A chaotic hierarchical encryption/watermark embedding scheme for multi-medical images based on row–column confusion and closed-loop bi-directional diffusion
Zheyi Zhang(张哲祎), Jun Mou(牟俊),†, Santo Banerjee, and Yinghong Cao(曹颖鸿),‡
1School of Information Science and Engineering,Dalian Polytechnic University,Dalian 116034,China
2Department of Mathematical Sciences,Politecnico di Torino,Torino 10129,Italy
Keywords: chaotic hierarchical encryption, multi-medical image encryption, differentiated visual effects,row–column confusion, closed-loop bi-directional diffusion, transform domain watermark embedding
1.Introduction
Along with the advancement of technologies such as healthcare private cloud and internet of medical things(IoMT),diagnosing and treating patients through telemedicine has become a new trend in the healthcare field.[1–3]Telemedicine will inevitably arise in the communication of medical images, and in the process of communication will inevitably arise in the leakage and exposure of image information,the attacker in the process of communication to intercept the image information will affect the smooth completion of medical treatment and diagnosis, and even more so, may also be to the patient’s private information and personal safety caused by the incalculable loss.[4–6]This makes the security of medical images crucial in the communication process,and encrypting medical images before communication can be a good solution to this problem.[7–9]
Researchers have proposed many image encryption schemes for the security of medical image communication.For example, chaotic sequences are generated by chaotic systems to provide pseudo-randomness for the encryption scheme, confusion and diffusion are realized by traditional Fridrich structures;[10–13]the content in medical images is discriminated to partially encrypt the visually effective part;[14]partial encryption of the part of interest is realized by combining with deep-learning encryption and decryption networks;[2]and a new content-aware DNA computing algorithm is designed to encrypt medical images and other algorithms.[15]All these schemes can protect the communication security of medical images,but in the realization of application scenarios,all users get the same visual level of decrypted images.The currently proposed schemes do not differentiate the decryption process for users with diverse security levels, which makes these users get the decrypted images with same visual levels.As for medical image encryption and decryption, the decryption results with visual differences can enrich the application scenarios of the proposed scheme.For example,visually damaged medical images are usually uploaded and displayed on the internet to provide a convenient preview for patients and related personnel; visually undamaged decryption results can be used in the real medical diagnosis process,where clear,undamaged medical images will not affect the doctor’s diagnosis results; and when there is a dispute about the attribution of a medical image, watermarking information can be extracted from medical images to prove the attribution of the images.In order to solve this problem,a hierarchical encryption scheme for medical images has emerged.
First of all, chaotic keys are used to generate chaotic sequences to provide pseudo-randomness for the encryption scheme.[16–19]Most of the previously proposed encryption schemes utilize the generated chaotic sequences to realize the confusion and diffusion operations on the plaintext images, and after obtaining the cipher images, the user can get the decrypted images under the condition of the given chaotic key.[20–24]Chaotic systems are extremely keysensitive,i.e.,two sets of chaotic keys with a slight difference produce chaotic sequences that are radically different from each other.[25–31]The proposed scheme takes advantage of this and produces hierarchical chaotic keys,so that users with different security levels can obtain different chaotic keys to decrypt images with different visibility levels, and at the same time improves the problem of decrypting images with a single visibility level in the previously proposed encryption schemes.
Secondly,this scheme adds the embedding and extraction of watermark images on the basis of hierarchical chaotic encryption,and this part can be regarded as the highest security level in the hierarchical encryption scheme.Existing watermark embedding techniques are mainly categorized into two types: spatial domain watermark and transform domain watermark, and the most common embedding method for spatial domain watermark is the least significant bit (LSB), but the robustness of this method is poor.[32,33]This scheme uses the joint spatial domain watermarking embedding algorithm of discrete wavelet transform (DWT) and singular value decomposition (SVD), which has the advantages of strong robustness of transform domain watermark,high image fidelity,etc.,[34,35]and can be applied in this scheme to realize further protection of the patient’s private information and the copyright information of the images.
Finally,this scheme uses a multi-image encryption(MIE)scheme to encrypt and decrypt medical images in batches.Compared to single-image encryption algorithms, MIE algorithms greatly reduce the time cost of encrypting and decrypting images, while increasing the difficulty for attackers to crack the algorithm.[36,37]The method of fusing multiple images into a multi-image cube in this scheme has better compatibility with the size of the images as compared to the method of fusing multiple images into one large image.[38–40]Meanwhile,this scheme improves the existing encryption algorithm and designs the encryption algorithm with row–column confusion and bi-directional closed-loop diffusion,and the designed encryption algorithm is highly correlated with the chaotic sequence, which ensures the security of image communication.Meanwhile, this paper also confirms the feasibility and security of the proposed scheme through simulation experiments.
In summary,the contributions or advantages of this work are as follows.
(i) A hierarchical encryption and decryption scheme is proposed, where users with different security levels can obtain decrypted images with different visual effects by using different keys.
(ii) Watermark embedding is implemented using DWT and SVD to extend the highest security level of layered encryption schemes while serving to avoid disputes over medical image attribution.
(iii)A novel MIE algorithm with row–column confusion and bi-directional closed-loop diffusion is designed.
2.Preliminaries
2.1.A discrete chaotic map
A discrete chaotic map is used in the proposed scheme,and the expression of this chaotic map is
whereaandbare the parameters in the equation.
This discrete map has a large dynamical range and the phase diagrams of this chaotic map are shown in Fig.1 when the parameters are (a,b,x0,y0) = (0.8,1.8,0.1,0.1),(1,1.4,0.1,0.1), (1.3,1,0.1,0.1), and (1.9,0.6,0.1,0.1), respectively.
