Three-party reference frame independent quantum key distribution protocol∗
Comfort Sekga and Mhlambululi Mafu
Department of Physics and Astronomy,Botswana International University of Science and Technology,P/Bag 16,Palapye,Botswana
Keywords: three-party reference frame independent,quantum key distribution,finite-size key security
1. Introduction
Quantum key distribution (QKD) provides the information-theoretically secure communication by exploiting the laws of quantum mechanics to detect an eavesdropper.[1]Since the inception of the primitive BB84 protocol,[2]much effort has been directed towards achieving large-scale practical implementation of QKD in the past decades. Impressively,QKD has made various advances both in theory and experiment, and commercial QKD systems have become available on the market.[3,4]Moreover, practical implementations have also been reported in various countries, for example, during the 2010 World Cup in South Africa,[5]installations in fiber networks at metropolitan areas[6–9]as well as in satellite QKD communications.[10–13]These examples demonstrate that QKD will be vital in securing the next generation of digital communications. Despite these achievements,in practice,several challenges need to be addressed to bridge the gap between theoretical assumptions in security proofs, and actual implementations.[14]To address some of these challenges, a novel protocol capable of overcoming the rate-distance limit of QKD without quantum repeaters was proposed,which is a promising milestone in extending the range of secure quantum communications.[15]Moreover, high dimensional encoding via exploitation of orbital angular momentum has been explored to increase the key generation rates.[16–18]One of the challenges in the practical implementation of QKD is the requirement for an aligned reference frame between the communicating parties.[19]For instance,alignment of polarisation states for polarising encoding and interferometric stability for phase coding. These requirements have proven difficult to be satisfied owing to unstable fiber communication links and imperfections in the measuring devices leading to unknown and varying reference frames and subsequent detrimental effects on the received states.[20]Effort to tackle potential reference frame misalignment by encoding qubits with larger systems requires the creation and manipulation of many photon entangled states that are very difficult to generate and very sensitive to losses.[21–23]Fortunately, the reference frame independent (RFI) protocol was proposed by Lainget al.[19]to address this problem of alignment. Since inception of the RFI protocol, outstanding results have been achieved both theoretically[24–30]and experimentally,[20,31–33]thus demonstrating its capability to achieve higher secure key rate under a varying reference frame.
In this work,we widen the reach of QKD by considering the RFI protocol employing the two-qubit entangled photons to establish a secret key between three communicating parties. We demonstrate that the number of communicating parties can be further extended and still achieve a secret key rate and transmission distance comparable to the traditional twoparty QKD.We also demonstrate the feasibility of multipartite QKD and its potential for achieving global-scale quantum networks. It has also been shown that multipartite QKD schemes are robust in some noise regimes,[34]thus rendering them secure compared to generating a multipartite secret key via many independent bipartite protocols. Moreover,we provide a composable finite-key analysis for the proposed three-party protocol implemented with decoy states based on entropic uncertainty relations. The entropic uncertainty relations is a direct and robust method for quantifying the amount of information held by communicating parties and the eavesdropper.This method also provides tight bounds on the secret key rates obtained from finite resources and avoids estimates compared to pre-existing approaches such as post-selection technique[35]and de Finetti theorem[36]which provide pessimistic finite key rate estimates.
