and normal frequency behavior,respectively,when perception data is y.represents the conditional probability of the target channel when secondary satellite normally use the spectrum,andλBrepresents the decision threshold determined by the false alarm constraintαin(9).denotes the set of the normal power levels.
The variablePris introduced into the above formula to represent any transmitting power,in which case the conditional probabilitiesp(y|Pa)andcan be expressed as
Obviously,the conditional probabilitiesp(y|Pa)andcan be brought into (21),and a perfect energy detector can be found when the abnormal frequency information is known.However,the abnormal frequency behavior informationp(Pa|O1) is usually unknown,which makes the above detector unavailable.
Therefore,in order to solve the problem of detecting the abnormal frequency behavior of the secondary satellite whenp(Pa|O1)is unknown,we intend to obtain the generalized likelihood ratio detector for unknown behavior by obtaining the maximum likelihood estimate of the unknown parameterPa,which can be obtained by
Then,by inserting ˆPainto(21),the generalized likelihood ratio can be expressed as
For ease of expression,defining the functionwith respect to the test statisticTand the normal power,satisfyingTherefore,the detector can be reexpressed as
Obviously,the above formula can complete the abnormal frequency behavior detection of secondary satellites in the case of multiple power levels,that is,the optimal solution in(9)is obtained.However,under the blockchain-based MCS detection framework,the computation to solve the optimization problem is run on the blockchain node,which aggravates the computational pressure on the blockchain node.Therefore,it is necessary to simplify the generalized likelihood ratio detector.
3.2.1 The BooG Detector
Therefore,a Bad out of Good detector is designed in this paper.Its design principle is to first select the most likely normal power level of the secondary satellite,and then determine whether there is an abnormal frequency behavior.The details are as follows:
First,we apply the maximum a posteriori criterion to find the most likely transmit power from the normal power levels of the secondary satellite:
Then,the generalized likelihood ratio detector in(21)can then be further written as
By simplifying the above equation,we have
Finally,the BooG detector can be denoted as:
3.2.2 Threshold Setting
To facilitate the analysis of the detector’s decision domain,the BooG detector can be further written as
where,for any decision domainRn,it satisfies
wherei,j ∈{0,1,...,N},i=j.
For the decision domainRn,it is important to note that
• When the secondary satellite is in operation,its transmitting powerPr >0;In this case,the variance of MWs’perception data is greater than;Therefore,
Because the test statisticTfollows the Chi-square distribution,sothe detection probability of the anomaly with frequency behavior can be expressed as
Similarly,the false alarm probability can be denoted as
For the BooG detector,we have the following analysis:
• According to the Theorem of large numbers,approaches 1 whenM →∞;
• In order to distinguish each power level of the secondary satellite more accurately,it is necessary to design the spacing between them reasonably.Thus,between any two adjacent extreme points,i.e.,Dl=the BooG detector can be approximately expressed as
For the decision domain between extreme value points,we have
Theorem 1.The intersection between Dl and decision domain can be denoted asif and only if the following equation is satisfied.
where
where
Therefore,we have
where,x0is the smaller solution toλM,and x1is the larger solution toProof.See Appendix.
According to above analysis,if the condition in(36)is not satisfied in the intervalDl,there is no intersection between intervalDland the decision domain.Therefore,when the abnormal spectrum behavior occurs in this interval,it is hard to be detected correctly,which will be verified in the simulations part.
IV.SIMULATION RESULTS AND ANALYSIS
In this section,we verify the effectiveness of the proposed framework through numerical simulation.MWs are randomly distributed within a radius of 3Km with the secondary satellite earth station as the center of the circle.Unless otherwise stated,key simulation parameters are shown as Table 2[4].

Table 2.Key simulation parameters.
As shown in Figure 5 and Figure 6,the influence of secondary satellite height and transmit power deviation on detection performance is given.At a single power level,detection performance increases with the increase of transmit power deviation.This is because the variance of the perceived data of MWs also deviates more and more under normal and abnormal conditions,which leads to improved detection performance.In addition,the lower the altitude of the satellite,the more the perception data of the MW reflects its true state,its detection performance increases.Comparing Figure 5 and Figure 6,it can be seen that the framework proposed in this paper can improve the detection probability of abnormal frequency behavior of secondary satellite,which reflects the superiority of data fusion at SP.In addition,the consensus mechanism based on detection ability further guarantees the detection effect of SP.