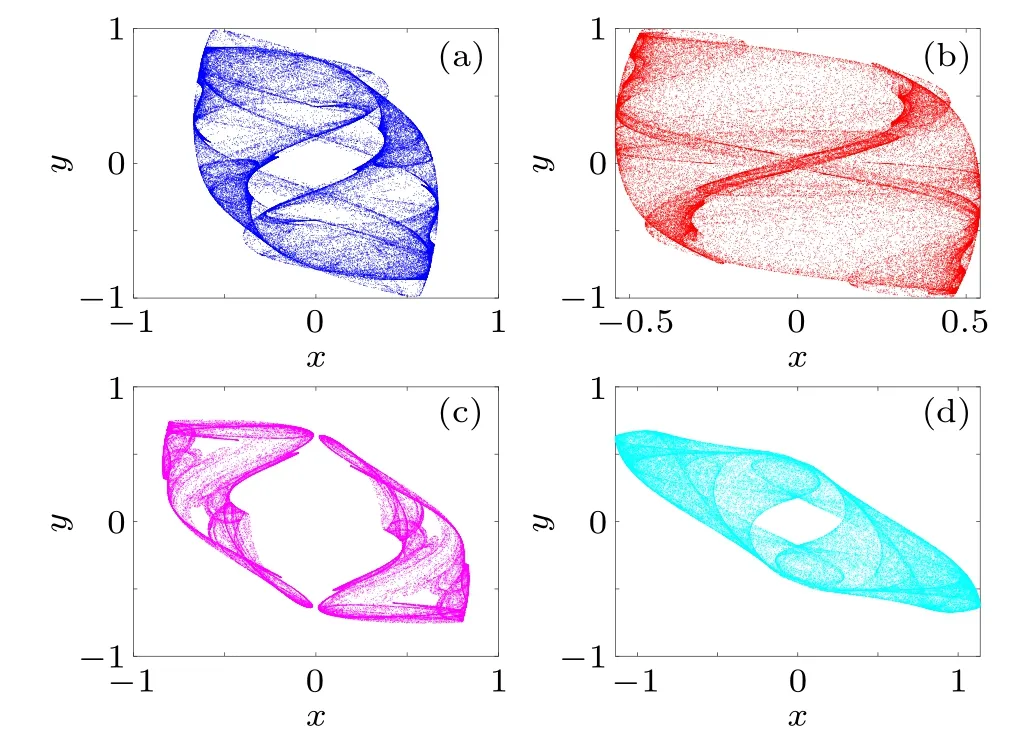
Fig.1.Phase diagrams under different sets of parameters:(a,b,x0,y0)=(0.8,1.8,0.1,0.1)(a),(a,b,x0,y0)=(1,1.4,0.1,0.1)(b),(a,b,x0,y0)=(1.3,1,0.1,0.1)(c),(a,b,x0,y0)=(1.9,0.6,0.1,0.1)(d).
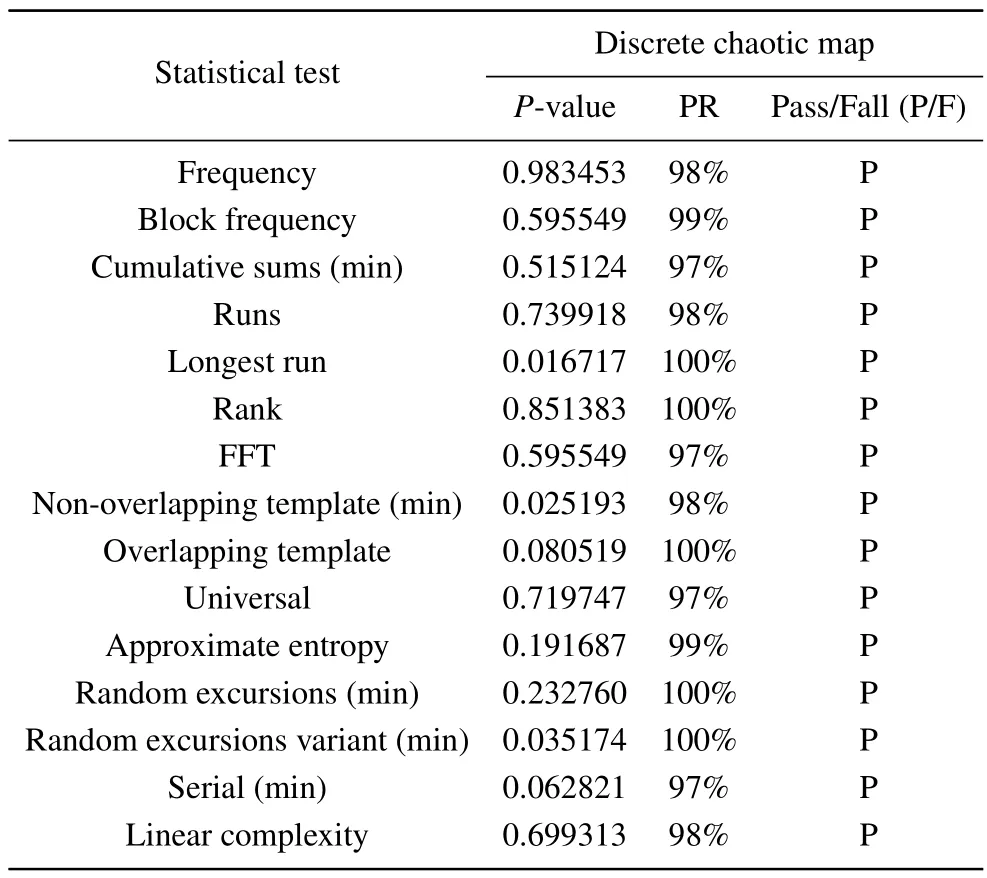
Table 1.NIST test results.
From the above figure, it can be seen that the phase diagram of the chaotic map changes considerably when the parameters are varied.A large range of parameters can provide sufficient pseudo-randomness for the encryption scheme.In order to further verify its pseudo-randomness,under the condition that the parameter is set to (a,b,x0,y0)=(0.8,1.8,0.1,0.1),iteratively chaotic map 1.25×107,two sets of chaotic sequences are obtained,and the two sets of chaotic sequences are converted to binary, and the binary strings will subject to NIST test(NIST SP 800-22),and the results of the test are shown in Table 1.The tests are all passed,further proving that the chaotic map can bring extremely strong pseudorandomness to the encryption and decryption scheme.
2.2.Watermark embedding based DWT and SVD
DWT is a signal change in the transform domain,the discrete signal will be divided into one low frequency componentLL,three high frequency componentsLH,HLandHHin different directions after DWT processing as shown in Eq.(2).SVD is usually used to extract the image eigenvalues as shown in Eq.(3),the image is decomposed into the left singular matrix(U),singular value matrix(S),right singular matrix(V)after SVD
2.3.Hierarchical encryption technology
In this paper,a concept of hierarchical encryption is proposed.Briefly, encryption is performed by setting up a hierarchical chaotic key to satisfy the demand of decryption under realizing different visibility.For a general encryption and decryption scheme, researchers generally select a chaotic sequence generated by a chaotic system iteratively under a certain set of parameters to provide pseudo-randomness for the encryption and decryption scheme.This set of parameters is regarded as the chaotic key of this encryption scheme.
This scheme improves this process by generating three sets of chaotic sequences under three sets of chaotic keys respectively, and combining the three sets of chaotic sequences as shown in Fig.2.In the paper, three application scenarios are preset,which are full level,transparent level and required level.In the face of different needs to give a different number of keys, the user with the highest priority has three different keys,the fusion of the chaotic sequence can be lossless decryption of the image, this process is regarded as full-decryption,similarly,when the user with a lower priority has only one set of keys, the resulting chaotic sequence decrypted image has obvious noise,this process is regarded as required-decryption.

Fig.2.Hierarchical chaotic keys and chaotic sequences generation process.