Moreover, our security analysis considers implementation with decoy states, making our proposed protocol robust against photon number splitting(PNS)attacks.[37]This allows us to demonstrate unconditional security against general attacks under practical conditions where a source produces multiple photons. To account for statistical fluctuations in the finite regime, we employ the tail inequality for random sampling without replacement,and multiplicative Chernoff bound proposed in Ref. [38], which provides the tightest bounds on expected and observed values. A large-deviation Chernoff bound[39]is another pre-existing method used for statistical analysis,which is equally rigorous as multiplicative Chernoff bound but fails to produce tight bounds on observed values in the high-loss regime leading to a rapid decrease in the achieved secret key rate. The Gaussian analysis method[40]is also comparable to multiplicative Chernoff bound. However, it is not rigorous as it is only limited to independent and identically distributed random variables. The tail inequality for random sampling without replacement provides the tightest bounds on observed error rates and avoids inequality scaling compared to pre-existing methods used in Refs.[39,41]. This article is organized as follows. In Section 2,we describe the operation of our proposed protocol,and in Section 3,we derive the asymptotic key rate formula against collective attacks. In Section 4,the finite-size key analysis with decoy states is presented,and in Section 5, we discuss the simulation results. Lastly, concluding remarks are provided in Section 6.
2. Operation of the proposed protocol
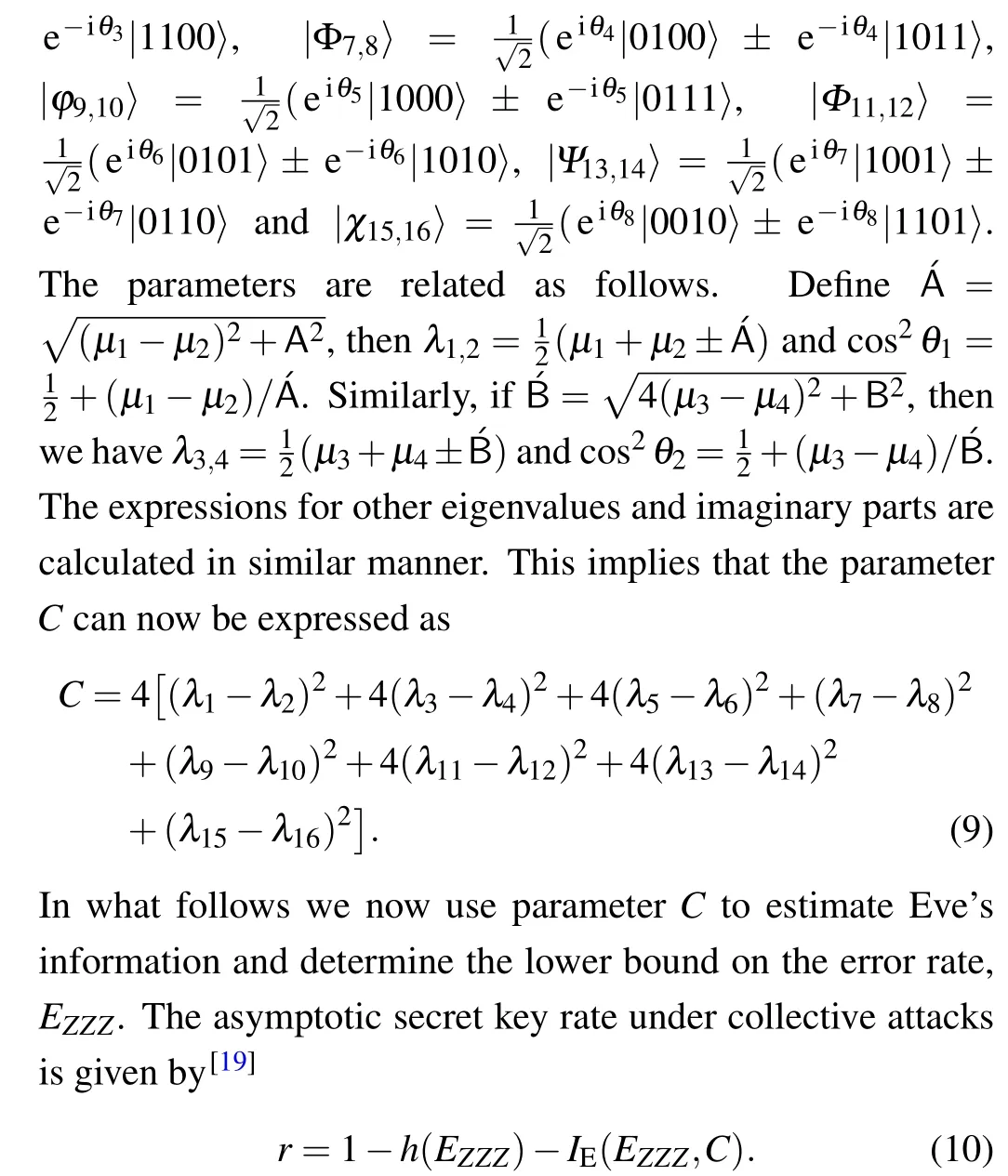
Alice starts by preparing two-photon entangled state using a spontaneous parametric down-conversion (SPDC)source. She then applies polarization modulation in these entangled photons using the same basis chosen from three Pauli encoding basesX,Y,andZ. The two photons are sent to communicating parties, Bob and Charlie, via insecure quantum channels. Upon receipt of photons, they (Bob and Charlie)measure them using any of the three randomly selected measuring bases,{X,Y,Z}to guess the Alice preparation basis. In this protocol,Alice,Bob,and Charlie share a common aligned measurement basisZA=ZBandZA=ZCwhile other measurements basesXandYare allowed to slowly vary by an arbitrary angleβ(see Fig.1). Due to the drift in reference frames,the measurement bases complementary to theZbasis is given by
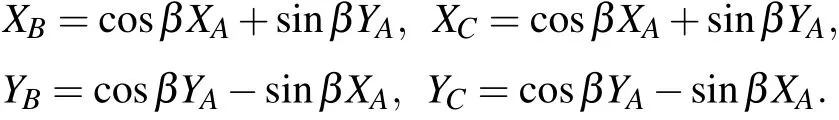
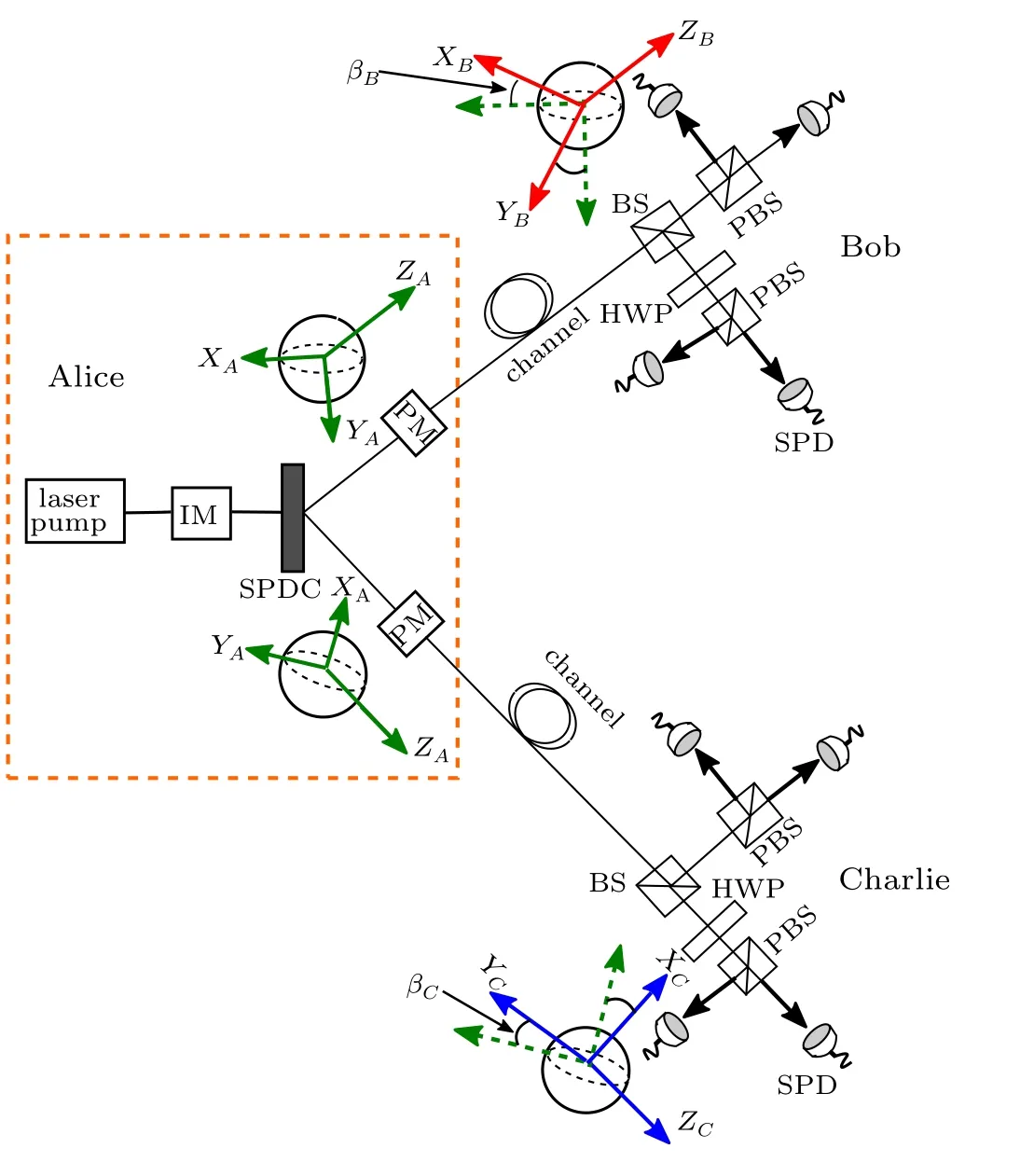
Fig.1. The schematic diagram of the three-party RFI-QKD protocol. Alice starts by preparing an two-photon entangled state using a spontaneous parametric down-conversion (SPDC) source. Next, the two photons are modulated into polarized states belonging to three bases {X,Y,Z} using polarization modulator (PM) and sent to Bob and Charlie through an insecure channel. The photons prepared in the X and Y basis experience misalignment by degree βB and βC for Bob and Charlie,respectively. The acronyms IM, BS, PBS, HWP, and SPD, stand for intensity modulator, beam splitter, polarizing beam splitter, a half-wave plate, and single-photon detector,respectively.
We consider the asymmetric basis choice in which theZbasis is chosen with probabilitypz>1/2 and the complementary bases,{X,Y}with probabilitypc=1−pz.[42]The three parties uniformly choose a random bitri ∈{0,1}to encode information for their chosen basis.The first steps of the protocol are repeated until they have exchanged enough qubits for the sifting process. Alice, Bob, and Charlie announce their basis choices over an authenticated classical channel and proceed with parameter estimation. The raw key is extracted from the cases where Alice prepared her states in theZbasis while Bob and Charlie measured their received qubits in theZdirection.Therefore,the quantum bit error rate is given by

