A covert communication method based on imitating bird calls
JIANG Jiajia,LU Yin,XU Junyu,DUAN Fajie,WANG Xianquan,LIU Wei,FU Xiao
(1.State Key Lab of Precision Measuring Technology and Instruments,Tianjin University,Tianjin 300072,China; 2.Department of Electronic and Electrical Engineering,University of Sheffield,Sheffield UK)
Abstract:When radio communication is interfered with or radio silence is required,the command and intelligence cannot be transmitted among the armed squads in the forest.So there is a great need for a communication method that can replace radio communication to transmit some important information.A novel acoustic covert communication method is proposed.This method encodes the communication information by imitating animals’ calls.Taking silvereye’s call as an example,silvereye’s syllables and the time intervals between syllables are used to encode the communication information.A syllable grouping method based on time-frequency characteristics is designed to improve encoding efficiency and reduce the amount of decoding computation.Meanwhile,various strategies are used to make the encoded communication pulse sequence as similar as possible to the true silvereye’s calls to improve the covert performance.The feasibility experiments are carried out in a forest with moderate noise to demonstrate the performance of the proposed covert communication method.The power of the acoustic source is fixed at 30 watts and the communication distance varies from 20 m to 60 m.The bit-error-rate (BER) of two communication modes are 1.98% and 1.39% at 60 m,respectively.Finally,the model of communication method is introduced,and the problems that may be encountered in practical applications,as well as solutions and future development directions are analyzed.The feasibility and covert performance of the proposed method are verified in the jungle environment,and the covert information transmission can be realized when radio communication is infeasible.
Key words:imitating brid calls; acoustic covert communication; silvereye’s call; time-frequency characteristics; radio communication
0 Introduction
Due to the advantages of a high communication rate and long communication distance,radio communication has become the most commonly used wireless communication method in military applications.However,with the development of radio interference technology,the enemy can interfere with the radio through a radio interference bomb,disabling all radio devices in the area[1-4].If the radio communication among armed squad members fighting in the forest is interfered with by the enemy,it will leave them in a very dangerous situation.Therefore,when the radio cannot work effectively or radio silence is required,there is a great need for an emergency communication method.A brief message or instruction is needed at a critical moment,this communication method does not need a high communication rate,but it must be able to achieve a high degree of covertness.
Although radio communication is interfered with,the acoustic wave can still play its role in communication.Existing researches show that sound waves are also an effective information carrier and can be used for wireless covert communication in the air.Michael Hanspach et al.[5]used sound waves near the ultrasonic frequency range as the communication carrier to realize covert communication among business laptops through a multi-hop communication modulation technology,which could achieve a rate of approximately 20 bit/s and a maximal communication distance of 19.7 m.Brent Carrara et al.[6]showed that the data could be communicated by using ultrasonic carriers and a bit-error-rate (BER) of 2% at the communication distance of 11 m and communication rate of 230 bit/s was obtained.Luke Deshotels[7]used ultrasound as a carrier and the frequency shift key (FSK) encoding method for effective communication.
Covert communication is usually achieved by using ultrasonic waves which cannot be detected by the human ear,and digital modulation schemes such as FSK,amplitude shift key (ASK) and phase shift key (PSK) are generally used.The prerequisite for covert communication is based on not being recognized by the enemy.Otherwise,the communication signal will be easily interfered with or deciphered.And the existing communication signal recognition technology is mainly aimed at artificial signals (LFM,CW,etc.) encoded by traditional modulation methods (ASK,FSK,PSK,etc.)[8-11],and other signals are generally filtered as environmental noise[12-14].Therefore,the communication signal is easily discovered by communication signal recognition equipment.
A camouflage covert communication method is proposed in this paper.The communication information is encoded into the camouflaged communication signal by imitating the animal’s calls.The core is to ensure the matching degree of the camouflaged communication signal with the communication environment and the similarity with the true animal calls,to trick the enemy into filtering out these animal calls as environmental noise,and then achieve covert communication.And in order to meet the communication requirements in different situations,it is necessary to select a variety of suitable animal calls and design corresponding encoding/decoding methods for the characteristics of these calls to construct a communication carrier library.In this way,the suitable animal call can be selected as the communication carrier for covert communication according to the actual communication conditions.
It can be seen that the keys to improving covert performance are the matching degree of the camouflaged communication signal with the communication environment and the similarity with the true animal calls.So the first step is to choose an appropriate camouflage object,which is essential to the covert performance and effectiveness.After investigation and analysis,the principles of the choice of camouflage object are concluded.
1) There must be some variable characteristics in the selected calls,and these characteristics change irregularly.In this way,the communication information can be effectively encoded and the original characteristics of the call can be retained,so as to obtain great covert performance.2) The body size of the selected animal should be small,and the living environment is the same as the expected communication environment.Such a small animal is hard to be found,making it difficult for the enemy to determine its location.3) It is better to choose the animal’s call with a lower frequency.Since the lower frequency sound can propagate farther.