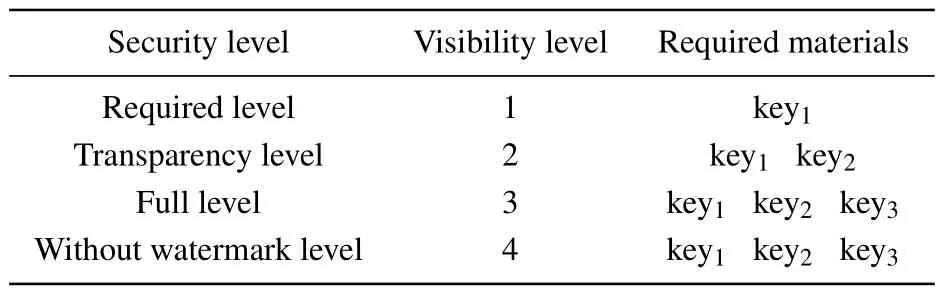
Table 2.Decryption process security level table.
The variables that control the length of each segment of the key in the hierarchical key are known as the security coefficients(SC)S1andS2,
They represent both the visibility and clarity of the partial visibility levels, and the user can change the visibility level of each level by changing the SC.
Finally, this paper also uses watermarking technique to provide the last layer of security to the user.So far,all the security levels of this scheme are categorized into four levels as shown in Table 2.
3.Proposed scheme
The specific flow of the proposed encryption and decryption scheme is shown in Fig.3, and the three main parts involved are categorized into watermark embedding and extraction,hierarchical key generation,multi-image encryption and hierarchical multi-image decryption.
3.1.Watermark image embedding
Considering that the cover images used in the designed scheme are medical images of varying sizes, to better fit the sizes of the cover images, the size of the watermark image needs to be adjusted before the watermark is embedded.Assuming that the sizes of the cover images arehandw, the length (hh) and width (ww) of the watermark image are adjusted to half of the cover images as
where ceil(·)denotes upward rounding.
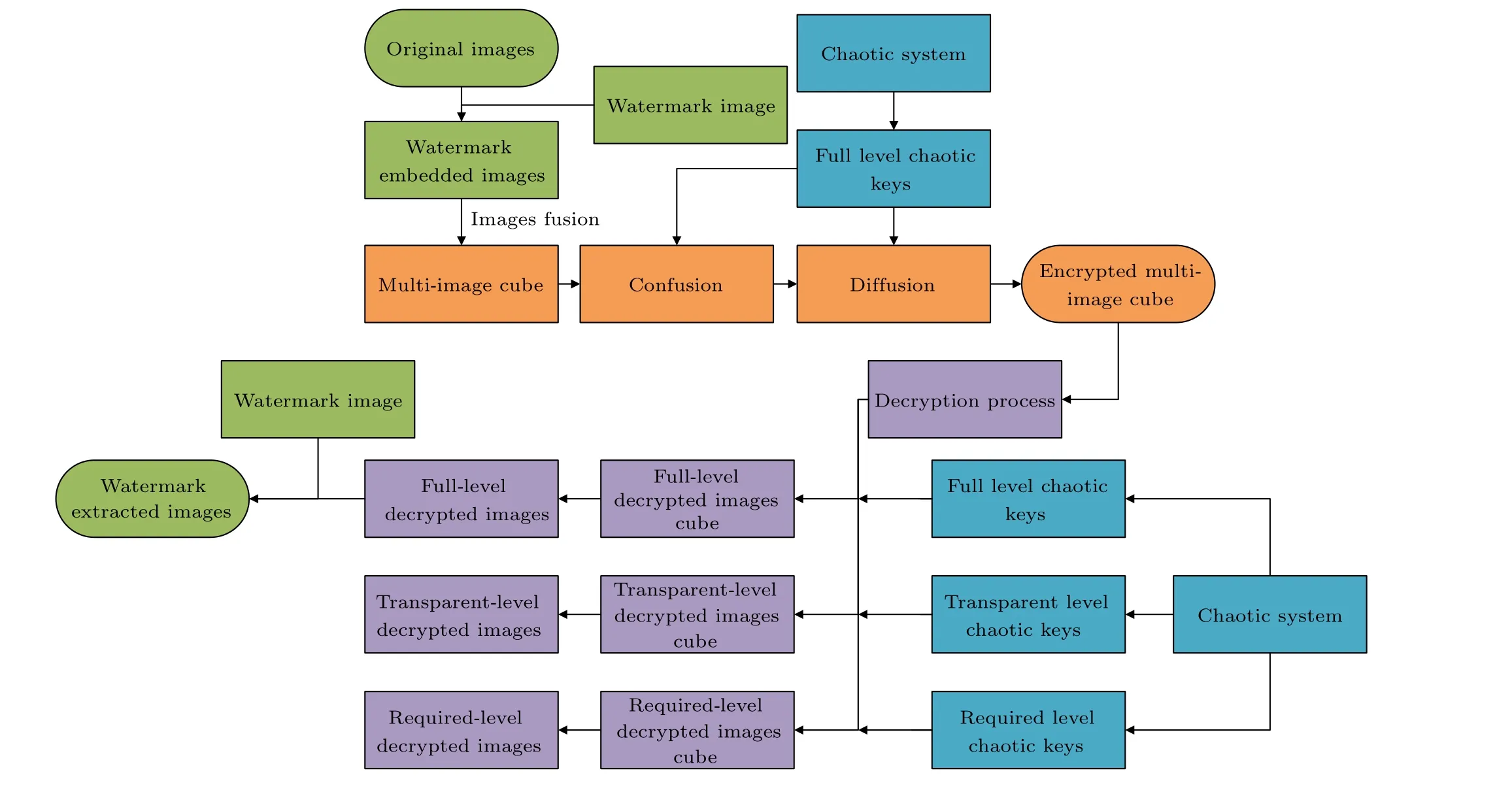
Fig.3.Encryption and decryption scheme flow chart.
In this scheme,the watermarked image is first embedded into the image to be encrypted using DWT and SVD as shown in Eq.(6).This scheme embeds the watermark into theLLof the original images so that the watermark has better robustness but poor invisibility,theαis a parameter representing the amount of embedding,which is taken as 0.2 in this scheme to get the watermark embedded images.
where IDWT stands for discrete wavelet inversion transform and I, W and IW stand for original image, watermarked image,and embedded image respectively.
3.2.Encryption process
A multi-image encryption algorithm with row and column confusion and bi-directional closed-loop diffusion is designed in the paper, and the following are the specific operations of the encryption scheme.
Step 1.Multiple watermarked images are fused into an image cubeBand the sizes of each image are recorded separately,the sizes ofBare noted asH,W,andL.
Step 2.InputtingBinto the function hash-256 yields two variableshaandhbrelated toB.