whereZArepresents that Alice sends the two states prepared in theZbasis whileZBandZCdenote that Bob and Charlie measure received states in theZdirection, respectively. The measurement results in the complementary bases are used to estimate the information that has leaked to Eve. The information is bounded by the statistical quantityCdefined as

where〈ΓAΓBΓC〉(withΓ ∈{X,Y})corresponds to the expectation that Alice prepares two states in the basisΓAwhile Bob and Charlie measure received states in basisΓBandΓC,respectively. Furthermore, it can be shown thatCis independent of the valueβwhen substituting the relationsXB,YBandXC,YCin Eq.(2).However,to get an accurate estimate ofC,the angleβis assumed to vary slowly in time short enough to allow for the exchange of key.
3. Security analysis

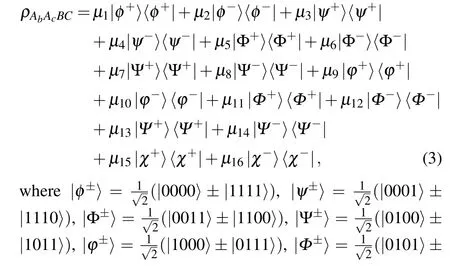

To estimate Eve’s information,IE, the eigenvaluesλihave to satisfy the condition: ∑λi=1 and yield the measured valuesEZZZandC. Since the key is obtained from the measurements in computational basis, this impliesλ1+λ2=1−EZZZandλ3+λ4+λ5+λ6+λ7+λ8+λ9+λ9+λ10+λ11+λ12+λ13+λ14+λ15+λ16=EZZZ.
The following parametrization is chosen to satisft the above conditions:



4. Implementation with decoy states
We extend our security analysis to accommodate imperfections in the state preparation devices. In practice,the secret key is generated by using a spontaneous parametric downconversion (SPDC) source, which occasionally emits more than one photon. The signals produced by this source contains photons whose probability distribution is given by

