Security analysis of access control model in hybrid cloud based on security entropy①
Che Tianwei (车天伟)
(*The School of Computer Science and Technology, Xidian University, Xi’an 710071, P.R.China)(**The School of Computer Science and Technology , Northwestern Polytechnical University, Xi’an 710129, P.R.China)(***The PLA information Engineering University, Zhengzhou 450001, P.R.China)
Security analysis of access control model in hybrid cloud based on security entropy①
Che Tianwei (车天伟)②
(*The School of Computer Science and Technology, Xidian University, Xi’an 710071, P.R.China)(**The School of Computer Science and Technology , Northwestern Polytechnical University, Xi’an 710129, P.R.China)(***The PLA information Engineering University, Zhengzhou 450001, P.R.China)
To resolve the problem of quantitative analysis in hybrid cloud, a quantitative analysis method, which is based on the security entropy, is proposed. Firstly, according to the information theory, the security entropy is put forward to calculate the uncertainty of the system’s determinations on the irregular access behaviors. Secondly, based on the security entropy, security theorems of hybrid cloud are defined. Finally, typical access control models are analyzed by the method, the method’s practicability is validated, and security and applicability of these models are compared. Simulation results prove that the proposed method is suitable for the security quantitative analysis of the access control model and evaluation to access control capability in hybrid cloud.
hybrid cloud, security entropy, classificatory access control model, directly unauthorized access, right about access, indirectly unauthorized access
0 Introduction
The key to access control model security proof is to find a recognized and self-evident security axiom, and then based on this security axiom, to deduce, or prove the security assumptions proposed in the model by means of this security axiom, so as to make it more reliable. However, even the proven Bell-La Padula(BLP) model[1,2]can’t prove the rationality, completeness and safety of “simple security axiom” and “ *-property axiom” that it proposed. So, some scholars point out that the security axioms in BLP cannot completely prove the security of BLP[3]. A complete access control model must clearly tell us which security requirements should be met, which access violation would be prevented, and how to reduce and prove the uncertainty of the access violation that the hybrid cloud allows.
Entropy is a tool of measuring uncertainty, which was originally used in thermodynamics. Shannon introduces it to the information theory, and puts forward the concept of information entropy for disordered degree of information[4]. Since the information entropy theory is proposed, it has been applied in many fields such as engineering science and social science. Some scholars have successfully introduced it into the quantification analysis of information security risk and event uncertainty[5-7].
This study, based on the thought and method that information entropy measures the uncertainty of things, puts forward the concept of security entropy, and by means of it, measures the uncertainty of system’s response to access violations, which provides a scientific quantitative method for the safety analysis of classificatory access control model.
1 security entropy
Clouds and large data have become the mainstream mode of service to enhance customer service quality, this service model is facing some security risks such as loss and leakage of user data. In order to meet the access control demand for cloud services, especially the access control requirement for multi-level cloud services to coexist user data of different grades and categories of cloud services at the same time, the access control should be able to support different security strength and support the joint control of different intensities between access control models, which is different from the traditional access control method. A quantitative method is presented for security requirements and security access control model assessment to meet the needs of multi-level cloud security assessment service access control model.
1.1 Definition of security entropy
In the cloud system, when a user sends an access request, the system will respond: to allow or to deny. And this response is the only one. To allow or to deny should not appear simultaneously. In addition, the access request is divided into two types: legal request and illegal request. If the system is seen as a black box, the system will give four kinds of response to user’s each access request, that is, “allow legall access”、“refuse legall access”、“allow access violation” and “refuse access violation”. Obviously, the response can be considered as a basis for judging if a system is good or bad. The more the denial responses to legitimate access gets, the poorer the system availability is. The more the allowable responses to violation access gets, the worse the system’s confidentiality is.