Step 3.Pre-selecting three different sets of initial values and coefficients of the chaotic system, combined withhaandhb,three different sets of chaotic sequences are obtained,which are named asX1,Y1,X2,Y2,X3,Y3.
Step 4.Three sets of chaotic sequences are generated by setting two SCs,S1andS2,according to Fig.2.The three security levels correspond to three sets of chaotic sequences,full level corresponds toXandY, transparent level tox1andy1,and required level tox2andy2.
Step 5.(confusion process)In the encryption process,the chaotic sequencesXandYgenerated using the key with the highest visibility level are used.
Step 5.1.(generate subsequences)SplitXandYinto ten subsequences as shown in Eq.(7).Wheresq1,sq3,sq4,sq5,sq6are used for row confusion andsq2,sq7,sq8,sq9,sq10are used for column confusion
Step 5.2.The two subsequencessq1,sq2are preprocessed as shown in
where floor(·)means round down.
Step 5.3.(row confusion and column confusion)Positive order traversal is performed on each row of the image cubeB,row confusion is performed according to Eq.(10),and after the end of row confusion,positive order traversal is performed on each column ofB, column confusion is performed according to Eq.(11), and the cube obtained after the final disorganization is namedC
Step 6.(bi-directional closed-loop diffusion) Each element in the cubeCis integerized into a column vectorV.After traversing each pixel point ofV,the specific diffusion operation is shown in Eq.(12).The diffusedVis rectified into a cube of the same size asC,and the new cube is namedD
3.3.Hierarchical decryption process
In this scheme,the decryption process is the reverse process of the encryption process.But the visible level of the decrypted image obtained by users having different chaotic keys is different, and the watermark image can be extracted when the user has the original cover image.The decryption flowchart is given in Fig.3.
Step 1.Multiple sets of chaotic keys are input to the chaotic map,and multiple chaotic sequences with different decryption levels are obtained by iterating the chaotic map.
Step 2.The cipher cubeDis rectified into column vectors,combined with chaotic sequences for inverse bi-directional closed-loop diffusion,and the diffused column vectors are reshaped into a cubeC.
Step 3.Traverse the cubeCin reverse, first perform inverse column disarrangement onC, and then perform inverse row disarrangement onC.The resulting image cube is namedB.
Step 4.TheBis split according to the sizes of each image recorded during the encryption process.It is worth noting that the image at this point is still a watermarked image, and both lossless images and watermark images can be obtained by watermark extraction.
4.Encryption and decryption effects
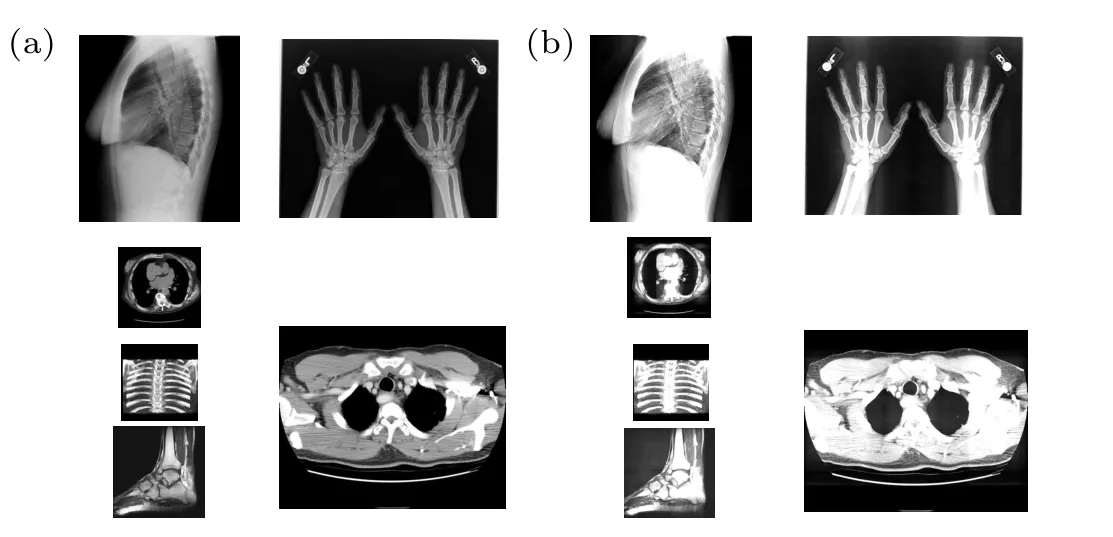
Fig.4.Watermark embedding effects(a)original images,(b)images after watermark embedding.

Fig.5.Multi-medical image encryption effects(a)original images after watermark embedding,(b)encrypted images,(c)cipher image cube.
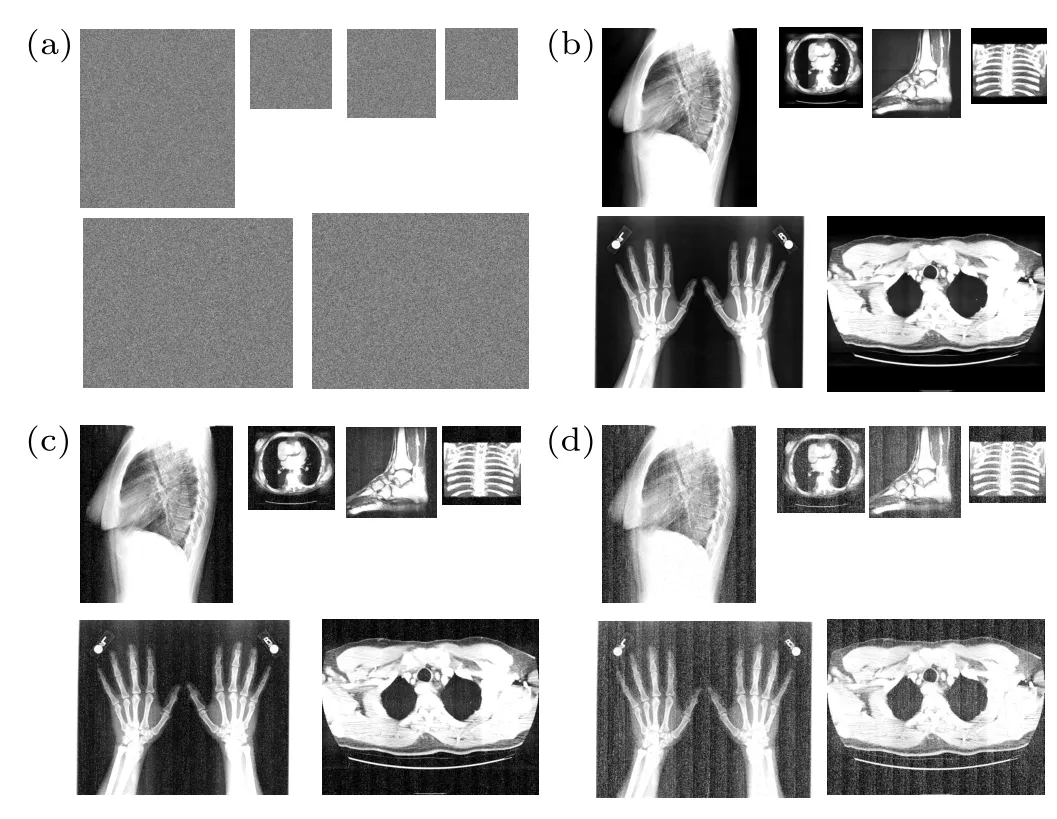
Fig.6.Hierarchical decryption effects (a) cipher images, (b) full-level decryption images,(c)transparent-level decryption images,(d)requiredlevel decryption images.