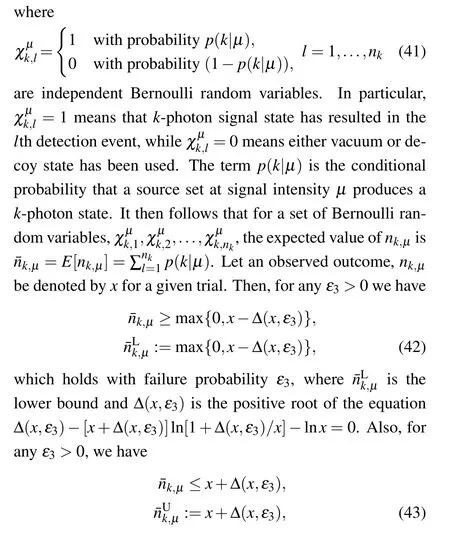
wherekis the number of photons andγis the average intensity of the laser source.[44]Therefore, to combat PNS attack Alice randomly prepares the photons using three different intensities(µ,ν,ω),whereµis the intensity for signal states,νfor decoy states,andωfor vacuum states.[40]The three intensities are usually selected with the probabilitiesPµ>Pν>PωwherePµ,PνandPωcorrespond to the probabilities for signal,decoy and vacuum states, respectively. The photons are sent to Bob and Charlie,who measures the received pulses in three bases{Z,X,Y}. The signal states obtained with intensityµare used for generating the final key, while decoy states acquired from the intensityνare for bounding Eve’s knowledge to the key. In the proposed protocol, Alice measures all the signal pulses,(µ)in theZbasis,and weak decoy pulses,νin all bases{X,Y,Z}. The key generation rate is given by

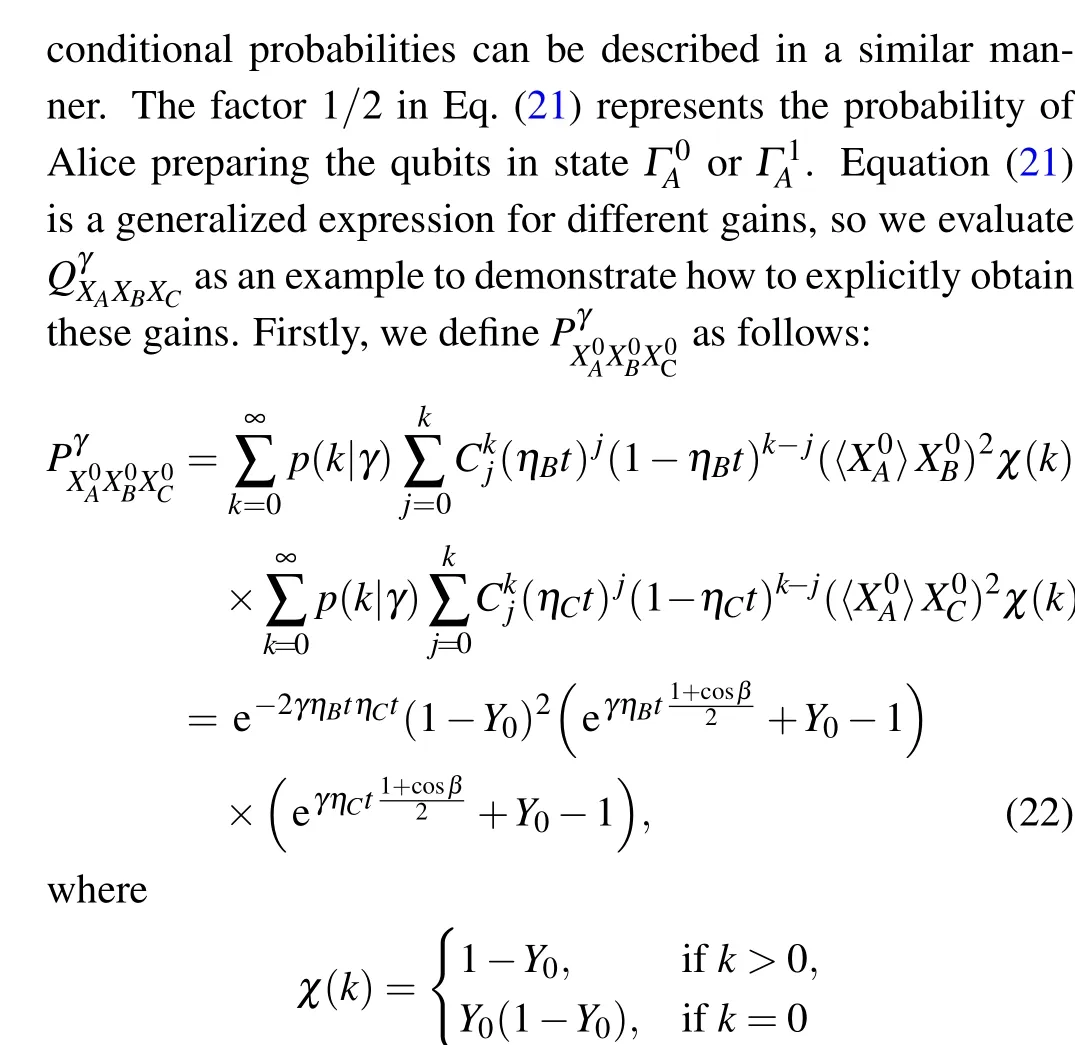
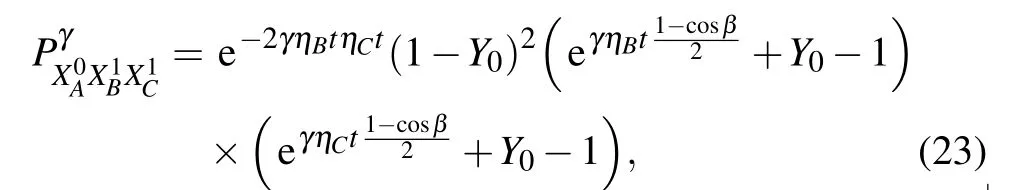