Given the communication environment in the forest,various animals’ calls that meet these points can be screened out,such as silvereye,willow warblers and sparrows.In this paper,silvereye’s call is chosen as an example,and the encoding/decoding method is combined based on its characteristics to introduce the design and performance of the covert communication method.
1 Encoding/decoding method for silvereye’s call
The covert communication method based on silvereye’s calls is taken as an example to introduce the encoding/decoding method adopted to ensure the similarity between the encoded communication signals and the true silvereye’s calls.
1.1 Selection and analysis of communication carrier
The silvereye is a kind of small bird with a length of about 90 mm-122 mm.They generally live in the forest and their calls could be heard 100 m away[15-16].As shown in Fig.1,each silvereye’s call segment is composed of many syllables,and there are random time intervals (TI) between adjacent call segments,which is generally 1 s to 5 s.The syllables in silvereye’s call are extracted for further observation and analysis,and the following characteristics are identified.1) The energy of silvereye’s call is concentrated in 2 kHz to 7 kHz.2) The duration of each syllable is randomly distributed between 20 ms and 300 ms.3) TI between adjacent syllables is randomly distributed between 20 ms and 150 ms.4) The number of syllables in each call segment is randomly 10 to 30.5) The time-frequency (t-f) characteristics of each syllable are complex and irregular.

Fig.1 Characteristics of silvereye’s call
Some extracted example syllables and their correlation results are shown in Fig.1.Mathematically cross-correlation and auto-correlation can be expressed as
(1)
(2)
wherep1andp2are two different syllables;Rp1p2(n) is the cross-correlation function ofp1andp2; andRp1p1(n) is the auto-correlation function ofp1.As shown in Fig.1,the auto-correlation results have sharp peaks which are much higher than the peaks of their cross-correlation results.The correlation is a prominent characteristic of the silvereye’s calls that is favorable for coding.So the silvereye’s call can meet all the requirements.Therefore,it is selected as the communication carrier,and an encoding/decoding method is designed based on its characteristics to achieve covert communication.
1.2 Construction of communication pulse database
First,a communication pulse database (CPD)is established,which is composed of silvereye’s syllables with low cross-correlation characteristics.So that the identification of the received communication pulse can be achieved by performing cross-correlation among all pulses in the CPD.However,if these syllables with low cross-correlation value are directly input into the CPD without any processing,the correlation result between the received communication pulse and hundreds of communication pulses in the CPD is calculated during the decoding process.It would have an extremely high computational complexity.More importantly,some short syllables in silvereye’s call are very similar to a part of another long syllable,resulting in a good cross-correlation between the two syllables.So the short syllable cannot be used as a communication pulse.It will greatly reduce the available communication pulses,resulting in reduced encoding efficiency.And the number of short communication pulses in CPD is small,which is different from the characteristics of a true silvereye’s call and may affect the covert performance.
A grouping method based ont-fcharacteristics is proposed.First,the syllables are divided into multiple groups according to the difference oft-fcharacteristics.And then the syllables with low cross-correlation with other syllables in the same group are selected as the candidate communication pulses.In the decoding process,thet-fcharacteristics of the received communication pulse are firstly calculated to determine its group.And then the correlation results between the received communication pulse and all communication pulses are calculated in the same group,instead of in the CPD.The pulse in the group that has a good correlation result with the received pulse is its original pulse before propagation.With this grouping method,it can greatly reduce the computational cost in the decoding process,and increase the number of silvereye’s syllables that can be used as communication pulses.
As shown in Fig.2,the process of constructing the CPD is divided into grouping and screening.During the grouping process,all syllables extracted from silvereyes’ calls are grouped according to theirt-fcharacteristics,including pulse width,frequency span and average frequency.First,thet-fcharacteristics of syllables are analyzed by short-time Fourier transform (STFT).Then the frequency component with the strongest energy is found out in each frame and outline thet-fcharacteristics for further calculation.Thet-fdiagram and its outline of one syllable are shown in Fig.2.The pulse width defined in this paper is the duration of a syllable.The frequency span is the difference between the highest frequency and the lowest frequency in the outline of thet-fdiagram.The average frequency is the average of the frequencies of each frame in the outline of thet-fdiagram.