Simulation tests are conducted for this program.Six medical images with different sizes are used for testing, they are Fig.1 (1024×880), Fig.2 (454×468), Fig.3 (400×400),Fig.4 (500×500), Fig.5 (826×1018), Fig.6 (828×1024).The watermark image is boat.png, and its size will vary according to the sizes of the cover images,as shown in Eq.(5).TheS1andS2are set to 5 and 20 for this simulation test and the simulation results are given in Figs.4–6.
Simulation and test environment: software: Matlab 2022a; OS: Window10; CPU: 12th Gen Intel(R) Core(TM)i5-12400F 2.50 GHz;RAM:8 GB.
5.Performance analysis
5.1.Watermark images extraction reconstruction quality
For this proposed scheme, the images are encrypted and decrypted after the watermark embedding, which leads to a slight discrepancy between the watermark extraction reconstructed result compared to the original watermark images.To test the effect of encryption and decryption on the quality of watermark extraction and reconstruction in this scheme, the metric of PSNR is used to measure the gap between the two,the resultant images of watermark reconstruction are given in Fig.7,and the result of PSNR calculation is given in Table 3.The comparison of the watermark reconstruction quality of this scheme with other schemes is given in Table 4,from which it can be seen that the algorithm has better superiority in watermark image reconstruction quality.

Table 3.Watermark images reconstruction quality.
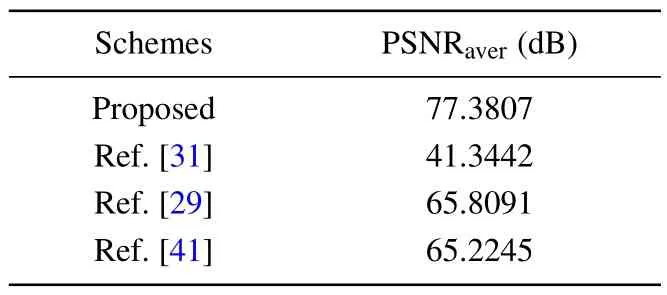
Table 4.Comparison of watermark reconstruction quality with other schemes.
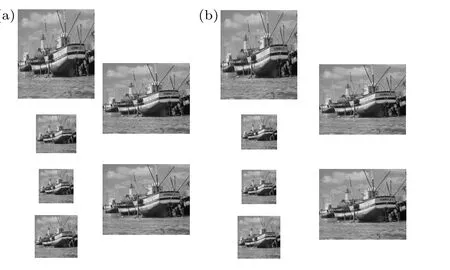
Fig.7.Watermark reconstruction effects(a)original watermark images,(b)reconstructed watermark images.
5.2.Key space and its sensitivity
The pseudo-randomness required in the encryption and decryption process in this scheme is all provided by the chaotic sequence, and the chaotic key determines the generation of the chaotic sequence.Therefore, for the security of the encryption/decryption scheme,the key space and key sensitivity directly determine the cracking difficulty of the attacker.
(i) Chaotic key space: in this scheme, the chaotic key is contributed by two parts.There are four chaotic system parametersa,b,x0,y0,their key space is 1015,1016,1016,1016.The second one is the parameter related to the plaintext,ha,hbwhose key space is 1016,1017respectively.To summarize the total key space is 10(15+16×4+17)=1096≈2318,it is much larger than 2100,which shows that it is difficult for the attacker to attack the algorithm by brute-force cracking.[42]From Table 5, it can be seen that the key space of this scheme has an upper hand compared to other schemes.
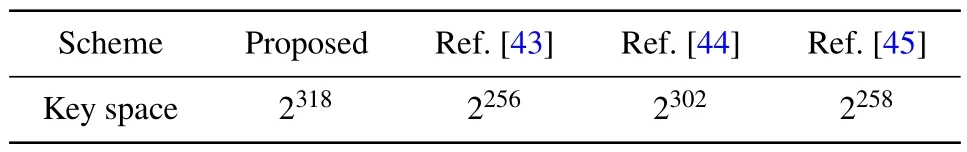
Table 5.Key space comparison with other schemes.
(ii) Key sensitivity: this scheme is considered to have strong key sensitivity if there is a huge gap between the encrypted image and the original encrypted image at this time when there is a tiny deviation of the input chaotic key.Taking the encryption result of Fig.1 as an example, let the first encrypted cipher bec1and the second encrypted cipher bec2,then the histogram of|c1-c2| with different key deviations is given in Fig.8, and it can be observed very intuitively that there are only a very small number of points where the difference between the points is 0,i.e.,there is a huge gap between the two encrypted images.This means that the chaotic key used in this scheme has a strong key sensitivity to the encryption process,and a small perturbation of the key can make the encrypted image change dramatically, which also means that it is difficult for an attacker to obtain the correct key by bruteforce cracking.