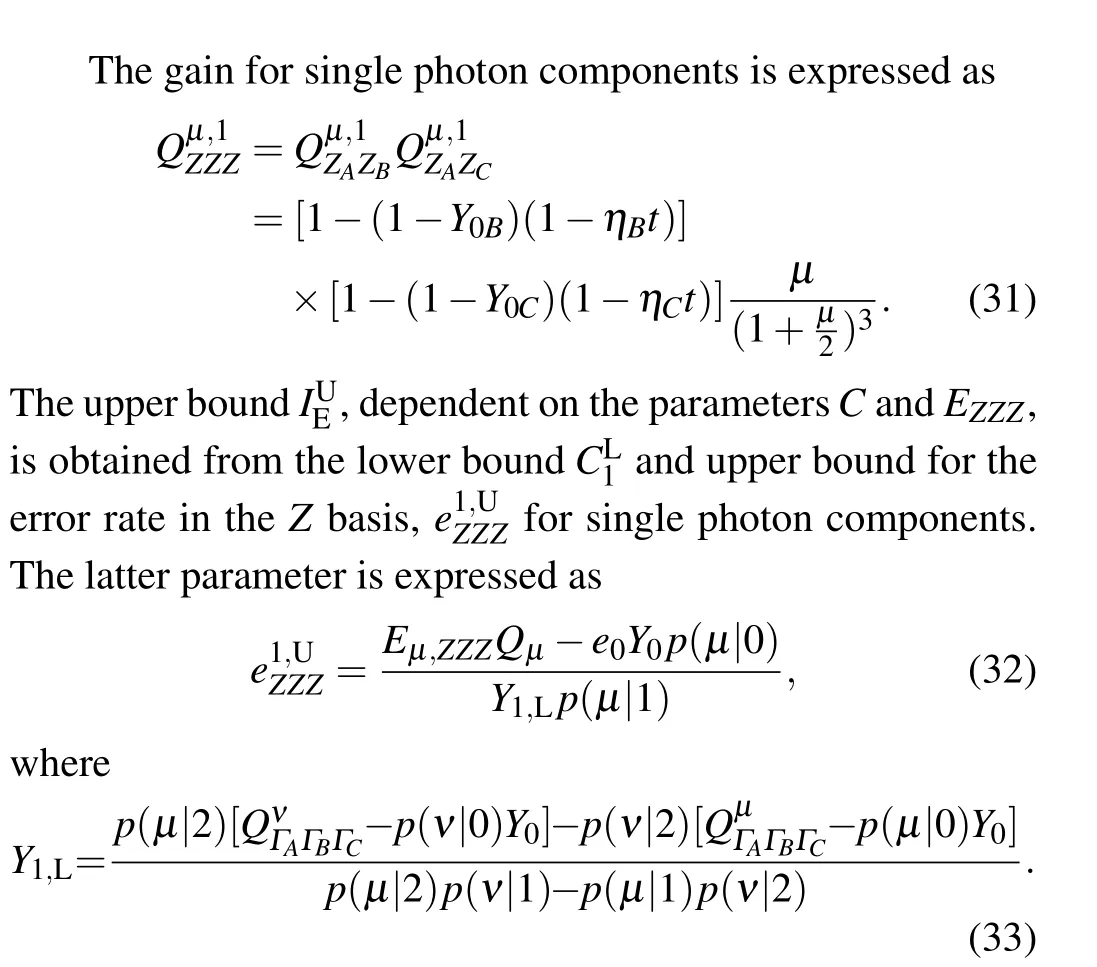
denotes the probability of valid detection events conditional onk-photon states. The other conditional probabilities are analogously obtained as In the above equation,p(γ|k) is the probability that signals generated with intensityγ ∈{µ,ν}containkphotons. The lower bound ofCfor single-photon states can be obtained in terms of error rates from measurements in the complementary bases as
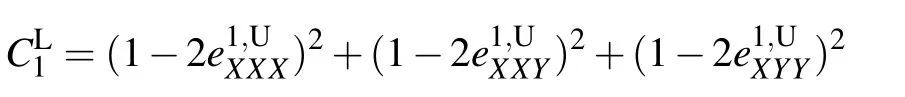


4.1. Finite security analysis
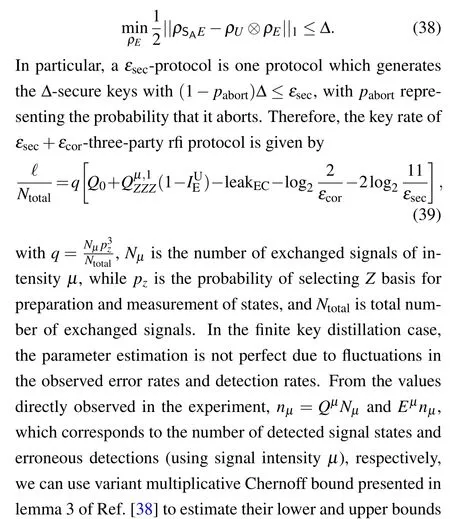
We provide a security proof under a realistic scenario where the communicating parties exchange a finite number of signalsNand subsequently account for statistical fluctuations due to finite-size effects. Our security analysis is sketched along the lines presented in[38,39,46–48]based on universally composable framework. Firstly, we point that the three-party RFI protocol generates a triplet of key bit strings SA,SBand SCfor Alice, Bob, and Charlie, respectively. The key bit strings are of the lengthℓand subject to satisfying the correctness and secrecy criteria for the protocol to be deemed secure. Under the composability criteria, a QKD protocol is regarded correct, if SA=SB=SC, for any given attacking strategy by an eavesdropper. Therefore, anεcor-correct protocol is invariant from the correct one by a small error probability,εcor, i.e.,Pr[SA/=SB/=SC]≤εcor. Furthermore,the secrecy conditions are defined as follows: LetρEbe the state of a quantum system containing the information acquired by an eavesdropper during the execution of a QKD protocol. The correlation of Alice’s key bit string SAwith Eve’s quantum stateρEcan be described by classical-quantum state,ρSAE. There is no correlation between Eve’s system and Alice’s key bit string in an ideal case,i.e.,ρU ⊗ρEwhereρUis a completely mixed state on the keyspace. The classical-quantum state,ρSAEis said to be ∆-secret if