In order to comprehensively measure the uncertainty of system’s response to various access requests, the security entropy is defined as follows:
Definition 1(security entropy) : If a group of access request B=b1,b2,…,bqis seen as the input, the system’s request responses to each access result as the object of study, and variable X as this response results, then the value of X will be :to allow legitimate access, to deny legitimate access, to allow illegal access, and to deny illegal access, which is recorded as a1,a2,a3,a4respectively. If Symbol p(ai) stands for the statistical probability of ai, the probability space [X, p(X=ai)] of X will be
Assigning weight wi, the impact factor of the system security, for each response result, the greater wiis, the higher the ai‘s influence to system safety is, otherwise the smaller the ai‘s influence is. If the distribution of wiis
the security entropy of X will be
(1)
1.2 The meaning of safety entropy
According to the common sense of information security, response a2gives negative effects on the usability of the system, and response a3gives negative effects on the confidentiality of the system, while response a1and a4have less influence on system security. Therefore, if we let w2, w3w1, w4, the meaning of safety entropy in Eq.(1) is the average uncertainty of the happened harmful responses. The bigger the value of security entropy is, the more the harmful response uncertainty is; the smaller the value of security entropy is, the less the response uncertainty is. As for the same set of access request, the smaller the security entropy of different access control model is, the less the possibility that model makes harmful response is.
If w2>0,w3>0,w1=w4=0, and w2+w3=1, security entropy is the ground on which the system satisfies usability and confidentiality. If w2=1,w3=w1=w4=0, security entropy of Eq.(1) will be the ground on which the system satisfies usability. If w3=1,w1=w2=w4=0, security entropy of Eq.(1) will be the ground on which the system satisfies confidentiality.
The number of the four responses is related to the number of input samples. If all input samples are legitimate accesses, a3and a4will be 0, and if all input samples are illegal access, a1and a2will be 0.In order to make the safety entropy reflect the system security accurately, the input samples must be complete. In addition, the responses are related to the number of input samples. If an input number of the access request is much more than others, the response will be distorted
Therefore, when security entropy is calculated, the input samples (access requests) must be complete and its probability distribution must be uniform.
The smaller the security entropy is, the less uncertainty of the harmful response that system does is, the more the security of the model is. When the security entropy approaches 0, then the model will achieve the theoretical security.
1.3 Security entropy of different types of illegal accesses
Whether an access is illegal is related to security requirements. According to the access control requirements in national grade of protection standard GB17859-1999[8], illegal access can be classified into three types: directly illegal access, right about access, and indirectly illegal access. The directly illegal access refers to explicitly violating the authorized strategy such as the access control matrix and so on.
The right about access refers to the one which leads to violating information flow direction that the system stipulates, in other word, the one which leads information flow from high class to low class. The indirectly illegal access refers to the one that violates the authorized strategy through information indirect transmission.
For instance, there are two users(s1、s2) and two resourses (o1、o2) in the hybrid cloud, and the relationship of security level is f(s1)▷f(s2)▷f(o1)=f(o2), the authorized strategy of the system is that “s1 read o2”, “s2 read o1”, “s2 write o2”.
Let us see the following four events: b1: s2 read o1,b2: s2 write o2,b3:s1 read o2,b4:s1 read o1.Because b4 explicitly violates the authorized strategy, b4 is therefore directly illegal access, and the sequence of access b1b2b3 causes the information to flow from s1 into o1, which equals that s1 read o1 indirectly. Therefore b1b2b3 is indirectly illegal access. b1 and b3 cause the information flowing to the violation of the direction made by the system, so b1 and b3 are right about access.
For the different types of illegal access, the meaning of Eq.(1) is different. If the illegal access is defined as “directly illegal access”, the security entropy of Eq.(1) is called “direct security entropy” recorded as HD(X).
Again, if the illegal access is defined as “right about access”, the security entropy of Eq.(1) is called “mandatory security entropy” recorded as HM(X). If the illegal access is defined as “indirectly illegal access”, the security entropy of Eq.(1) is called “indirectly security entropy” recorded as HI(X).
2 Safety conditions of classificatory access control model
2.1 Security attributes based on security entropy of safety
w2>0,w3>0,w2+w3=1。
Theorem 1 (direct safety of access control model): Access control model has direct safety, if and only if
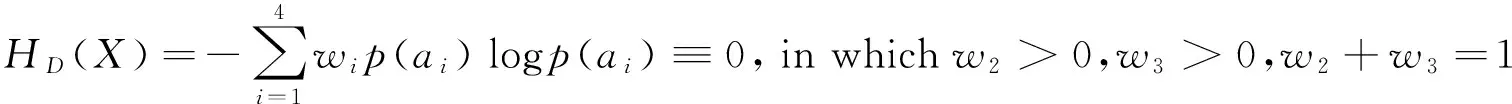
Prove:
It is proved that when HD(X)=0, the event “refuse legal access” and “allow access violation” will never happen, that is, p(a2)=p(a3)=0.