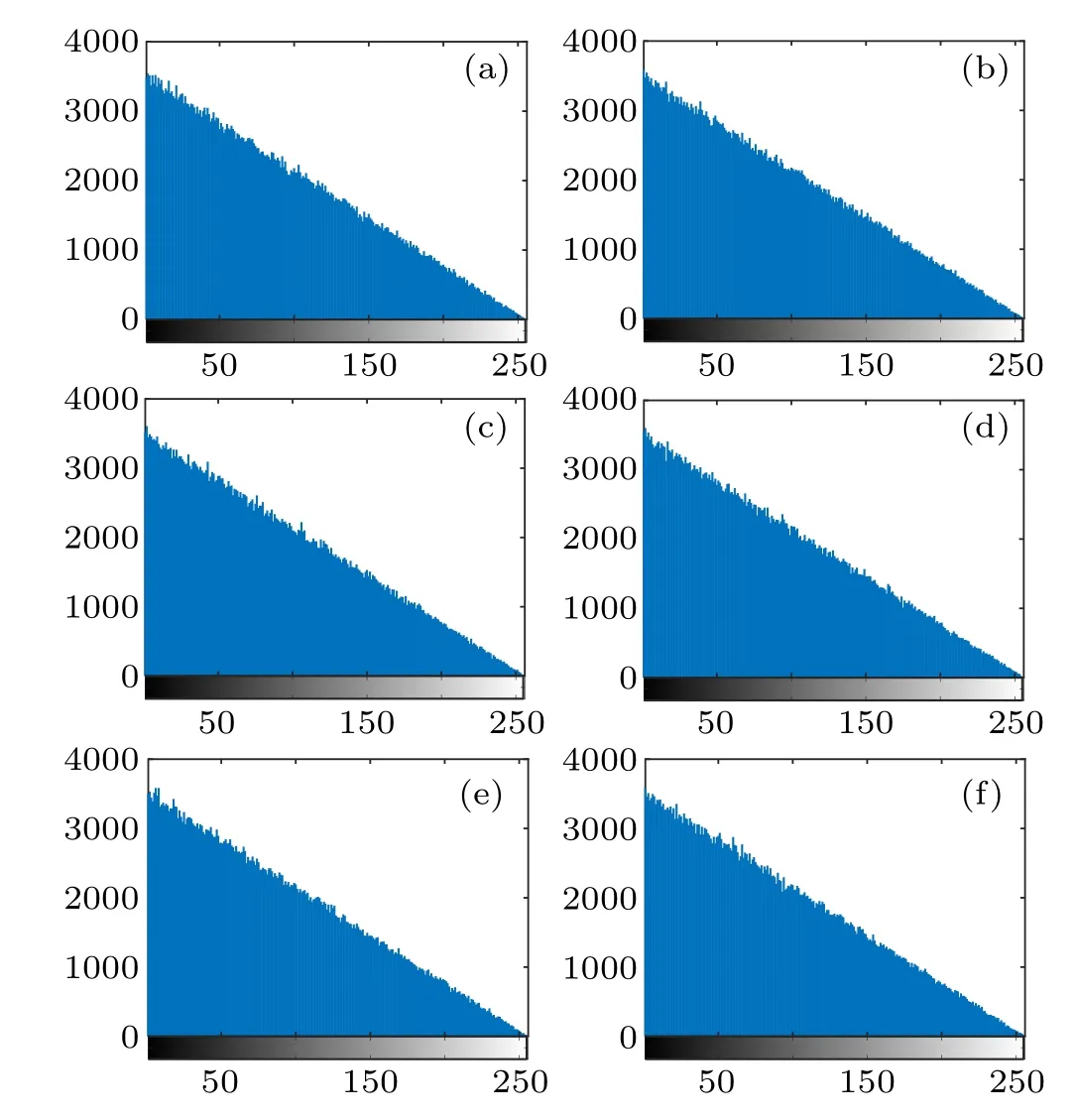
Fig.8.The histogram of|c1-c2|(a)a=a+10-15,(b)b=b+10-16,(c) x0 =x0+10-16, (d) y0 =y0+10-16, (e) ha =ha+10-16, (f) hb =hb+10-17.

Fig.9.Histogram test effects(a)–(f)encryption effects of Figs.1–6.
5.3.Statistical attack resistance
5.3.1.Histogram test
The histogram can show the distribution pattern of pixel values of each pixel in an image, generally the histogram of plaintext image is distributed in a certain regular way,and the encryption scheme needs to destroy this distribution pattern.The histogram test effect of this encryption algorithm is shown in Fig.9, which can be visualized that this encryption algorithm can make the distribution of pixel values in the image becomes uniform.
5.3.2.Correlation between neighboring pixel points
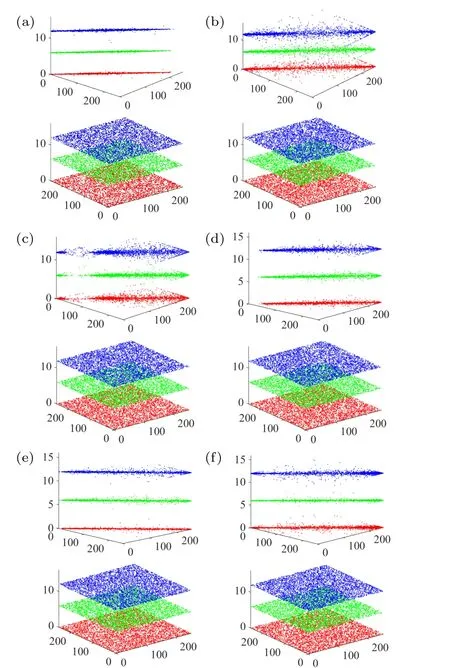
Fig.10.Correlation graph of original and encryption images (a) Fig.1,(b)Fig.2,(c)Fig.3,(d)Fig.4,(e)Fig.5,and(f)Fig.6.
The purpose of designing the encryption algorithm is to change this strong correlation so that the attacker cannot attack the encryption algorithm by analyzing the correlation.The correlation graph between neighboring pixels before and after encryption of this scheme is given in Fig.10, where the red, green, and blue planes represent the correlation in the horizontal,vertical,and diagonal 45◦directions,respectively.It can be observed that for the unencrypted original image,the distribution of the correlation map in the three directions is a straight line, which represents the strong correlation between neighboring pixels in the three directions, while the correlation map of the encrypted image is randomly distributed in the whole plane in the three directions,i.e.,the correlation between neighboring pixels has been hidden, which proves that the proposed encryption scheme can hide the correlation between neighboring pixels in the original image very well.
5.3.3.Information entropy test
Information entropy directly represents how much visual information is shown in an image,the higher the visual clutter the higher the value of information entropy of the image.Theoretically speaking, the theoretical value of information entropy of an image is 8.[46]The information entropy test results of this scheme are given in Table 6, and it can be concluded from the results that the scheme is able to hide the visualization information of the original image well.
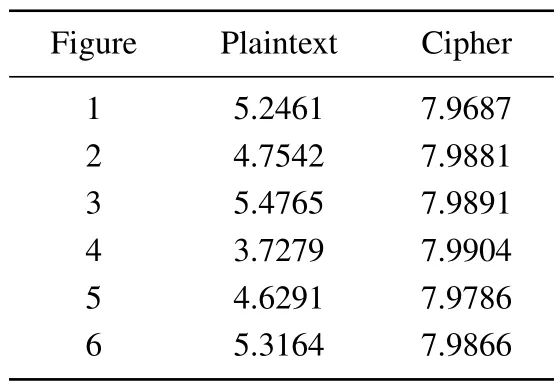
Table 6.Information entropy test results.

Table 7.NPCR and UACI test results.

Table 8.Comparison of performance against differential attacks with other algorithms.