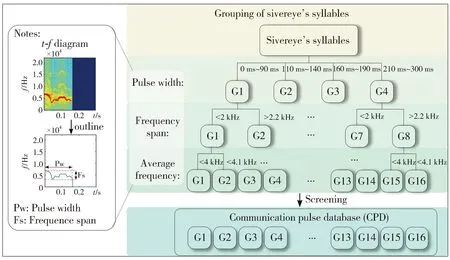
Fig.2 Construction of CPD
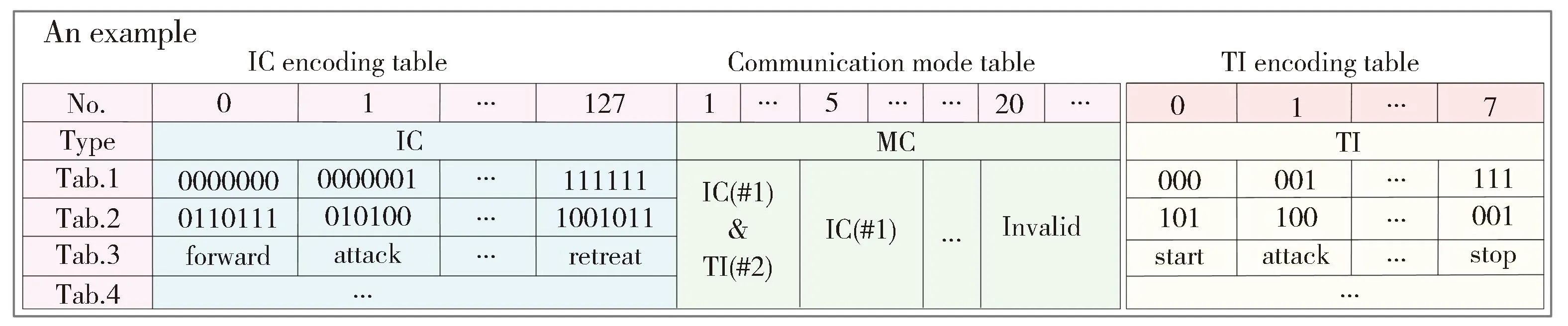
Fig.3 An example of IC encoding table,communication mode table and TI encoding table
Meanwhile,it is necessary to select an appropriate threshold to make the number of communication pulses in each group approximate.Moreover,to accurately detect the grouping of pulses during the decoding process,the thresholds of thet-fcharacteristics of each group also need to be maintained some margin.As shown in Fig.2,all syllables are divided into four groups according to the pulse width of 0 ms-90 ms,110 ms-140 ms,160 ms-190 ms and 210 ms-300 ms.Then the four groups of syllables are further divided into eight groups according to the frequency span of >2.2 kHz and <2 kHz.Finally,the eight groups of syllables are further divided into sixteen groups according to the average frequency of >4 kHz and <4.1 kHz.
During the screening process,the syllables with low cross-correlation with other syllables in the same group are selected as communication pulses to construct the CPD for each pulse group in the CPD.The syllables selected as communication pulses have high auto-correlation and low cross-correlation.For every pulse selected in the CPD,the peak of the auto-correlation result is at least three times larger than the peak of the cross-correlation results between themselves and other syllables in the same group.
1.3 Encoding method
Thet-fcharacteristics of the selected pulses are unique,which can be demonstrated by correlation results.Likewise,the distribution of TIs among the true silvereye’s call pulses is diversiform.In this section,the encoding method based on information code (IC) and TI will be introduced in detail.The encoding process is shown in Fig.4.
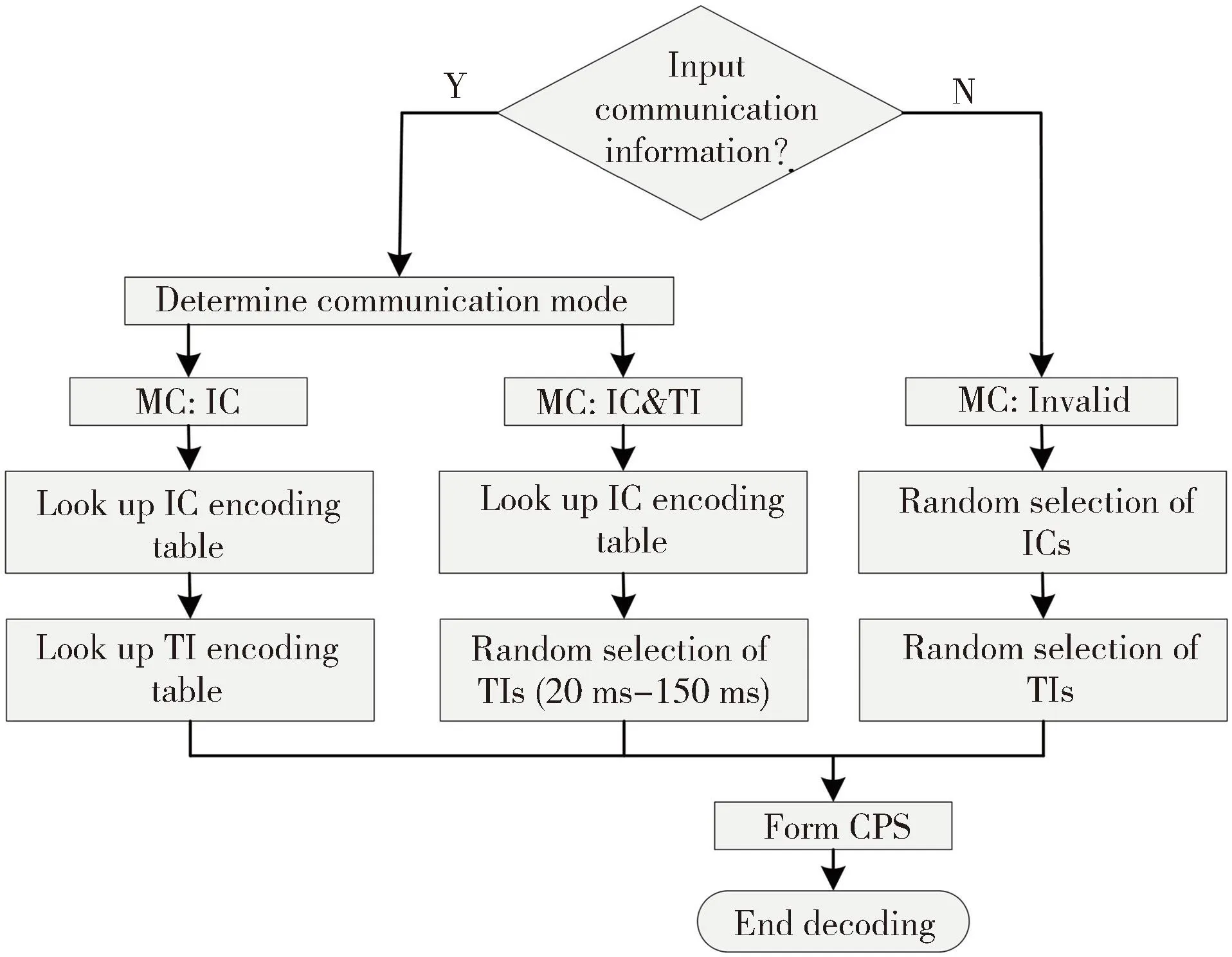
Fig.4 Encoding process
Since each communication pulse in the CPD has unique characteristics,its index number can be defined by grouping method and correlation results,which is the unique identifier of this pulse.In this way,each communication pulse can be used as a communication carrier to encode specific communication information,which is called IC encoding.To ensure the similarity between the encoded communication pulse signal (CPS) and the real silvereye’s call,each IC only consists of one single original silvereye’s call pulse.Before communication,the index number of ICs and the information represented by each IC must be determined in the IC encoding table as shown in Fig.3.The encoding process based on IC can be summarized as follows.First,assuming that each pulse can encodenbits of information,2ncommunication pulses are randomly selected from the CPD as the ICs (the number of communication pulses in the CPD is larger than 2n).Then,their index number (0,2n-1) and the information represented are determined.The information can be varied by changing