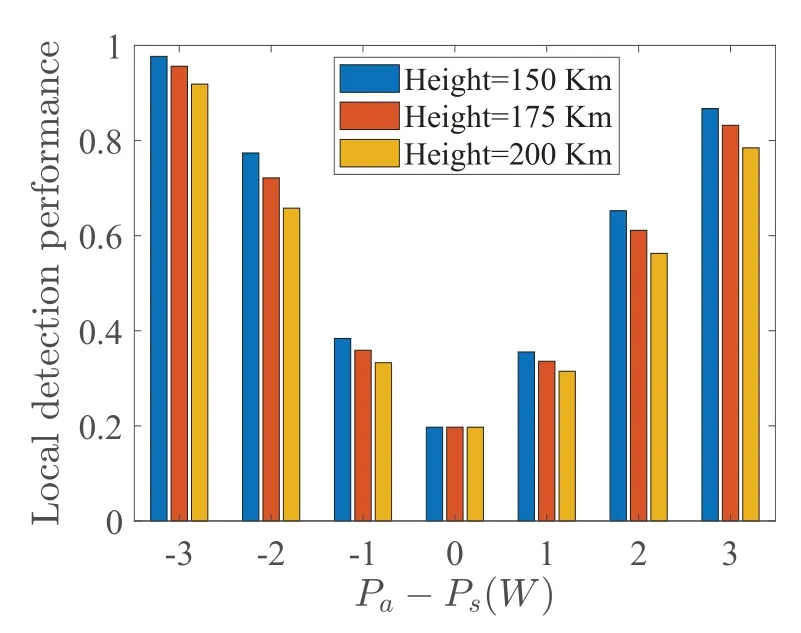
Figure 5.The influence of satellite height and transmit power on the local detection performance.
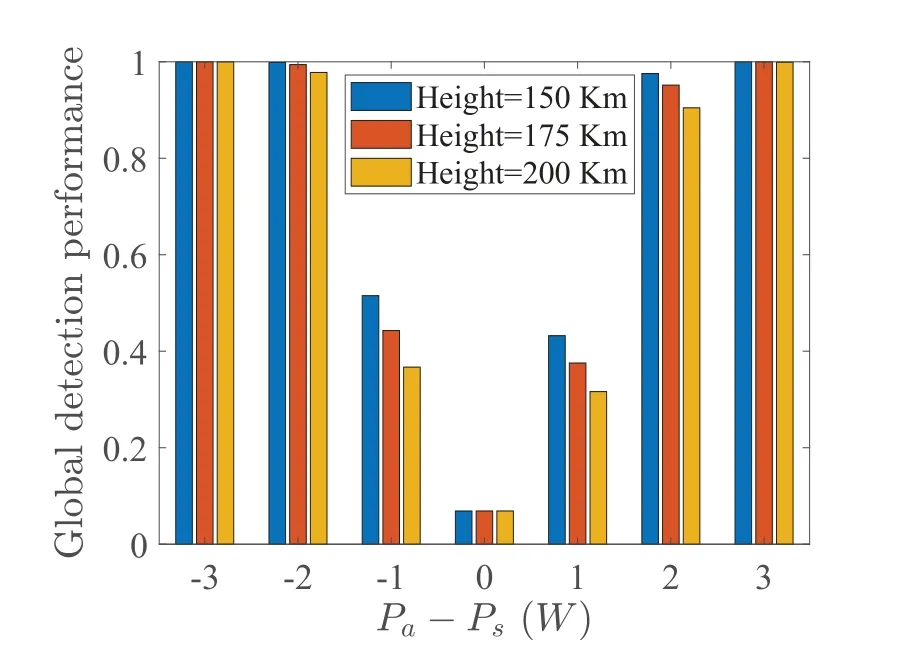
Figure 6.The influence of satellite height and transmit power on the global detection performance.
As shown in Figure 7,the relationship between detection performance and detection threshold under different false alarm constraints at a single power level is given.It can be concluded that there is a compromise relationship between detection performance and detection threshold,that is,the stronger the false alarm constraint,the smaller the global decision threshold,and the stronger the detection performance.Because the number of workers involved in the detection is limited,the global decision threshold basically does not change apparently under some false alarm constraints.

Figure 7.The relationship between detection performance and detection threshold under different false alarm constraints.