The total number of aiis made as ni(i=1,2,3,4), n1+n2=s, n3+n4=t. Because a1、a2and a3、a4are different responses to the same access, p(a1)+p(a2)=s/(s+t), p(a3)+p(a4)=t/(s+t).
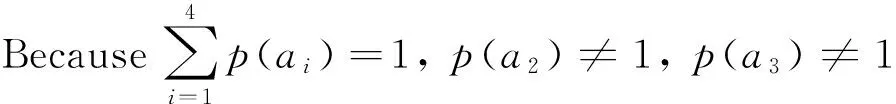
Because w2>0,w3>0,w2+w3=1, so w1=w4=0。
End.
Similarly, theorems could be got as follows:
Theorem 2 (mandatory safety of access control model): the access control model has mandatory safety, if and only if
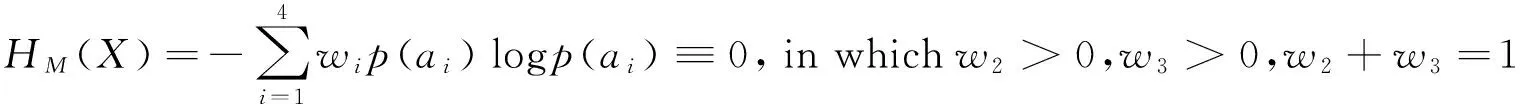
Theorem 3 (indirectly safety of access control model): the access control model has indirect safety, if and only if
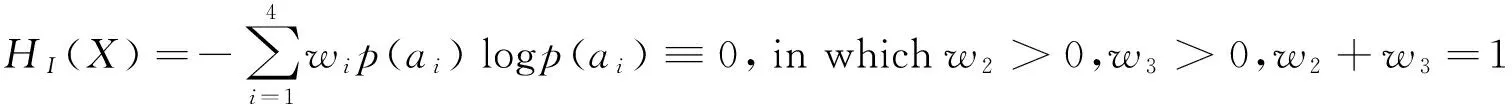
2.2 Safety theorem of classificatory access control model
Symbol Θ2represents class 2 access control model, Θ3represents class 3 access control model, and Θ4represents class 4 access control model.
Now, according to safety needs of class 2、3、4 information system, the safety theorem of classificatory access control model based on the above security attributes is put forward.
Theorem 4 (safety of classificatory access control model):,Class 2 access control model Θ2satisfies safety needs, if and only if HD(X)|Θ2≡0, in which w2>0,w3>0,w2+w3=1; Class 3 access control model Θ3satisfies safety needs, if and only if HD(X)|Θ2≡0 and HM(X)|Θ3≡0, in which w2>0,w3>0,w2+w3=1; Class 4 access control model Θ4satisfies safety needs, if and only if HD(X)|Θ4≡0、HM(X)|Θ4≡0 and HI(X)|Θ4≡0, in which w2>0,w3>0,w2+w3=1;
3 Analysis of typical access control model based on security entropy
Now, the theory is applied to analyze the security of typical access control model, verify the practicability of this method, and point out the defect of these access control models.
3.1 Security analysis to HRU model
3.1.1 Direct safety
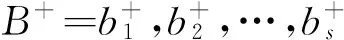
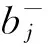
The statistical probability distribution of responses is
Since HD(X)|HRU≡0, model HRU can satisfy direct safety.
3.1.2 Mandatory safety
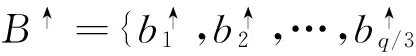
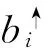
3.1.3 Indirect safety
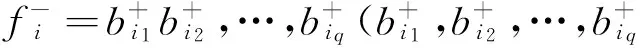
HI(X)|HRU>0, which shows that the HRU model doesn’t satisfy indirect safety.