different IC encoding tables.For example,the information could ben-bit binary data,which is numerically equal to the index number of the IC.Assuming thatn=7,the information represented by IC No.125 is ‘1111101’,the information represented by IC No.58 is ‘0111010’,and so on.The communication information could also be irregularn-bit data or specific instructions such as “forward” and “retreat” according to different IC encoding tables.
In this paper,the TI is defined as the time difference between the end of the previous call pulse and the beginning of the next call pulse.since TIs among adjacent communication pulses are variable and irregular,they can also be used to encode communication information,which is called TI encoding.Similarly,before communication,the index number of TIs and the information represented by each TI must be determined in the TI encoding tables as in the example shown in Fig.3.The encoding process based on TI can be summarized as follows.Firstly,the maximum TI(Tmax) and the minimum TI(Tmin) are determined according to the TI distribution rule in silvereye’s call.Assuming that each TI is used to encodem-bit data,then the time rangeTmin-Tmaxis divided into 2msections of equal length to get 2mtime range.Then,the index number (0,2m-1) of each TI range is determined,which is the unique identifier of TI range.And the information represented by TI range can be varied by changing different TI encoding tables.For example,the information represented can bem-bit binary data,which is numerically equal to the serial number.Of course,the information could also be irregularm-bit binary data or specific instructions such as “start” and “attack” according to different TI encoding tables.
Different encoding methods are proposed based on IC or TI.Considering that when only TI encoding is used,the range of TI will limit the choice ofm,which causes a low communication rate.However,IC and TI can be combined for encoding.For this reason,two encoding methods are determined based on IC only or IC &TI.It is worth mentioning that when only IC encoding is used,the distribution of TI in the encoded CPS is the same as that in true silvereye’s call,which ensures the communication signal has a better covert performance.If IC encoding and TI encoding are both used,the communication rate can be greatly increased.Meanwhile,TI in the encoded CPS is discretely distributed for encoding,which may affect the covert performance of the communication signal.Therefore,in the communication process,the encoding method should be determined according to the requirements of the communication rate and the covert performance.And multiple encoding tables should be switched in time according to the communication requirements.It will greatly increase the difficulty for the enemy to decipher the communication information and further ensure the security of communication.