As shown in Figure 8,the best detection performance comparison of different detectors under different transmitting power of secondary satellite is given according to the consensus mechanism based on detection ability,where the GLR detector is defined as the baseline.The normal transmitting power of the secondary satellite is defined asIt can be seen that,first of all,for all detectors,in most cases,the greater the gap between the transmitting power of the secondary satellite and the normal power level of the corresponding interval,the better the detection performance.However,when the ratio of the transmitting power of the secondary satellite falls to (5.7),the GLR detector shows the opposite trend,which corresponds exactly to the situation inTheorem 1.That is to say,in this case,the intersection between the decision field andDlis empty or nearly empty.Second,as the secondary satellite baseline transmission power increases,so does the performance of all detectors,because the difference between the different normal transmission powers also becomes larger.Finally,for the two detectors given,the detection performance of the BooG detector is basically behind that of the GLR detector,because the BooG detector only considers the maximum posterior probability to estimate the most likely normal transmission power,thus losing part of the detection performance.However,in the interval(5,7),because the BooG detector estimates the most likely normal transmit power by the maximum posterior probability,F(T)is sharper,resulting in better performance in the interval(5,7).
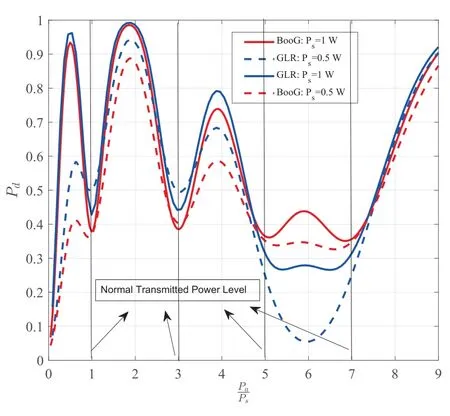
Figure 8.The performance comparison of different detectors under different transmitted power.
As shown in Figure 9,the influence of false alarm constraints on different detectors under different transmitting power is given.It can be seen that,first of all,with the increase of false probability,the detection performance of both detectors increases,this is because the false alarm probability itself is positively correlated with the detection performance.Second,in most cases,the detection performance of GLR is better than that of BooG,because in order to simplify GLR,the BooGie detector only considers the most likely normal transmission power through the maximum posterior probability,so part of the detection performance is sacrificed.However,in the interval (5.7),that is,Pa=6,the intersection of the GLR detector’s decision domain andDlcan be approximated as the empty set.

Figure 9.The influence of false alarm constraints on different detectors under different transmitting power.
As shown in Figure 10,the performance of the forking probability at different MW sizes as well as block sizes is given.It can be seen that for the same block size,the fork probability increases as the MW size increases.Moreover,as the block size increases,the bifurcation probability also increases.Therefore,as long as a certain block size is guaranteed,the network scale of MWs can be increased to improve the detection performance of the MCS framework.

Figure 10.The influence of K on forking probability.
V.CONCLUSION
In this paper,a blockchain-based MCS detection framework is developed to detect the abnormal frequency behavior in the inter-satellite spectrum sharing system.First,we explain in detail how the framework can monitor the abnormal frequency behavior in the spectrum sharing system between satellites.Secondly,under the constraint of false alarm probability,we propose an anomaly frequency detection algorithm based on mixed hypothesis testing to maximize the detection probability in single power level and multi-power level scenarios.Then,in order to reduce the computing pressure of blockchain nodes,a BooG detector is proposed.Simulation results show that the proposed framework can effectively detect abnormal frequency behavior in inter-satellite spectrum sharing scenario.
VI.APPENDIX
Proof.Defining the functiong(x)=xe1-x,we find thatx=1 is the maximum value point ofg(x).Therefore,when it comes tosimilar conclusion can be obtained that whenreaches its maximum value andIn addition,when the functionreaches its minimum value.At this time,we can get
Therefore,there are two relationships between intervalDland the decision domain.
- China Communications的其它文章
- Resilient Satellite Communication Networks Towards Highly Dynamic and Highly Reliable Transmission
- Mega-Constellations Based TT&C Resource Sharing: Keep Reliable Aeronautical Communication in an Emergency
- High-Precision Doppler Frequency Estimation Based Positioning Using OTFS Modulations by Red and Blue Frequency Shift Discriminator
- Energy-Efficient Traffic Offloading for RSMA-Based Hybrid Satellite Terrestrial Networks with Deep Reinforcement Learning
- For Mega-Constellations: Edge Computing and Safety Management Based on Blockchain Technology
- Robot-Oriented 6G Satellite-UAV Networks: Requirements,Paradigm Shifts,and Case Studies