The above analysis shows that, model HRU satisfies direct safety, and doesn’t satisfy mandatory safety and indirect safety.
3.2 Security analysis to BLP
3.2.1 Direct safety and indirect safety
Model BLP uses two methods: DAC and MAC in which, DAC uses the HRU model, so the direct safety and the indirect safety of the BLP model coincide with that of HRU, that is, BLP satisfies direct safety and doesn’t satisfy indirect safety.
3.2.2 Mandatory safety
So, HM(X)|BLP≡0, which shows that BLP satisfies mandatory safety.
3.3 Security analysis to RBAC
Model RBAC[9-11]assigns roles for users, and then based on these roles grants authorization. The RBAC’s rights management and access control manner are similar to HRU’s. so its safety is similar to that of HRU, which is, satisfying direct safety and not satisfying mandatory safety or indirect safety.
3.4 Security analysis to FGBAC
FGBAC[12]is the improved BLP, which introduces the information flow graph as a judgment auxiliary tool. In FGBAC, any directly illegal access, right about access and indirectly illegal access will be refused. So
HD(X)|FGBAC=HM(X)|FGBAC=HI(X)|FGBAC≡0
It shows that the model satisfies direct safety, mandatory safety and indirect safety.
According to the above safety analysis of the typical access control model, and in the light of the safety needs of 2、3 and 4 class systems, it is concluded the typical model’ security and applicability are Table 1 and Table 2.
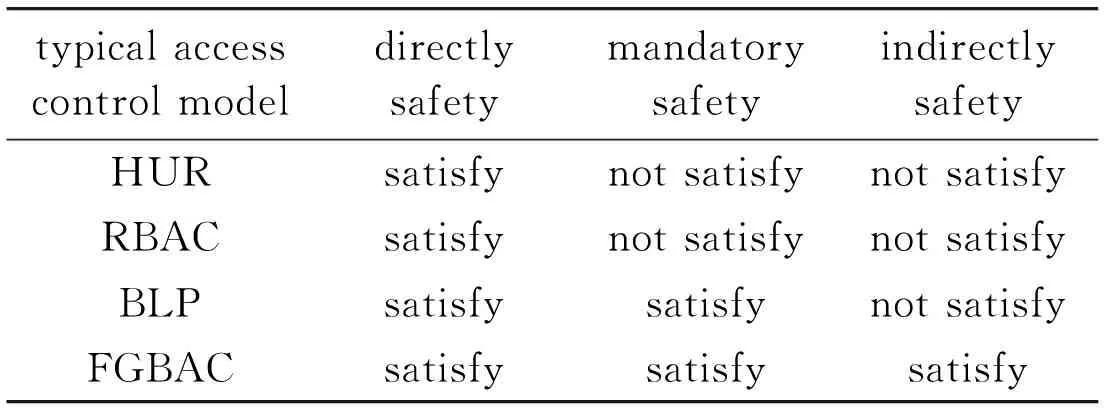
Table 1 The security of typical access control model

Table 2 The applicability of typical access control model
In the simulation environment of achieving the RBAC, BLP and FGBAC models, the rationality of this method is tested. In the simulation environment, 30 users and 200 text types of resources have been. Through user behavior simulation program automaticly and randomly generated user access and randomly modified on three models of security rules and procedures, three audit tracking programs are established recording the determination result of each model. the security entropy is calculated according to the execution result shown in Table 3.
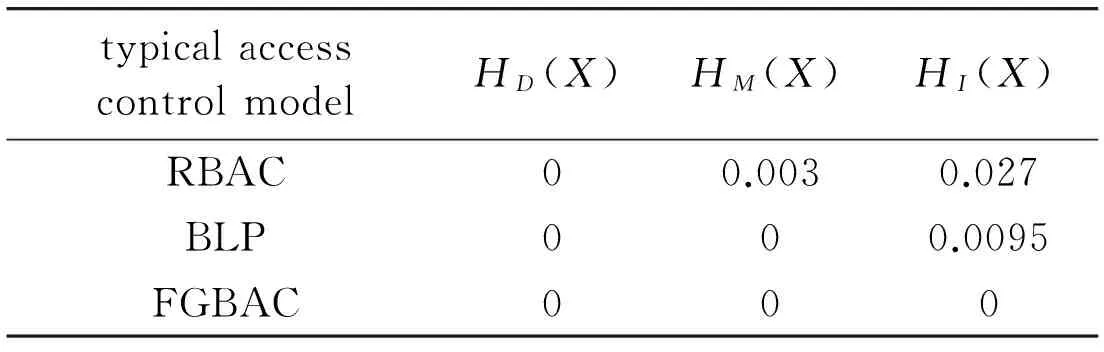
Table 3 The security entropy result of typical access model
4 Conclusion
This study puts forward the concept of “security entropy” for measuring uncertainty of system’s response to access request, and proposes its security theorems based on security entropy. The theory can be widely applied to security analysis of access control mode and system.