where ˆδis the positive root of equation ¯n1,µ[ˆδ+(1−ˆδ)ln(1−ˆδ)]+ln ˆε2=0. The observed lower bound ofn1,µis given by the upper tail of lemma 2 with failure probabilityε2. The tail inequality for random sampling without replacement is exploited to provide an upper bound for the observed error rates from the expected error rates. The method is described in lemma 1 of Ref.[38]as follows.
Lemma 1[38]For a givenn+mstring of binary bitsχn+m{x1,x2,...,xn+m}, letχmdenotes a random sample(without replacement)of sizembit strings andχnrepresents a random sample of the remainingnbit string. Then, forλmandλn,the probabilities of observing bit 1 value in stringχmandχn,respectively,it holds that for any∊>0
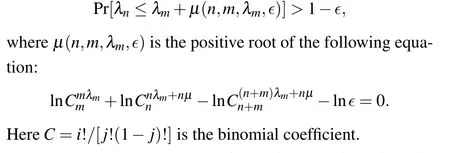
We can use Lemma 1 to estimate the upper bound on observed error rates in theZbasis,eZZZby considering a thought experiment picture where ann+mstring of bits correspond to compatible measurements made by Alice,Bob and Charlie in theZbasis. If the observed average error rate obtained frommrandom bit strings is ¯eZZZ=∑mi=1rZ,A ⊕rZ,B ⊕rZ,C(rZ,A,rZ,BandrZ,Care Alice, Bob and Charlie’s bits) then by using the upper tail inequality,the remainingnbits give bounds for error rate in theZbasis under the condition that

with probability 1−ε1. The other upper bound for error rates in the complementary baseseαβδwithα,β,δ ∈{X,Y}can be obtained analogously by applying Lemma 1.
5. Simulation results
In this section,we simulate performance of the proposed protocol on a fiber-based QKD system model. We use the following experimental parameters: the loss coefficient of the fiber is 0.2 dB/km, Bob and Charlie’s detection efficiencies,η= 14.5%, and dark count rate of single-photon detector,Pd=1.7×10−6. The security parameters of secrecy and correctness are fixed atεcor=10−15andεsec=10−10.We assume that error correction efficiency,fEC=1.22 and the expected photon number for signal states is set atµ=0.6. The optimal probability,pzfor key basis is set at 0.95 according to Ref.[49].
Figure 2 shows the secret key rate,ℓ/N, as a function of signal sizeNfor the two-party and three-party RFI protocols.The key rates are obtained at different values for the intrinsic error rate,Q=(0.02%,0.03%,0.05%) due to the misalignment and instability of the optical system. We observe that our proposed protocol can achieve a positive key rate with a minimum of 103signals. It can also be observed that higher key rates are achieved for the three-party protocol as compared to the two-party counterparts for the same number of signals exchanged. Our simulation result demonstrates that the threeparty RFI QKD is a feasible scheme in the finite-key regime.

Fig. 2. Plot of secret key fraction versus number of signals N for the proposed three-party RFI protocol (solid lines) for security parameters: εcor = 10−15, εsec = 10−10, and the misalignment error rates Q =(0.02%,0.03%,0.05%). For comparison, we also plot the two-party RFI protocol(dashed lines)for the same error rates.
In Fig. 3(a), we simulate the secret key rate for threeparty RFI protocol as a function of transmission distance for fixed misalignment degreeβ=0,π/6,π/8. For comparison,we also simulate the key rate for the two-party RFI protocol(dashed line)for the same parameters.We observe that despite the increase in misalignment of reference frames, the achievable transmission distance is still comparable to when there is no misalignment in reference frames(whenβ=0). Also,our results indicate that the two-party RFI protocol outperforms our proposed three-party RFI protocol in terms of maximum attainable transmission distance for different misalignment degrees ofβ. These results may be attributed to the fact that the three-party RFI protocol considers misalignment in two channels linking Alice to Bob and Charlie. On the contrary,the two-party RFI protocol employs one channel linking Alice and Bob hence a slight increase in signal gain and superiority in performance. Nevertheless, our proposed three-party RFI protocol is more efficient for secure communication involving multiple parties as a secret key for each party is produced from a single run of the protocol rather than performing multiple bipartite QKD protocols to establish a secret key for each communication party.
In Fig. 3(b) we demonstrate the performance of threeparty RFI protocol for a fixed number of signals,N=107,108and 109. For comparison, we provide the plots for the twoparty RFI protocol for the same number of signals. Our results demonstrate that with a minimum data size ofN=107, it is possible to achieve a secure key rate at a reasonable transmission distance of approximately 120 km for the three-party protocol. We also observe the slight superiority of two-party RFI protocol over three-party RFI protocol in terms of achievable secret key rate and transmission distance. Thus, this demonstrates that our proposed protocol fares well against the twoparty protocol,which proves its feasibility.