According to the requirement,each communication frame needs to contain the information of the encoding method and encoding table used in this frame.Mode code (MC) is used as the frame header of the communication frame to indicate the encoding method and encoding table used in the communication frame.Therefore,it is necessary to design a communication mode table as in the example shown in Fig.3 before communication.First,Zcommunication pulses that are not used as IC are randomly selected from the CPD as MCs (index numbers are 1-Z),and the communication modes represented by each MC are determined.For example,assuming that the frame header is MC #5,it means that IC encoding with IC encoding Table 1 abbreviated as IC(#1) is used in this frame.And if the frame header is MC #1,it means that IC(#1) and TI(#2) are used in this frame.Noting that if a communication mode is used for a long time,the MC used as the frame header may always be the same,which may be exposed.Therefore,multiple MCs are used to represent the same communication mode to avoid the issue,which further guarantees the covertness of communication.In addition,the mode of invalid communication frames can be added.In this way,when there is no need for communication,the communication transmitter also transmits sound signals by imitating silvereye’s call,further imitating the sound in a real environment.
Each silvereye’s call segment contains 10-30 call syllables,and the time interval between adjacent call segments is 1 s-5 s.So a silvereye’s call segment can be regarded as a communication frame,and the time interval between adjacent communication frames is randomly distributed within 1 s-5 s.The structure of the communication frame after encoding is shown in Fig.5.

Fig.5 Structure of a communication frame
The frame header is MC,followed by several ICs (IC1-ICk),and the TIs between adjacent communication pulses are TI1-TIk.The process of constructing a communication frame is concluded as follows.First,the communication mode used in this communication frame is determined,and the corresponding MC is selected as the frame header.Then the information is encoded into a CPS by looking up the IC encoding table and the TI encoding table.For example,when the communication mode is IC(#2),the corresponding MC is inserted as the frame header,then IC encoding Table 2 is looked up to determine the corresponding ICs.Finally,these ICs are sequentially inserted to form a CPS,and the TIs:TI1,TI2,TI3,… among adjacent pulses are randomly distributed between 20 ms-150 ms.When the communication mode is IC(#1) &TI(#2),the corresponding MC is inserted as the frame header,then IC encoding Table 1 and TI encoding Table 2 are looked up to determine TI1,IC1,TI2,IC2,TI3,IC3,… Then the corresponding ICs are inserted at the corresponding TIs in the above order to form a CPS.When the communication mode is an invalid communication frame,the corresponding MC is first inserted as the frame header,and then ICs is randomly inserted to form a CPS.In addition,the number of ICs in a communication frame should be between 10 and 30.
1.4 Decoding method
Due to channel fading and multipath,spatial diversity and spectral subtraction filtering techniques[17-19]are adopted to process the received signal to improve the decoding performance.
The proposed covert communication method is to encode communication information by ICs and TIs among adjacent pulses.Therefore,in simple terms,the decoding process is actually to determine the index number of received ICs and TIs among adjacent pulses.And then the encoding table used in the encoding process is looked up to determine its corresponding communication information.
The process of decoding is summarized and shown in Fig.6.First,the short-term energy spectrum[20]of the CPS after filtering and equalization is calculated to distinguish communication pulses from TIs.The short-term energy spectrum can be expressed as
(3)
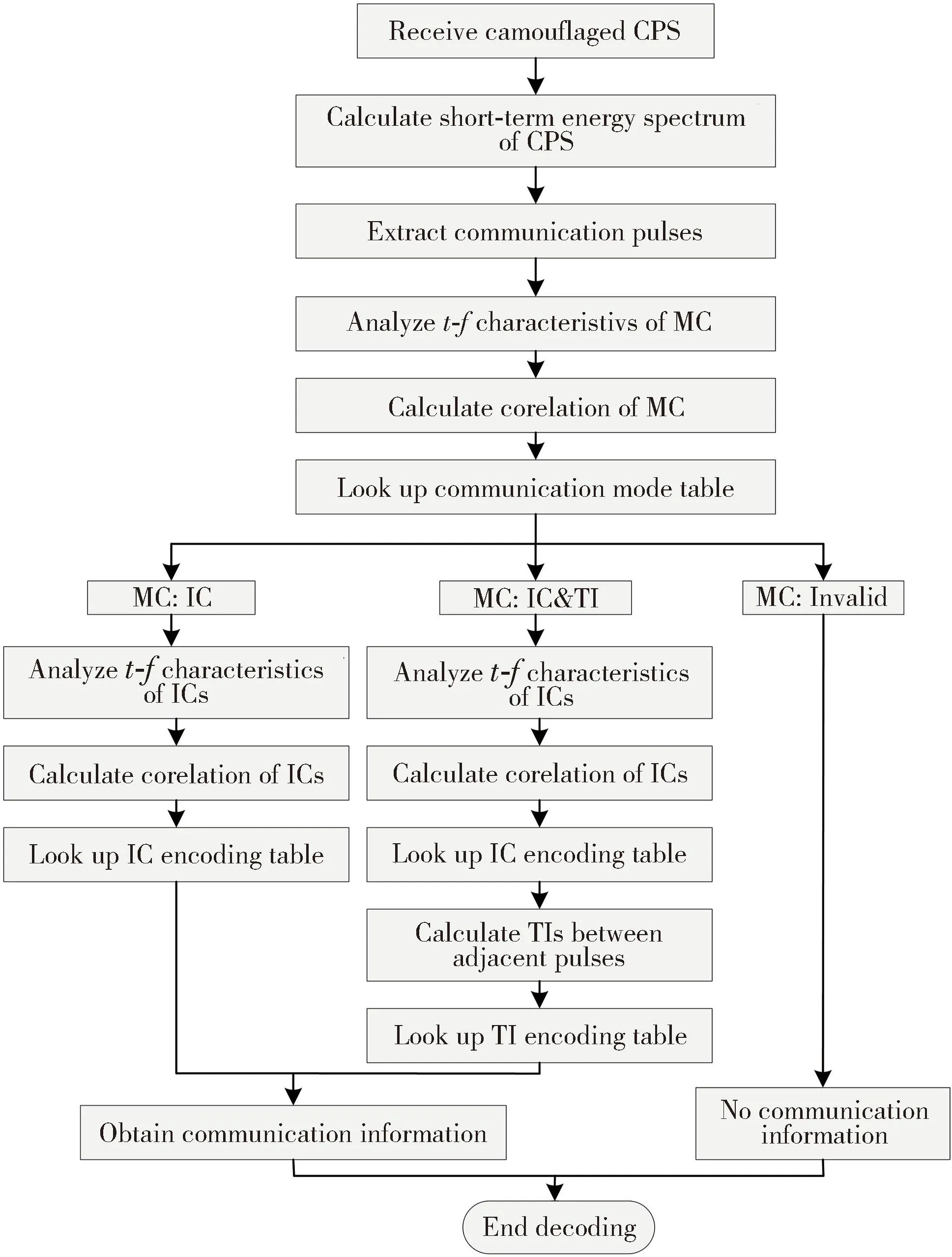
Fig.6 Decoding process

2 Experiment
Experiments are carried out to verify the feasibility and covert performance of the proposed covert communication method.
2.1 Feasibility of communication