5.4.Differential attack test
Differential attack is a common attack on encryption algorithms by comparing the gap between the encryption results of two plaintext images with a slight difference.In order to make it impossible for an attacker to attack the algorithm by the above methods,a good encryption algorithm needs to have some resistance to differential attacks.Two indexes, NPCR and UACI, are usually used to measure the gap between two images, and this algorithm is considered to have a certain resistance to differential attacks when the NPCR value is higher than the standard value(99.6094%)and the UACI is close to the standard value(33.4635%).[47]The test results of the differential attack of this algorithm are shown in Table 7, and from the comparisons with other algorithms in Table 8, it is able to conclude that this algorithm has a certain superiority over other algorithms in terms of resistance to differential attack.
5.5.Robustness testing
5.5.1.Shearing attack test
Image information may be attacked by malicious shearing during transmission in the channel.A good encryption algorithm requires that the decrypted image can still distinguish the original image information under malicious shearing.The simulation results under different shear ratios are given in Fig.11 below, it can be observed that the decrypted image can still distinguish the content of the decrypted image at a cutting rate(CR)of 25%.In this way, it is demonstrated that the proposed scheme has some robustness against shear attacks.
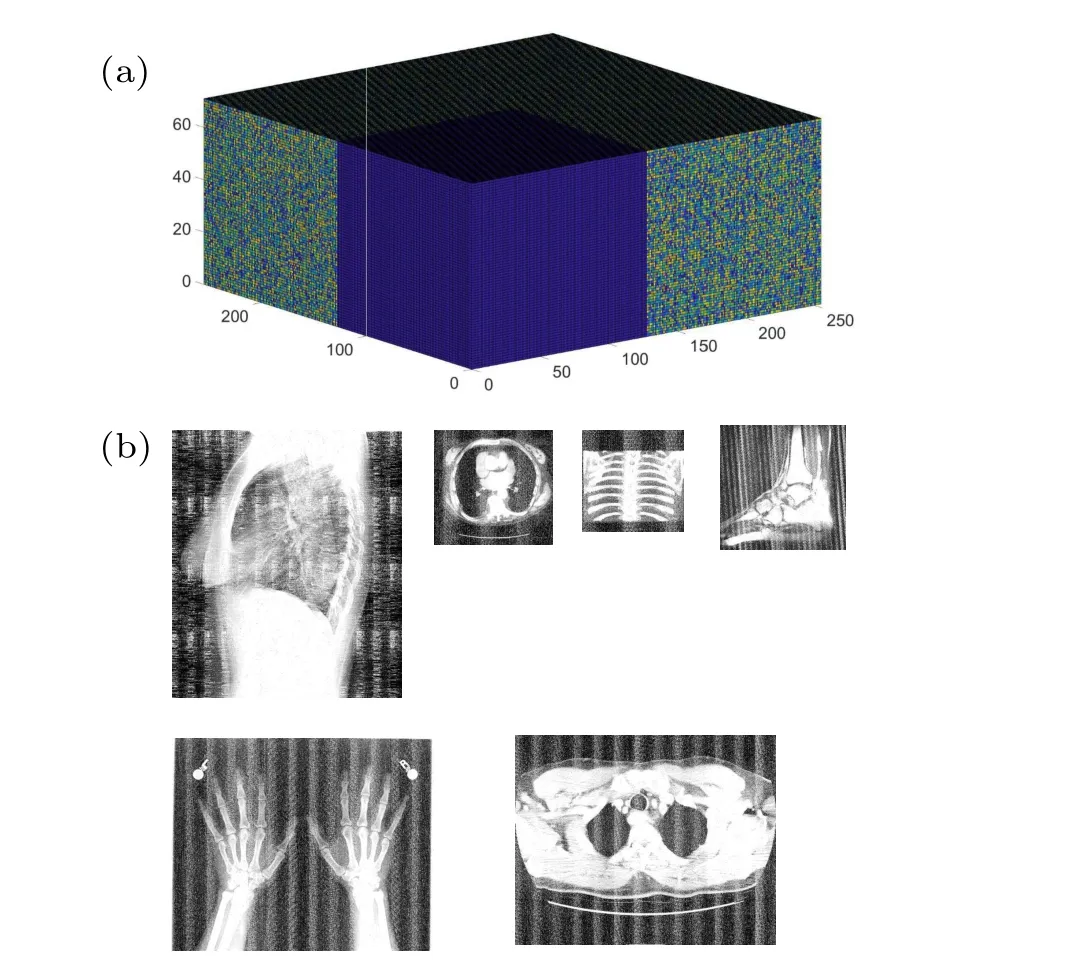
Fig.11.Decryption effect when CR is 25%(a)image cube cut effect,(b)decryption effect.
5.5.2.Noise attack test
Noise interference is a common problem in a kind of signal transmission over a channel, and for a good encryption algorithm,it needs to be robust to noise attacks.This scheme simulates the encryption and decryption process under different strengths of salt and pepper noise (SPN) conditions, and the decryption effect at SPN=0.1 is shown in Fig.12.It can be concluded that even if the decryption is carried out under the noise condition with particularly strong intensity, the decryption result can still distinguish the subject content of the decrypted image.It is proved that the proposed encryption and decryption scheme has some robustness against noise attacks.
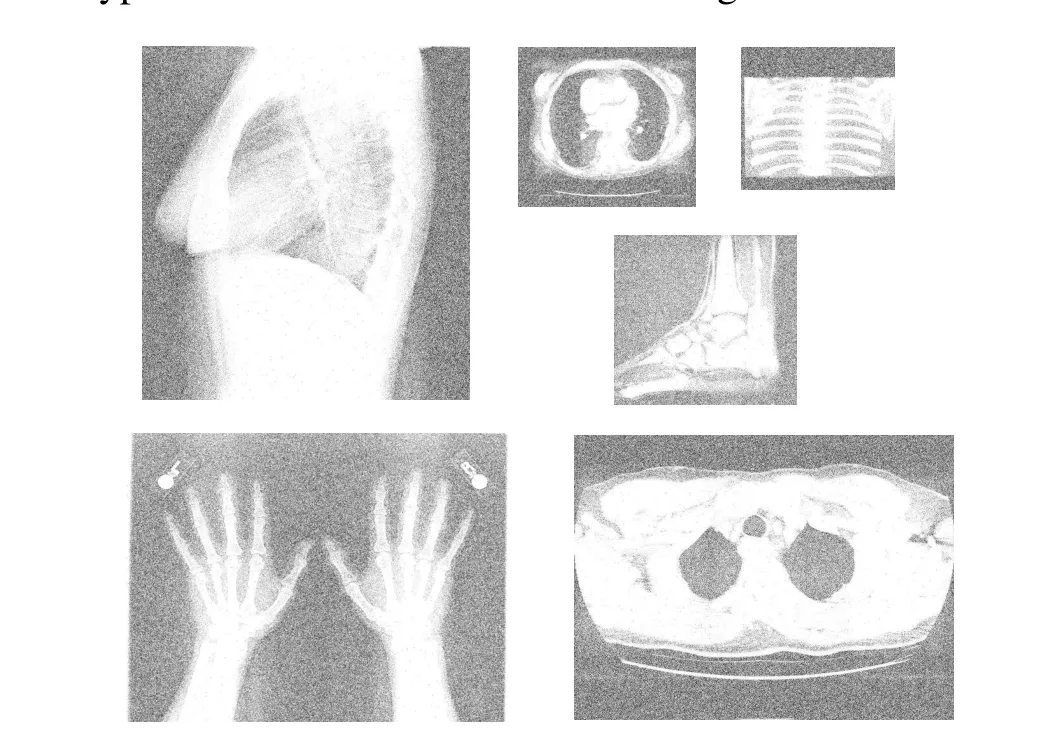
Fig.12.Decryption effect under SPN=0.1 condition.