Fig.3. (a)Expected secret key rate(in logarithmic scale)for the proposed three-party RFI protocol (solid red line) as a function of transmission distance measured in km, for the fixed misalignment degree β. From left to right,the curves represent β =π/6,β =π/8 and β =0.The number of signals are fixed at 109. (b)Expected secret key rate(in logarithmic scale)for the proposed three party RFI protocol(solid red line)as a function of transmission distance measured in km,for the fixed number of signals,N=107,N =108 and N =109. The relative rotation of reference frames is set at β =π/8 and security parameters are εcor =10−15, εsec =10−10, experimental parameters: dark counts rate,Pd=1.7×10−6,the loss coefficient of the channel is 0.2 km/dB,the detection efficiency is η =14.5%. For comparison purposes we show the plots of two-party RFI protocol,represented by blue dashed lines in both figures.
In Fig.4,we plot the key rate against the quantum bit error rate in the asymptotic regime to deduce the lower bound on the tolerable error rate. We obtainEZZZ ≈0.2265 for the proposed protocol, which indicates that a secure key is achievable at higher error rates compared to the two-party RFI protocol[19]with an error bound of 12.62%and the wellknown error bound for BB84 protocol of 11.0%.[50]
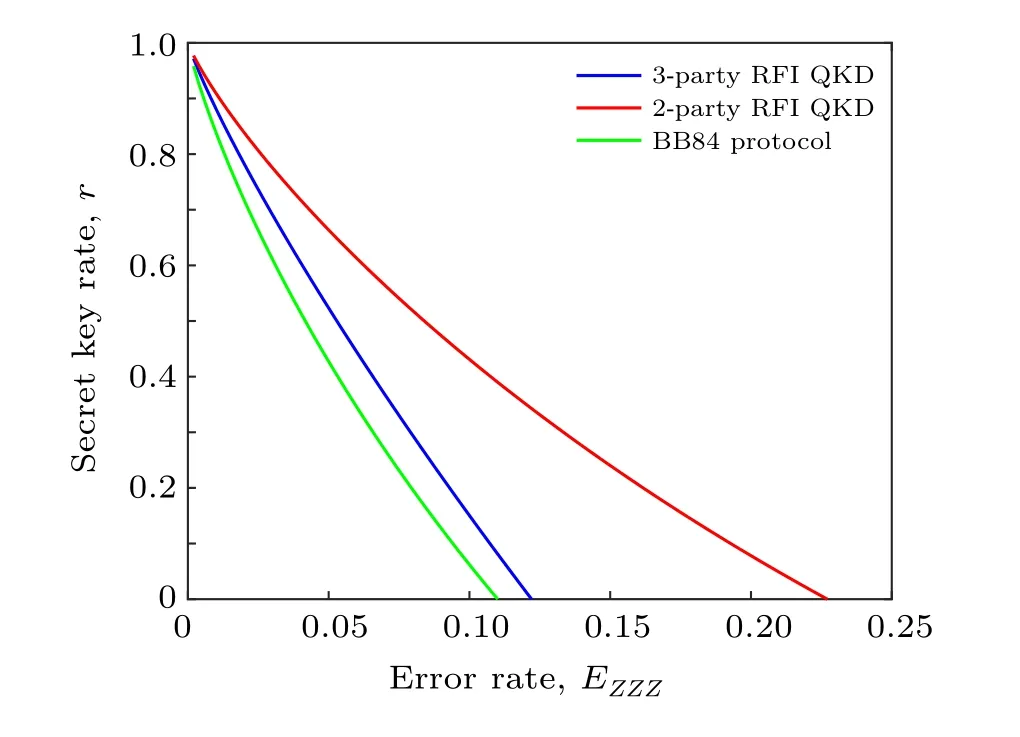
Fig.4. Plots of secret key rate vs quantum bit error rate,EZZZ for the BB84 protocol,[50] two-party rfiprotocol[19] and the proposed three-party rfiprotocol.
6. Conclusion
We presented a three-party RFI QKD protocol that can be implemented without any alignment between the sender and the receiver. The protocol exploits entangled states to establish a secret key between three communicating parties.We derived the asymptotic key rate for the proposed protocol against collective attacks and performed finite-size key security of the three-party RFI QKD protocol. Furthermore, we simulated the secret key rate for three-party RFI protocol as a function of transmission distance for different misalignment degrees (β=π/6,π/8) to investigate the impact on statistical quantityCand stability of the protocol. The simulation results demonstrate that our proposed protocol is not heavily affected by an increase in misalignment of reference frames as the achievable transmission distances are still comparable to the case where there is no misalignment in reference frames(whenβ=0).
Furthermore,we investigated the performance of our proposed three-party RFI protocol for a fixed number of signals. The simulation results demonstrate that the protocol can achieve a significant secret key rate at reasonable transmission distances of about 120 km with 107signals. However, a further distance of 195 km can be achieved with about 109finite signals. The proposed protocol presents a suitable alternative for practical QKD implementations. This was demonstrated by reasonable secret key rates obtained with rigorous and tight statistical fluctuation analysis methods for finite-size key effects. Furthermore, our protocol is more efficient than the two-party RFI protocol in terms of resource consumption, as few data signals are required to produce reasonable secret key rates, as evidenced by the finite key analysis results. Moreover, we have also shown that our protocol is robust against noise in the quantum channel based on the realized error rate threshold of 22.7%, which is an improvement to the existing two-party BB84 protocols.
Appendix A:Secrecy
We provide details for the derivation of key length and security bounds presented in this work. We use the entropic uncertainty relations to establish bounds on the smooth-min entropy of the raw key conditioned on Eve’s information. Let system ´Ebe information that Eve gains onZA,ZBandZC,i.e.,the raw key for Alice,Bob,and Charlie up to the error correction step. If Alice, Bob, and Charlie apply a privacy amplification scheme based on two universal hashing[51]to extract shorter key strings of lengthℓfromZmeasurement statistics,the protocol is ∆-secret if