Based on the theory,this work analyses the typical access control model, verifies the practicability of the method, and concludes the security and application scope of the available models.
Reference
[ 1] Bell D E, Lapadula L J. Security Computer Systems:Mathematical Foundations and Model. Bedford:Mass Mitre Corp,1973. 66-79
[ 2] David E B. Looking back at the bell-La Padula model. In: Proceedings of the 21st Annual Computer Security Applications Conference, Tuscon, USA, 2005. 337-351
[ 3] Si T G, Tan Z Y , Dai Y Q. A Security Proof Method for Multilevel Security Models. Journal of Computer Research and Development, 2008,45(10): 1711-1717 (in Chinese)
[ 4] Fu Z Y. Information Theory—Fundamental Theory and Application. Beijing: Press of Electronics Industry,2007 (in Chinese)
[ 5] Wang G B, Huang H Z, Zhang X L. Risk Possibility Number——A New Model for Risk Evaluation and Prioritization Based on Maximum Entropy Theory. Acta Aeronautica Et Astronautica Sinica, 2009,30(9):1684-1690 (in Chinese)
[ 6] Fu Y,Wu X P,Ye Q,et al. An Approach for information Systems Security Risk Assessment on Fuzzy Set and Entropy-Weight. Acta Electronica Sinica, 2010,38(7):1490-1494(in Chinese)
[ 7] Zhao D M,Ma J F,Wang Y S. Model of fuzzy risk assessment of the information system. Journal on Communications, 2007, 28(4):51-56 (in Chinese)
[ 8] GB/T 17859-1999. Classified Criteria for Security. Beijing: Standards Press of China,1999 (in Chinese)
[ 9] Peter J. Third Generation Computer Systems. Computer Surveys, 1971,3(4):175-216
[10] Sandhu R S, Coyne E J, Feinstein H L. Role-based access control models. IEEE Computer, 1996,29(2):38-47
[11] Zhai D G, Xu Z,Feng D G. Violation of static mutual exclusive role constraints in dynamic role transition. Journal of computer research and development, 2008, 45(4):677-683(in Chinese)
[12] Wang C, Chen X Y, Li N. An access control mode based on information flow graph. In: Proceedings of the International Conference on Computational Intelligence and Security, Sanya, China, 2011. 998-1000
Che Tianwei, born in 1971,He received his Ph.D. in Computer Science and Technology School of Xidian University in 2014. His main research interests include computer architecture, information security, grid computing systems.
10.3772/j.issn.1006-6748.2015.02.012
①Supported by the National Natural Science Foundation of China (No. 60872041, 61072066) and Fundamental Research Funds for the Central Universities (JYI0000903001, JYI0000901034).
②To whom correspondence should be addressed. E-mail: tianweiche@163.com Received on Jan. 28, 2014*, Ma Jianfeng*, Li Na**, Wang Chao***
 High Technology Letters2015年2期
High Technology Letters2015年2期
- High Technology Letters的其它文章
- Research on suppress vibration of rotor misalignment with shear viscous damper①
- RF energy harvesting system for wireless intraocular pressure monitoring①
- A method for retrieving soil moisture from GNSS-Rby using experiment data①
- Design and development of real-time query platform for big data based on hadoop①
- Multi-sensor federated unscented Kalman filtering algorithm in intermittent observations①
- Improving wavelet reconstruction algorithm to achieve comprehensive application of thermal infrared remote sensing data from TM and MODIS①