The communication bit-error-rate(BER) is tested first through a series of experiments conducted in a forest,where the loudspeaker (Alpha 3-8) is used as the acoustic source,and the microphone is used as the receiver.The experiment is conducted in the forest with a moderate density of trees,covering an area of about 100 m×150 m,and the height of the trees is about 8 m.The model and environment of forest experiment is shown in Fig.7.

Fig.7 Experiment model and environment
Communication interference is mainly caused by natural noise and channel fading effect.In the experiment,the natural sound of the experimental environment is about 43 dB-50 dB,including sounds of wind,bird calls and traffic.The effect of channel fading is analyzed by changing the communication distance.In addition,nin the IC encoding is set to 7,andmin the TI encoding is set to 3.The power of the acoustic source is fixed at 30 watts and the communication distance varied from 20 m-60 m by changing the position of the microphone.In the experiment,the amount of communication data at each communication distance is 10 000 bit.The BER results at different communication distances of two communication modes,one with both IC encoding and TI encoding and one with IC encoding only,are shown in Fig.8.At the communication distance of 60 m,the amplitude range of the received signal is 0.03 V-0.2 V and the signal-to-noise ratio is about 10 dB.Under such experimental conditions,the BER of two communication modes are 1.98% and 1.39%,respectively.The BER increases significantly with the increase of communication distance.The communication method based on IC has better performance in accuracy than that based on IC &TI.

Fig.8 BER at different distances
Since the communication method encodes information with ICs and TIs,and the pulse width of IC and the length of TI are related to the communication information,the communication rate of the method cannot be calculated accurately.In the experiment,the average communication rate is 43 bits/s when the communication is based on IC &TI,and the average communication rate is about 30 bits/s when the communication is based on IC only.
2.2 Analysis and testing of covert performance
The key to realizing the camouflage covert communication method is that the communication signal cannot be discovered by the enemy.And its core is to ensure the matching degree of the camouflaged communication signal with the communication environment and the similarity with the true animal calls.
First of all,the theoretical analysis and evaluation of the similarity between the camouflaged communication signal and the real silvereye’s calls are carried out,which is essential to evaluate the covert performance of the camouflaged communication.Based on the encoding principle of the covert communication method,the theoretical analysis of the similarity can be carried out in terms of both individual communication code element pulses and the encoded CPS.The similarity between individual communication pulses and real call’s syllables is analyzed first.According to the coding method,the pulses used for covert communication are extracted from the real silvereye’s calls without any modification.That is,any pulse in the CPS is identical to its corresponding syllable of the silvereye’s calls.Then the similarity between the encoded CPS and the call string of silvereyes is analyzed.
In the encoded CPS,the features such as the range of the length of the TIs,the range of the number of pulses in the communication frame and the structure of the CPS are determined exactly according to the features of the silvereye’s calls,which is consistent with the real calls.In the IC-based coding method,the TIs between pulses are consistent with those of the real calls,while the combination situation and arrangement order of the communication pulses depend on the communication content and coding table,which will be different from that of the original call sample.In the IC &TI-based coding method,both the combination of communication pulses and the TI distribution of the CPS are different from those of the original silvereye’s calls.