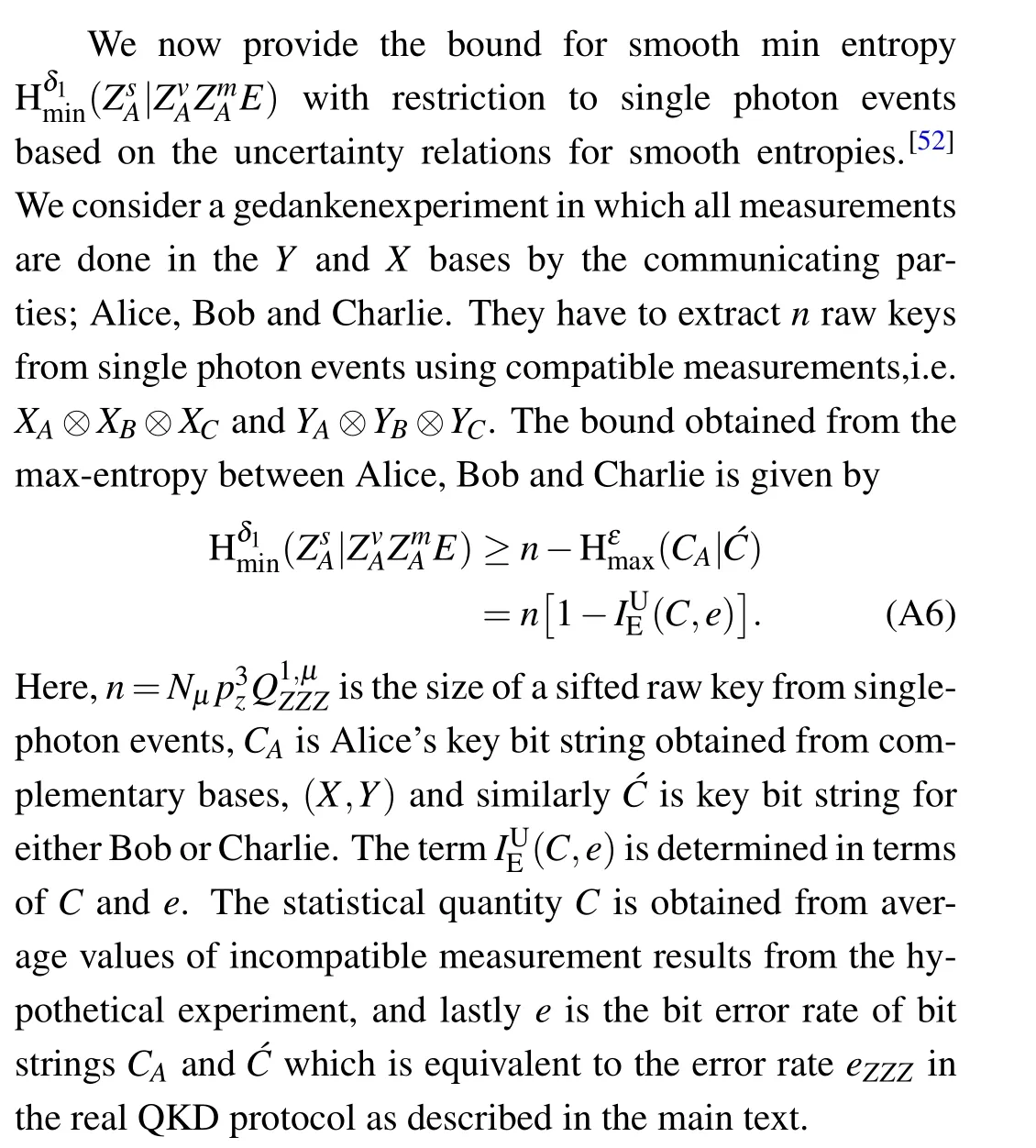
Finally,we compose the error terms due to finite sample sizes and estimation of observed values from expected values as described in the main text. From the main text, we found out that there is error probability,ε1due to estimation of observed error rate,eZZZby using Lemma 1 of Ref. [38]. The observed error rates in the complementary baseseαβδwithα,β,δ ∈{X,Y}are obtained analogously applying Lemma 1 with failure probability,ε1. The error rates from the incompatible measurements in the complementary bases are eight all together which brings the sum of error probabilities to 8ε1.We also estimated the observed number of detected single photon components using lemma 2 of Ref.[38]with failure probability,ε2. Lemma 3 was used to estimate the expected values,nµ,nνandnωwith failure probability,ε3for each. Therefore combining all the error terms for min-entropies and estimation of observed values,the secrecy is given by

- Chinese Physics B的其它文章
- Transient transition behaviors of fractional-order simplest chaotic circuit with bi-stable locally-active memristor and its ARM-based implementation
- Modeling and dynamics of double Hindmarsh–Rose neuron with memristor-based magnetic coupling and time delay∗
- Cascade discrete memristive maps for enhancing chaos∗
- A review on the design of ternary logic circuits∗
- Extended phase diagram of La1−xCaxMnO3 by interfacial engineering∗
- A double quantum dot defined by top gates in a single crystalline InSb nanosheet∗