5.6.Encryption and decryption efficiency
For an MIE algorithm, encryption and decryption efficiency is its most obvious advantage over single-image encryption algorithms.The batch of encrypted and decrypted images brings higher encryption and decryption efficiency.The encryption and decryption efficiency of this scheme is shown in Table 9,in order to facilitate the comparison of encryption and decryption efficiency with other schemes,this simulation uses 256×256 pixels as a unit, and expresses the encryption and decryption efficiency in terms of units/s as a representative.The efficiency comparison with other schemes is given in Table 10,and from the results,it can be summarized that this scheme has a greater advantage in encryption and decryption efficiency.
The main reason that the disarray process takes up most of the time in this scheme is that we counted the time taken by the chaotic system to iteratively generate the chaotic sequences in our tests,while the time required for row and column disarray is only a small fraction of the time.

Table 9.Algorithmic encryption and decryption efficiency.
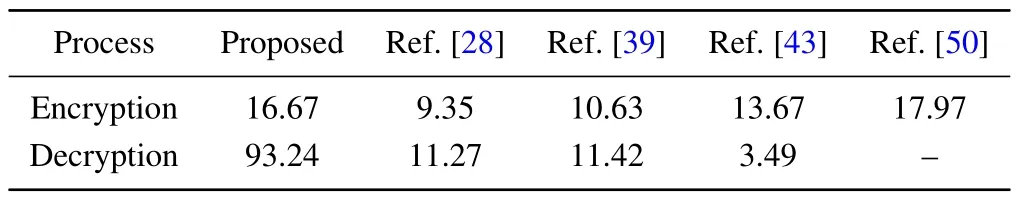
Table 10.Comparison of encryption and decryption efficiency with other MIE schemes.
5.7.Computational complexity
Computational complexity(CC)is a measure of the computer resources that needs to be mobilized to run the proposed algorithm once it is written as an executable program.Algorithms with lower CC are more likely to run on more terminals,e.g.,implementation on embedded hardware with lower computing power requires higher CC of the algorithm.Not only does the algorithm need to be able to accomplish the goals it needs to achieve,but it also needs to have the CC to run on the hardware platform.In order to add more possibilities for this system to be used in more scenarios, the CC of some important steps in this scheme are counted as shown in Table 11 for more directions.H,W,andLrepresent the length,width and height of the image cube respectively.
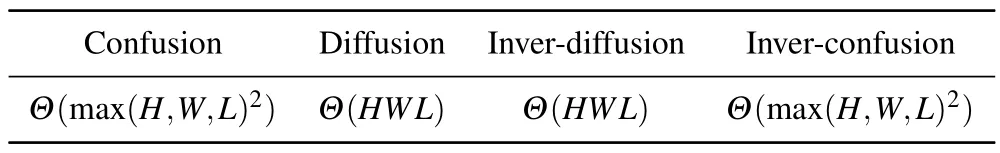
Table 11.Computational complexity statistics.
6.Conclusion
A chaotic hierarchical encryption/watermarking embedding scheme for medical multi-image based on row–colunm confusion and closed-loop bi-directional diffusion is proposed.Firstly,the chaotic system used is briefly introduced,and multiple sets of hierarchical chaotic keys are input into the chaotic map to get multiple sets of different chaotic sequences.Secondly, the watermarked image is embedded in the image to be encrypted,and the processed image is input and fused into a multi-image cube, notably, the size of the images constituting the cube can be arbitrary.Multi-image encryption is realized using the proposed row–column confusion and closedloop bi-directional diffusion algorithms to ensure the security of medical images in the communication process.Simulation and performance test results illustrate the feasibility, security and efficiency of the proposed scheme.Specifically, the key space of the algorithm is 2318,which is sufficient to resist exhaustive attacks,and the algorithm is extremely key-sensitive.The reconstruction quality of the watermarked image is up to 70 dB(PSNR).By testing several test images,the distribution of pixel points in the histogram of the cipher image is average,the correlation of neighboring pixels in each direction of the cipher is hidden,and the information is close to the ideal value of 8, and all of them pass the analysis of anti-differential attack.It also performs well in terms of encryption and decryption efficiency and computational complexity.Comparative analysis with some latest chaotic image encryption algorithms shows that this algorithm is highly practical and secure.
Therefore, this scheme is of strong research significance for practical application scenarios where there is a need to visualize decryption differences.The next work will use hierarchical encryption as inspiration for further research in two main areas.Firstly, this scheme provides decryption effects with different visual effects,and users with different visual security levels obtain the decryption results of the corresponding visual effects through the keys they hold.However,the idea of hierarchical encryption can be further developed.For example,the content in the medical image can be segmented by the semantic recognition technology, and the content with different semantics in the image can be encrypted and decrypted in a hierarchical manner to realize content-aware hierarchical encryption,and such a scheme can further enhance the application scenarios of hierarchical encryption in the field of medical treatment.Secondly, in the actual treatment process, medical 3D models are also widely used,whether we can also perform hierarchical encryption and decryption with similar effects on 3D models is also our next research direction.
Acknowledgments
Project supported by the National Natural Science Foundation of China(Grant No.62061014)and the Natural Science Foundation of Liaoning province of China (Grant No.2020-MS-274).
- Chinese Physics B的其它文章
- Unconventional photon blockade in the two-photon Jaynes–Cummings model with two-frequency cavity drivings and atom driving
- Effective dynamics for a spin-1/2 particle constrained to a curved layer with inhomogeneous thickness
- Genuine entanglement under squeezed generalized amplitude damping channels with memory
- Quantum algorithm for minimum dominating set problem with circuit design
- Protected simultaneous quantum remote state preparation scheme by weak and reversal measurements in noisy environments
- Gray code based gradient-free optimization algorithm for parameterized quantum circuit