According to the analysis of real silvereye’s calls,there is no significant pattern of syllable combination and TI distribution,and there are regional and individual differences in the calls of Silvereyes,which means that the syllable combination and TI distribution of the calls are variable.Therefore,it is theoretically difficult to distinguish the encoded CPS from the real silvereye’s calls by the combination and arrangement of syllables and their TIs.The analysis of communication pulse and the CPS shows that the covert communication method uses original call syllables as communication code elements and follows the characteristics of the silvereye’s calls as much as possible.Therefore,the camouflaged communication signal has a high similarity with real silvereye’s calls in theory.In addition,since the CPS with IC encoding does not modify the TIs of the syllables,its camouflage effect is better than that of the CPS with IC &TI encoding.
To further test whether the camouflaged communication signal will be recognized as a communication signal,a signal classification system based on a neural network is designed based on the existing communication signal classification technology.First,a fifth-order polynomial is used to fit the ridge of thet-fdiagram of the traditional communication pulse (LFM,CW) and silvereye’s syllables.The coefficients and residual error of the polynomial are used as feature parameters to train the classifier.Then the communication pulse (LFM,CW) extracted from the received traditional communication signal is used as input to test the effectiveness of the classifier.Then the communication pulse extracted from the received camouflaged communication signal is used as an input to test whether the camouflaged communication signal will be classified as a traditional communication signal.
In the test results,the classification accuracy rates of LFM and CW communication pulses are 98% and 98.5%,respectively,which proves that the classifier is effective.And only 0.5% of the camouflaged communication pulses are classified as traditional communication pulses,which proves that the camouflaged communication signals are obviously different from the traditional communication signals and will not be recognized as communication signals.
In addition,the camouflaged communication signal can be perceived by humans,so it is also very important to test people’s judgment on the camouflaged communication signal.Participants from various backgrounds (teacher,doctor,veteran,etc.)are invited to conduct tests through online surveys.First,the encoded CPS and true silvereye’s call are played to theme.Then they are asked two questions.(1) Are these two sounds the same animal’s call,or is there a clear difference between them? (2) One of the two sounds contains communication information,which one do you think? Finally,286 valid results are received,and 98.3% of them say that the two sounds are the same animal sound,no difference.The rest of the people say that they do not know what the animal’s voice is and can not decide.For the second question,54.7% of them think that the first sound contains communication information,while the remaining thinks otherwise.In fact,the first sound is silvereye’s call,and the second sound is the encoded CPS.Based on the experimental results,it can be concluded that it is very difficult for the human ears to distinguish between the two sounds,which demonstrates that the proposed bio-inspired communication method has a strong covert performance.
3 Discussion
The bio-inspired covert communication method based on silvereye’s call is taken as an example to introduce the corresponding encoding and decoding method,and the feasibility of the covert communication method is verified through point-to-point communication tests.But there are still some problems to be solved in the actual communication environment.
As shown in Fig.9,in the actual communication model,there are communication transmitter (A),communication receiver (B) and enemy (C),as well as other interferers (D) (animal calls in the environment,etc.).A needs to transmit information to B by using animal calls as communication carriers under C’s recognition,interference,intercept and D’s interference.
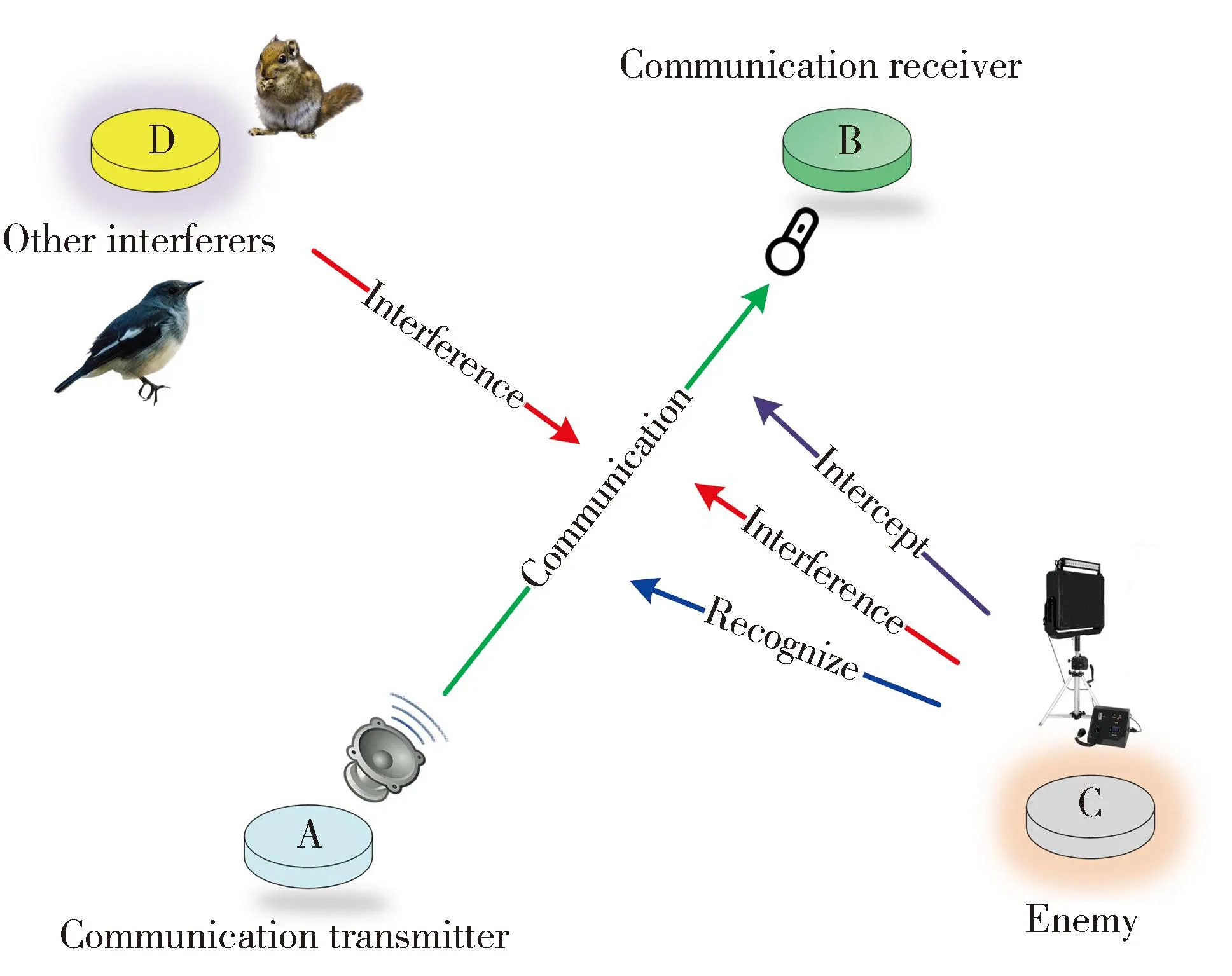
Fig.9 Communication model
First of all,even if C received communication signals disguised as silvereye’s calls,as long as the camouflaged communication signal is sufficiently similar to the true silvereye’s calls,it will also be difficult for C to recognize it,let alone deciphering.In general,C will only ignore camouflaged communications as background noise.What’s more,C can only interfere with the communication by continuously sending interference signals.But audible sound waves are different from the radio.They are perceivable by the human body.If C continuously sends high-power audible sound,it will not only expose its position but also may cause permanent damage to the hearing of C’s members and surrounding animals.So judging from the current technology,the proposed covert communication method is difficult to interfere with.
D refers to other interferers in the environment,such as natural animal calls.If these sounds overlap the frequency range of the communication signal,it may interfere with the communication between A and B.It is similar to the bandwidth conflict in traditional communication.At this time,other suitable animals that do not exist in the environment temporarily can be selected as camouflage objects.And it is necessary to select the camouflaged object according to the actual situation to ensure the matching degree between the camouflaged communication signal and the communication environment.That is,the camouflage covert communication method based on specific animals is not universal.Therefore,it needs to design covert communication methods based on different animals’ calls,so that an animal call that does not conflict with environmental sounds can be selected as the communication carrier in actual communication.And it is also necessary to design more effective encoding methods to increase the communication rate.
In fact,the covert communication method based on insects’ calls has already been done before,and the covert communication methods is being designed based on other animals’ calls.It is hoped that a rich communication carrier library can be established to meet the demand for covert communication in different environments and different situations as much as possible.
4 Conclusions
For effective communication when radio communication is not feasible,a bio-inspired covert communication method by imitating animals’ calls is proposed.And the covert communication method based on silvereye’s call is used as an example to introduce this novel covert communication method.Based on the strategy of camouflage,the true silvereye’s syllables are extracted as the communication pulses,and these pulses and TIs between adjacent communication pulses are used to encode information.Meanwhile,various strategies are employed to ensure the similarity between the encoded CPS and the silvereye’s calls.In this way,it is difficult for the enemy to distinguish the encoded CPS from true silvereye’s calls.Experimental results shows that the BER of this communication method at a distance of 60 m is less than 2%.Therefore it provides a novel and effective solution to solve the covert communication problem when radio communication is infeasible.The proposed approach is not limited to forests but can also be applied to other similar areas requiring covert communication.And there are still some problems to be solved in the actual communication environment.In the following research,it is necessary to design more encoding/decoding methods based on other animals’ calls to improve the performance of covert communication.
 Journal of Measurement Science and Instrumentation2023年4期
Journal of Measurement Science and Instrumentation2023年4期
- Journal of Measurement Science and Instrumentation的其它文章
- A synchronous scanning measurement method for resistive sensor arrays based on Hilbert-Huang transform
- Remote sensing images change detection based on PCA information entropy feature fusion
- An image dehazing method combining adaptive dual transmissions and scene depth variation
- Research on restraint of human arm tremor by ball-type dynamic vibration absorber
- Drive structure and path tracking strategy of omnidirectional AGV
- Electro-hydraulic servo force loading control based on improved nonlinear active disturbance rejection control
